Category: Mix
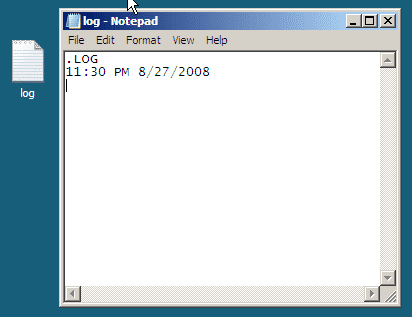
Yeah, that Notepad. It has a feature that few know about, and I’m not talking about word wrap. You can…
Many, especially in the blogsphere, are fond of saying, “This country is becoming fascist.” Or, “We’re on a path to…
Every year, the number of vulnerabilities discovered and recorded increases. The sheer volume of vulnerabilities makes it impractical for organizations…
There is much debate in the information security world regarding the proper definition of security. I have seen dozens of…
When debating someone who believes in the fundamental components of the Christian narrative, i.e. the choice by man to eat…
In late 2023, we’ve discovered and coordinated a quite interesting vulnerability affecting the Emarsys SDK for Android versions 3.6.1 and…
Many of my friends who are still somewhat religious despite being freethinkers see the benefits of rejecting ideologies that are…
At Fyodor‘s talk last week at Blackhat he talked about the research he’s been doing, and the ways that research…
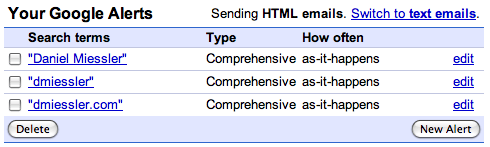
You don’t have to be an ego-freak to wonder if others are talking about you online. Egosurfing, i.e. the act…
Agentic AI is transforming business. Organizations are increasingly integrating AI agents into core business systems and processes, using them as…
A lingering feeling that I’ve had for roughly the last year was solidified for me last week at Blackhat/DEFCON. Making…
Ever wanted to take a piece of WordPress functionality and put it in a non-WordPress portion of your website? Like,…