Category: Mix
Bringing clarity to questions about Prompt Injection Security Everyone loves talking about prompt injection, but the real impact to an…
We recently discussed the new SEC rule requiring all registered companies to report material cyber incidents within four (4) days….
I hope you’ve been doing well! What We’re Known For It’s long had a place in my heart, as I…
I think AI is about to massively improve the quality of our best content. But not for the reason you…
The debate was quite fun to watch, but also frustrating. What irked me about the debate—and all similar debates—is that…
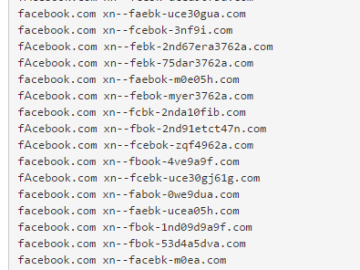
So we’re seeing homograph attacks again. Examples show how ‘apple.com’ and ‘epic.com’ can be mimicked by the use of Internationalized…
While researching a web application last February, I learned about Slanger, an open source server implementation of Pusher. In this…
Bug Bytes is a weekly newsletter curated by members of the bug bounty community. The second series is curated by…
Download my transcription of Bill Evans’ piano solo in I’ve Got You Under My Skin below. The solo starts around…
When performing security tests, you will often be required to send all of your traffic through a VPN. If you…
In this write-up, I want to share a cool way in which I was able to bypass firewall limitations that…
Last May, I discovered that a critical vulnerability I had reported earlier this year had resulted in my first CVE….


![[tl;dr sec] #196 – How Secrets Leak in CI/CD, AI Threat Modeling, Supply Chain [tl;dr sec] #196 - How Secrets Leak in CI/CD, AI Threat Modeling, Supply Chain](https://cdn.cybernoz.com/wp-content/uploads/2023/08/tldr-sec-196-How-Secrets-Leak-in-CICD-AI-360x270.jpg)