Category: TheHackerNews
New research has found that Google Cloud API keys, typically designated as project identifiers for billing purposes, could be abused…
Ravie LakshmananFeb 28, 2026National Security / Artificial Intelligence Anthropic on Friday hit back after U.S. Secretary of Defense Pete Hegseth…
Ravie LakshmananFeb 27, 2026Financial Crime / Social Engineering The U.S. Department of Justice (DoJ) this week announced the seizure of…
Ravie LakshmananFeb 27, 2026Network Security / Vulnerability The Shadowserver Foundation has revealed that over 900 Sangoma FreePBX instances still remain…
Ravie LakshmananFeb 27, 2026Malware / Linux Security Cybersecurity researchers have disclosed details of a malicious Go module that’s designed to…
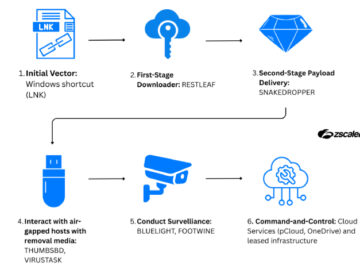
Ravie LakshmananFeb 27, 2026Malware / Surveillance The North Korean threat actor known as ScarCruft has been attributed to a fresh…
Ravie LakshmananFeb 27, 2026Endpoint Security / Windows Security Threat actors are luring unsuspecting users into running trojanized gaming utilities that…
Ravie LakshmananFeb 27, 2026Online Scam / Digital Advertising Meta on Thursday said it’s taking legal action to tackle scams on…
Cybersecurity researchers have disclosed details of a new botnet loader called Aeternum C2 that uses a blockchain-based command-and-control (C2) infrastructure…
Ravie LakshmananFeb 26, 2026Malware / Threat Intelligence A previously undocumented threat activity cluster has been attributed to an ongoing malicious…
Introduction: Steal It Today, Break It in a Decade Digital evolution is unstoppable, and though the pace may vary, things…
Ravie LakshmananFeb 26, 2026Malware / Software Security Cybersecurity researchers have disclosed details of a new malicious package discovered on the…