Category: HelpnetSecurity
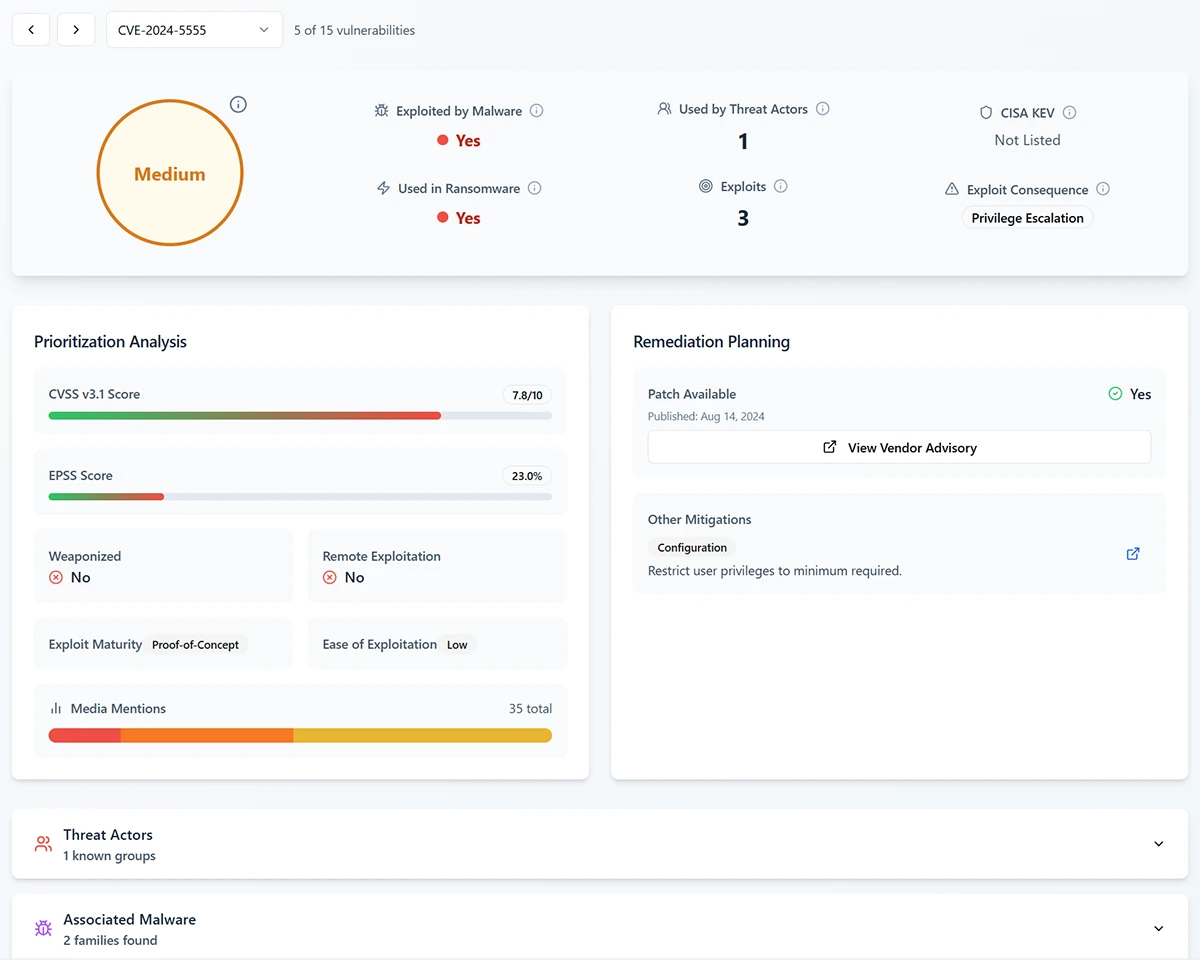
CISOs are dealing with an overload of vulnerability data. Each year brings tens of thousands of new CVEs, yet only…
Salesforce has become a major target for attackers in 2025, according to new WithSecure research into threats affecting customer relationship…
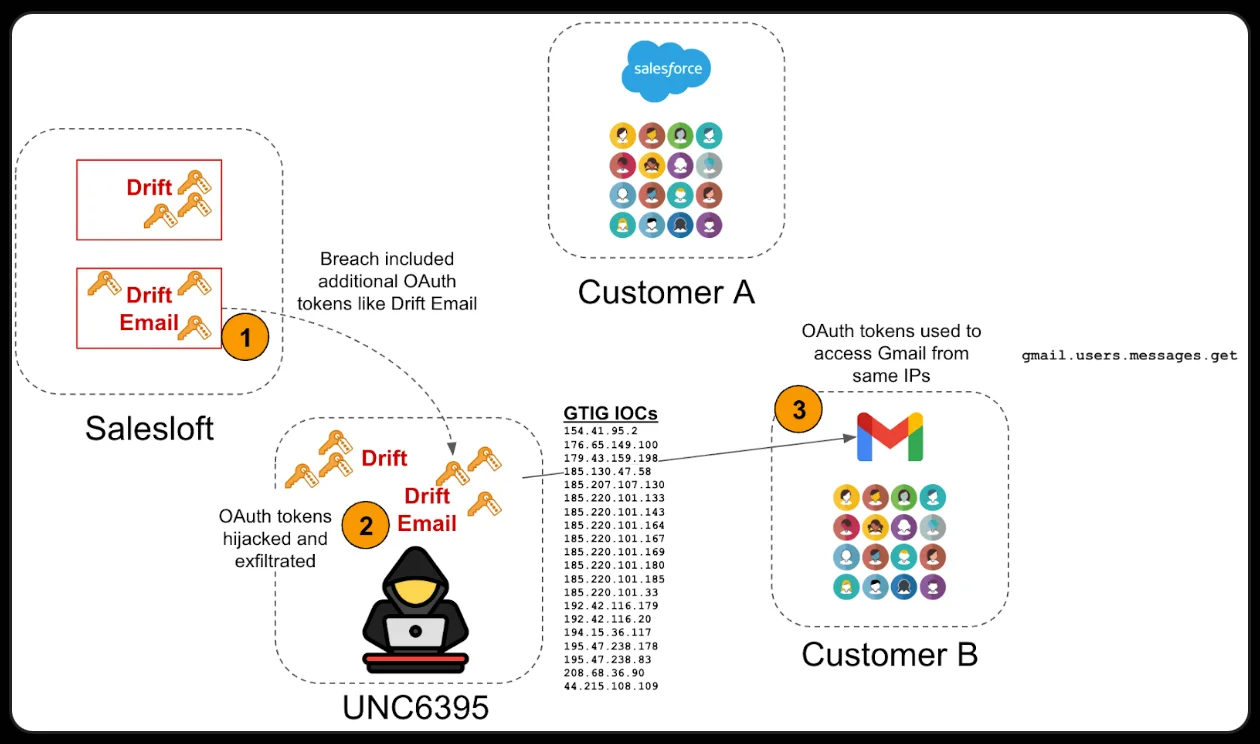
Cloudflare has also been affected by the Salesloft Drift breach, the US web infrastructure and security company confirmed on Tuesday,…
BruteForceAI is a penetration testing tool that uses LLMs to improve the way brute-force attacks are carried out. Instead of…
Many people might not think that playing video games could help build a career in cybersecurity. Yet the skills gained…
In today’s complex threat environment, the challenge for security professionals isn’t just defeating threats – it’s finding your vulnerabilities in…
AI is moving into security operations, but CISOs are approaching it with a mix of optimism and realism. A new…
Varonis Systems acquired SlashNext, an AI-native email security provider. Their predictive AI sees through evasive tactics, removes threats from the…
In the wake of last week’s revelation of a breach at Salesloft by a group tracked by Google as UNC6395,…
A new research project called NetMoniAI shows how AI agents might reshape network monitoring and security. Developed by a team…
Identity has become a core pillar of cybersecurity strategy. Remote work, cloud-first adoption, and distributed supply chains have moved identity…
CISO Shift Technology | France | Remote – View job details As a CISO, you will develop and execute a…