Category: Mix
Chatting with @Hacksplained about Bug Bounties and Infosec Jobs Source link
LHVM Demo Source link
Breaking Into Systems With Permission AKA Pentesting Source link
Internet Bug Bounty disclosed a bug submitted by ht0k: https://hackerone.com/reports/1889477 – Bounty: $480 Source link
Learn to Hack Web Apps – Live Source link
Fake Twitter accounts are dangerously out of control Source link
LIGHTS? 60 seconds on why i think a dynamic light setup is important. Source link
GovTech’s Cyber Security Group recently organised the STACK the Flags Cybersecurity Capture-the-Flag (CTF) competition from 4th to 6th December 2020….
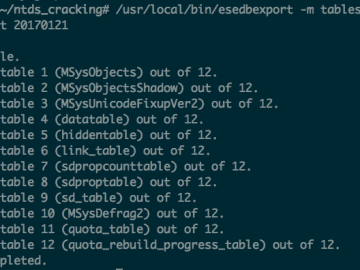
On internal pens, it’s really common for me to get access to the Domain Controller and dump password hashes for…
No BS Guide – Top 6 Browser Extensions for Bug Bounty Source link
Hacking 1Password | Episode 1 – Introduction Source link
Broken Access Control – Lab #11 Insecure direct object references | Long Version Source link