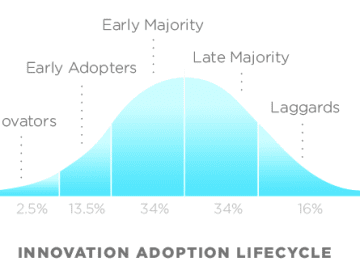
Category: Mix
Hunting IDOR with Z-winK (Part 2) Source link
How to get greater bounties for MEDIUM and LOW risk reports? Account takeover – Stripe Source link
Alternatively titled, “Why the Internet Protocol Suite is an imaginary rainbow layer cake” A significant part of the process of…
Note that during these interviews I also moderate thus quality may vary. Profile 🐝 Got into hacking in middleschool Cicumventing…
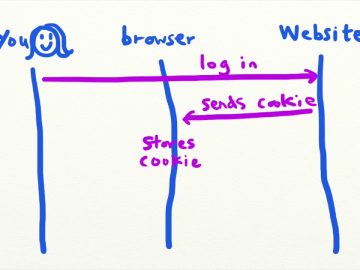
Intro to CSRF (Cross-Site Request Forgery) – Security Simplified Source link
Yorkshire Post Building Demolition #5 Source link
The Iceberg Of Network Exploits [Parody] Source link
Expedia Group Bug Bounty disclosed a bug submitted by exploitmsf: https://hackerone.com/reports/1762764 – Bounty: $150 Source link
Learn to Hack Web Apps – Live | #APIs #BOLA #brokenAuth Source link
macOS stores a copy of everything one prints forever Source link
☠️ The Malicious Office 365 Application Experiment.. that went bad.. real bad.. Source link
GraphQL is a modern query language for Application Programming Interfaces (APIs). Supported by Facebook and the GraphQL Foundation, GraphQL grew…



![The Iceberg Of Network Exploits [Parody] The Iceberg Of Network Exploits [Parody]](https://cdn.cybernoz.com/wp-content/uploads/2023/04/The-Iceberg-Of-Network-Exploits-Parody-360x270.jpg)