Category: HelpnetSecurity
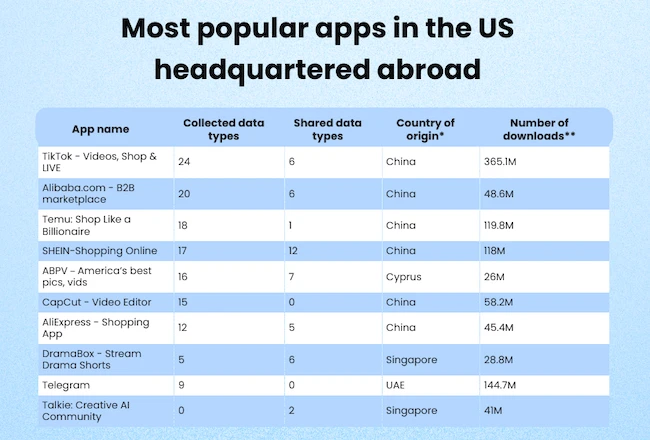
Both domestic and foreign technology companies collect vast amounts of Americans’ personal data through mobile applications, according to Incogni. Some…
Three new vulnerabilities affecting (Citrix) NetScaler application delivery controller (ADC) and Gateway devices have been made public, one of which…
CVE-2025-48384, a recently patched vulnerability in the popular distributed revision control system Git, is being exploited by attackers. Details about…
Agriculture is a connected, software-driven industry where cybersecurity is just as essential as tractors and harvesters. From embedded hardware in…
The energy sector remains a major target for cybercriminals. Beyond disrupting daily routines, a power outage can undermine economic stability…
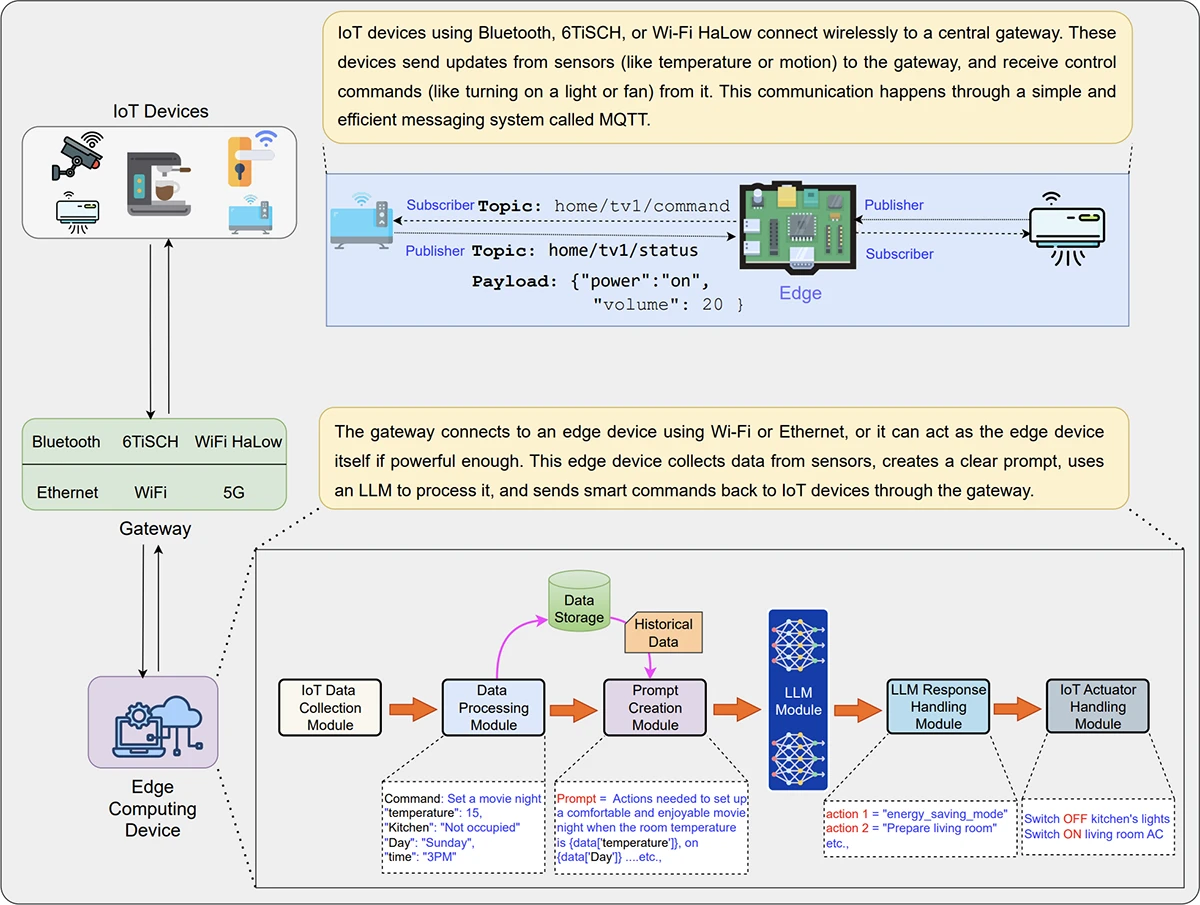
Anyone who has set up a smart home knows the routine: one app to dim the lights, another to adjust…
Sr. Cybersecurity Analyst Aecon Group Inc. | USA | On-site – View job details As a Sr. Cybersecurity Analyst, you…
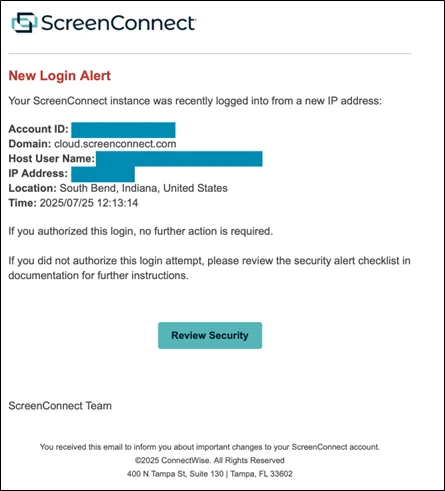
ScreenConnect cloud administrators across all region and industries are being targeted with fake email alerts warning about a potentially suspicious…
Cloudflare announced new capabilities for Cloudflare One, its zero trust platform, designed to help organizations securely adopt, build and deploy…
Criminals are taking advantage of macOS users’ need to resolve technical issues to get them to infect their machines with…
The manufacturing sector is entering a new phase of digital transformation. According to Rockwell Automation’s 10th Annual State of Smart…
Satellites play a huge role in our daily lives, supporting everything from global communications to navigation, business, and national security….