Category: SecurityWeek
While silos pose significant dangers to an enterprise’s cybersecurity posture, consolidation serves as a powerful solution to overcome these risks,…
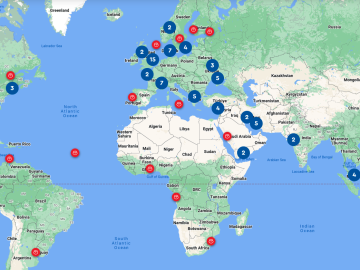
The NHL Stenden University of Applied Sciences in the Netherlands recently announced the launch of a database tracking cyberattacks and…
Five vulnerabilities, two deemed to be critical, have been found in the Terrestrial Trunked Radio (TETRA) standard. TETRA is the…
French aerospace, defense, and security giant Thales (Euronext Paris: HO) announced on Tuesday that it has reached an agreement with…
AMD has started releasing microcode patches to address a Zen 2 processor vulnerability that can allow an attacker to access…
A new zero-day vulnerability affecting a product of US-based enterprise software provider Ivanti has been exploited in an attack aimed…
Apple on Monday pushed out major security-themed updates to its flagship iOS, macOS and iPadOS platforms, warning that at least…
NuRR is a product that claims to intercept and capture the encryption keys at the start of a ransomware’s encryption…
Ransomware recovery company Coveware believes the Cl0p ransomware gang could earn as much as $100 million from the MOVEit hack,…
Data privacy and governance provider OneTrust today announced that it has raised $150 million in new funding, bringing the total…
When faced with an increasing number of cyberattacks, many organizations think in terms of what additional security tools they need….
A Los Angeles man has pleaded guilty to using SIM swapping to perpetrate multiple cybercrime schemes targeting hundreds of victims….