Category: HelpnetSecurity
ESET researchers have discovered a previously unknown vulnerability in WinRAR, exploited in the wild by Russia-aligned group RomCom. If you…
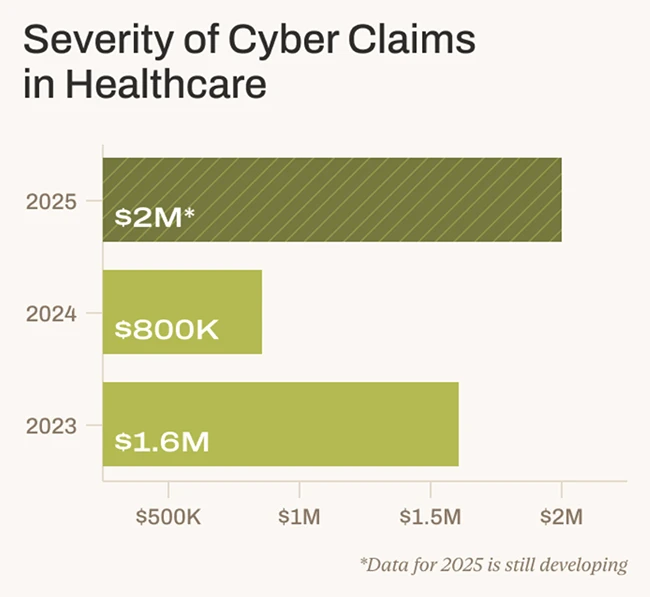
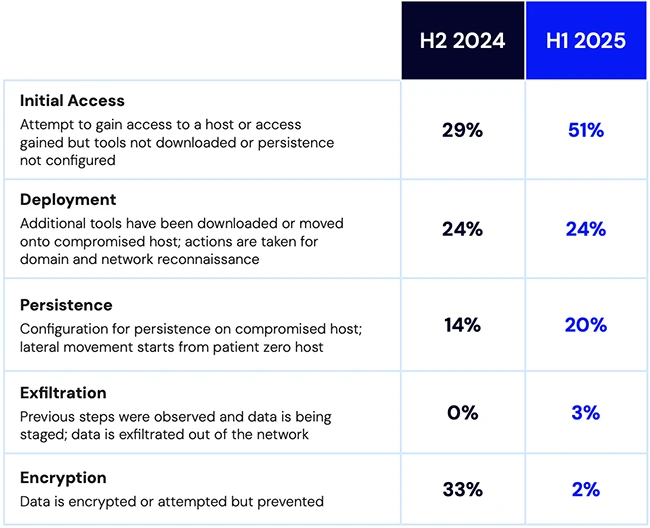
A new report from Resilience outlines a growing cyber crisis in the U.S. healthcare sector, where ransomware attacks, vendor compromise,…
From Day Zero to Zero Day is a practical guide for cybersecurity pros who want to move beyond reading about…
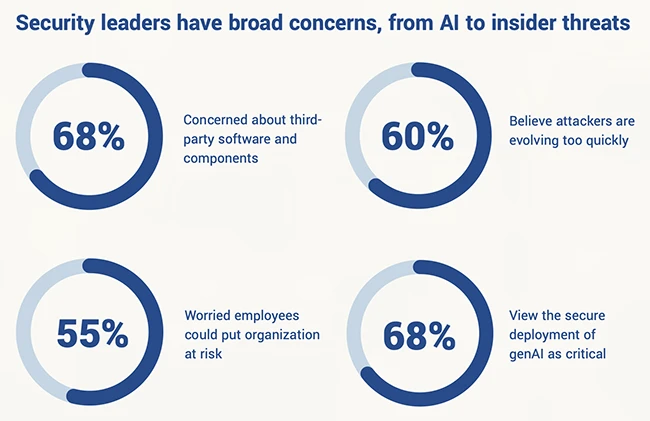
Security leaders are rethinking their approach to cybersecurity as digital supply chains expand and generative AI becomes embedded in critical…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Black Hat USA 2025Black Hat…
July turned into a surprisingly busy month. It started slowly with a fairly ‘calm’ Patch Tuesday as I forecasted in…
Over a third of companies say they are using AI, including generative AI, to fight fraud, according to Experian. As…
Cybercriminals are getting better at lying. That’s the takeaway from a new LevelBlue report, which outlines how attackers are using…
Here’s a look at the most interesting products from the past week, featuring releases from Black Kite, Descope, Elastic, ExtraHop,…
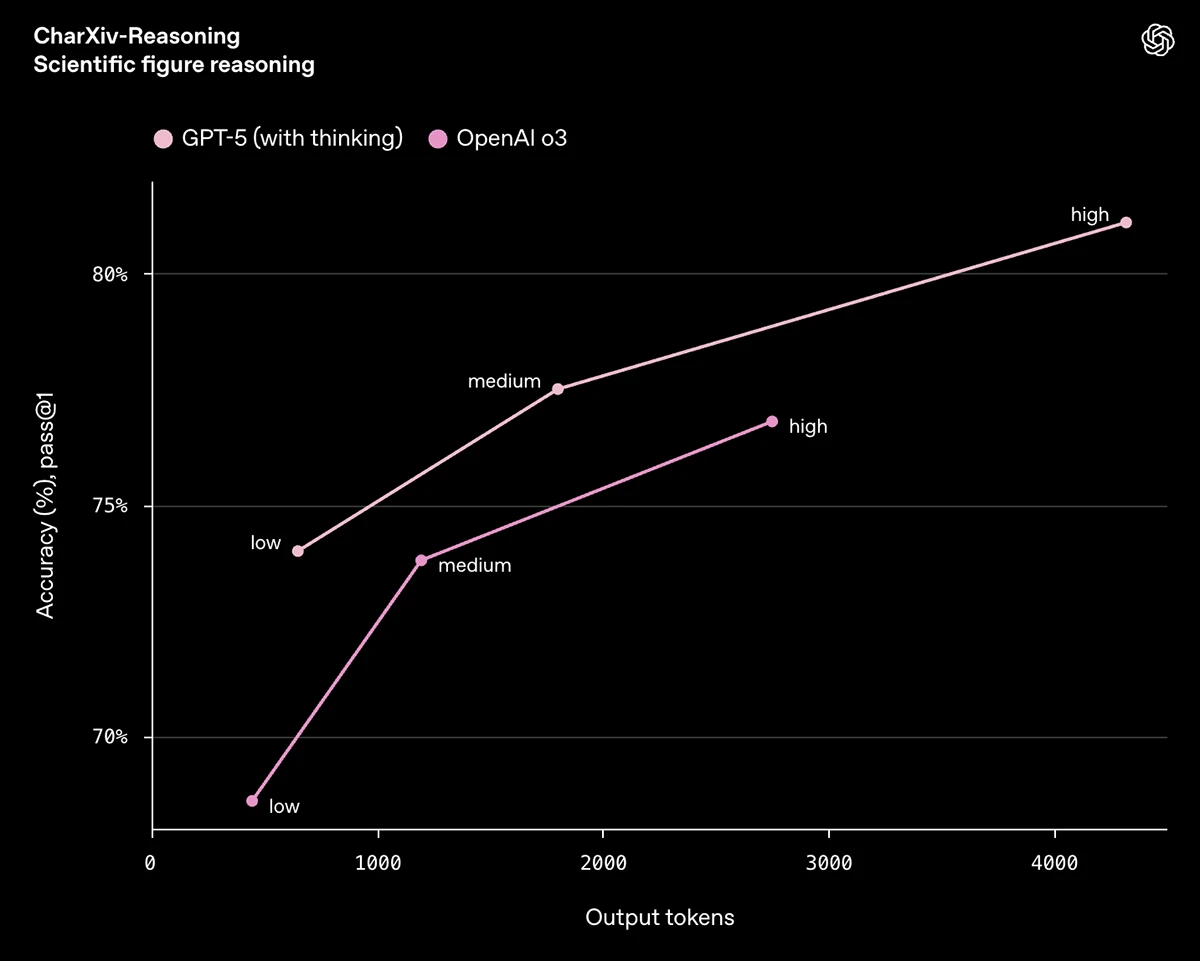
OpenAI has released GPT‑5, the newest version of its large language model. It’s now available to developers and ChatGPT users,…
“In an Exchange hybrid deployment, an attacker who first gains administrative access to an on-premises Exchange server could potentially escalate…
Akira ransomware affiliates are not leveraging an unknown, zero-day vulnerability in SonicWall Gen 7 firewalls to breach corporate networks, the…