Category: HelpnetSecurity
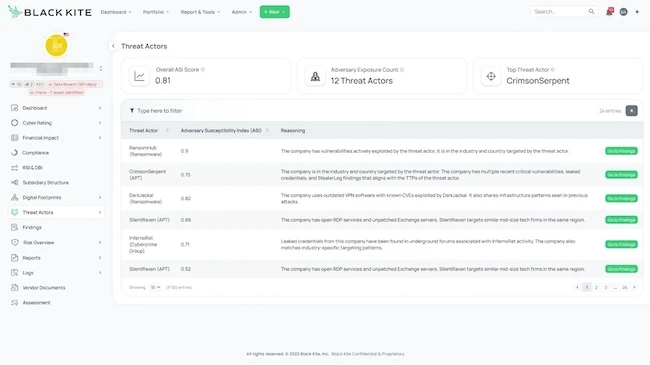
Black Kite has unveiled the Adversary Susceptibility Index (ASI), a tool designed for TPRM teams to proactively identify which vendors…
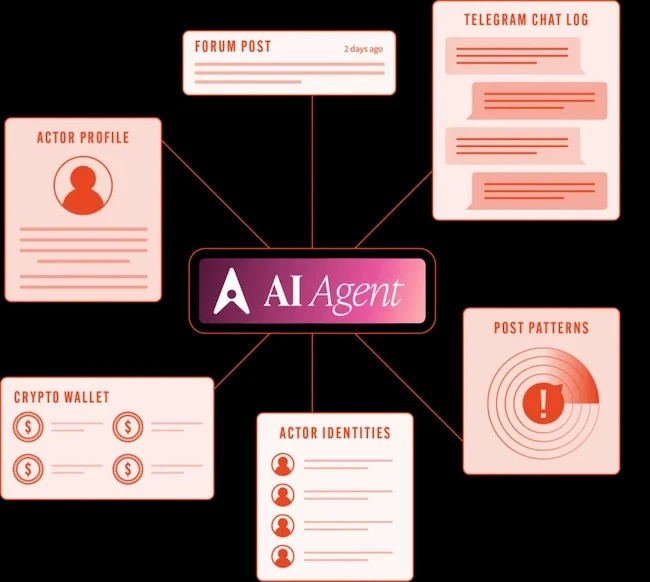
Searchlight Cyber has released a new AI capability that summarizes the activity of a threat actor in its dark web…
Cyber attackers are finding new ways in through the overlooked and unconventional network corners. Forescout’s 2025H1 Threat Review reveals a…
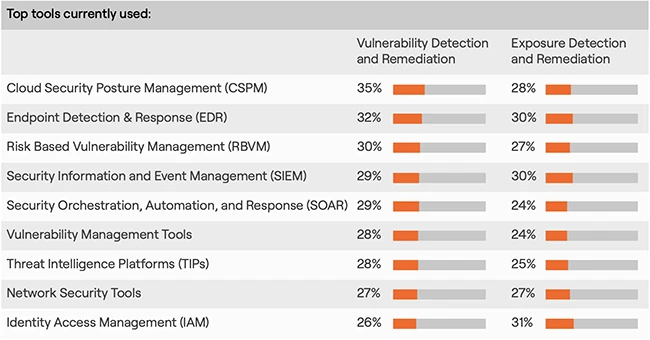
Most security teams believe they can act quickly when a threat emerges. But many don’t trust the very data they…
90% of cyber leaders find managing cyber risks harder today than five years ago, mainly due to the explosion of…
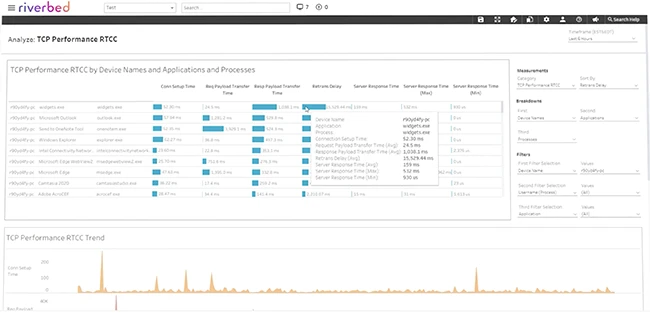
Riverbed launched its new AI-powered intelligent network observability solutions, enhancing network visibility for enterprise IT teams and enabling them to…
A set of firmware vulnerabilities affecting 100+ Dell laptop models widely used in government settings and by the cybersecurity industry…
Manifest Cyber introduced Manifest AI Risk, the latest module part of the Manifest Platform, designed to help security and compliance…
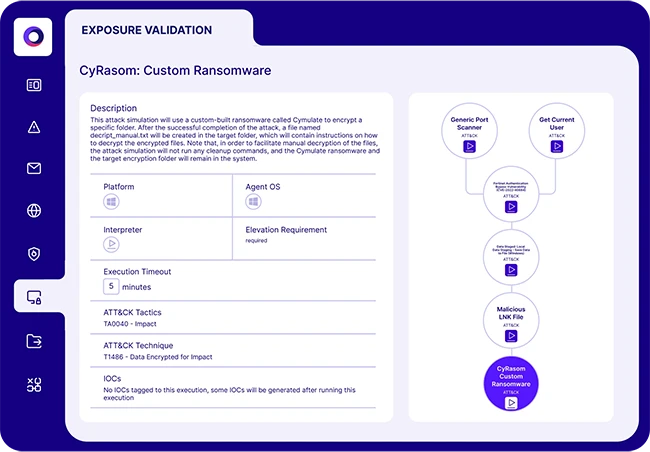
Cymulate announced the new Cymulate Exposure Management Platform, which validates, prioritizes and optimizes the entire security ecosystem – continuously. The…
Microsoft is working on a AI agent whose main goal is autonomous malware detection and the prototype – dubbed Project…
ExtraHop unveiled new innovations to accelerate incident response, offering an understanding of cyberattacks by linking disparate detections to compromised identities….
Reveal Security released the Reveal Platform, a solution to deliver preemptive identity security across SaaS, cloud, and custom applications. Designed…