Category: HelpnetSecurity
In this Help Net Security interview, Seth Ruden, Senior Director of Global Advisory at BioCatch, discusses how financial institutions are…
As the space sector becomes more commercial and military-focused, these assets are becoming attractive targets. The global space economy is…
Despite knowing the risks, most organizations are still shipping insecure software. That’s one of the stark findings from Cypress Data…
For all the excitement around LLMs, practical, engineering-focused guidance remains surprisingly hard to find. LLM Engineer’s Handbook aims to fill…
In this Help Net Security interview, Gonçalo Magalhães, Head of Security at Immunefi, discusses the legal and ethical implications of…
Vulnhuntr is an open-source tool that finds remotely exploitable vulnerabilities. It uses LLMs and static code analysis to trace how…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft pins on-prem SharePoint attacks…
It’s been six months since the EU’s Digital Operational Resilience Act (DORA) came into effect, but a new Censuswide survey…
In this Help Net Security interview, Benjamin Schilz, CEO of Wire, discusses Europe’s push for digital sovereignty through initiatives like…
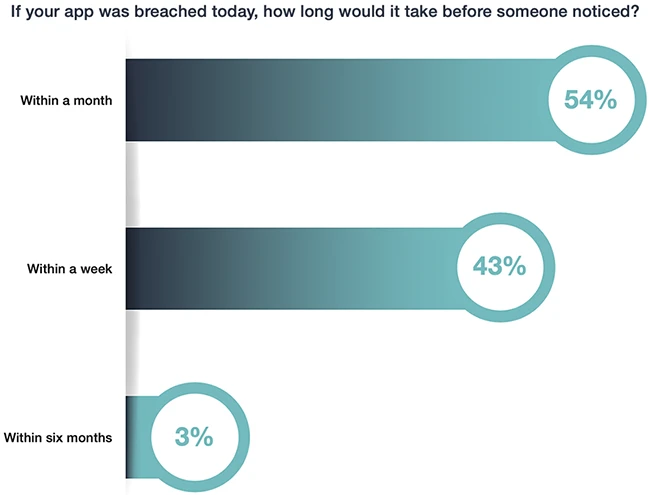
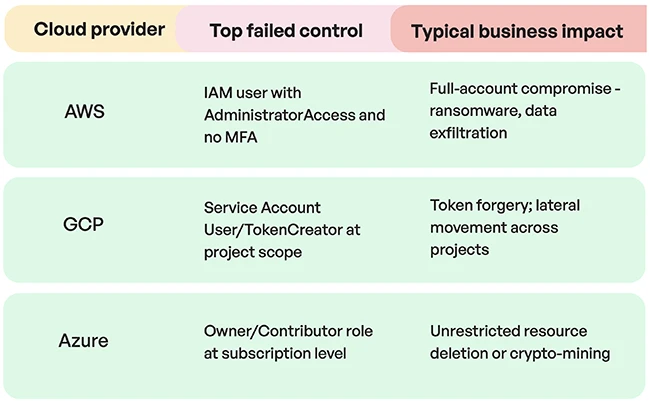
Most organizations still miss basic identity security controls in the cloud, leaving them exposed to breaches, audit failures, and compliance…
Here’s a look at the most interesting products from the past week, featuring releases from Akeyless, Bitdefender, Malwarebytes, ManageEngine, PlexTrac,…
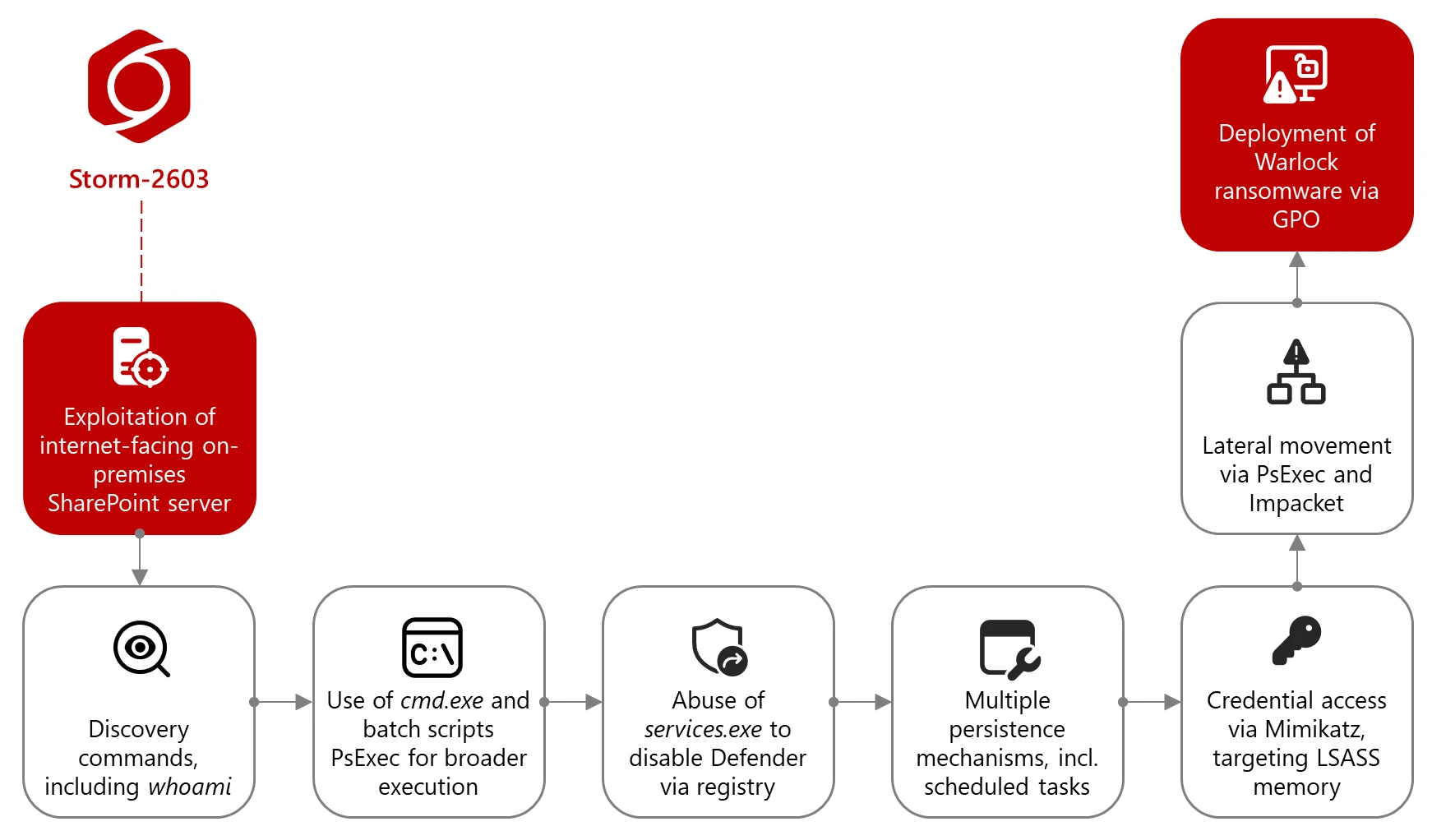
One of the groups that, in the past few weeks, has been exploiting vulnerabilities in on-prem SharePoint installation has been…