Category: TheHackerNews
Apr 30, 2025Ravie LakshmananPrivacy / Data Protection A high court in the Indian state of Karnataka has ordered the blocking…
Various generative artificial intelligence (GenAI) services have been found vulnerable to two types of jailbreak attacks that make it possible…
Apr 29, 2025Ravie LakshmananArtificial Intelligence / Data Protection Popular messaging app WhatsApp on Tuesday unveiled a new technology called Private…
Cybersecurity company SentinelOne has revealed that a China-nexus threat cluster dubbed PurpleHaze conducted reconnaissance attempts against its infrastructure and some…
Apr 29, 2025Ravie LakshmananEnterprise Security / Vulnerability Google has revealed that it observed 75 zero-day vulnerabilities exploited in the wild…
Find out how Reco keeps Microsoft 365 Copilot safe by spotting risky prompts, protecting data, managing user access, and identifying…
Apr 29, 2025Ravie LakshmananCybersecurity / Malware In a new campaign detected in March 2025, senior members of the World Uyghur…
Apr 29, 2025Ravie LakshmananVulnerability / Web Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two high-severity…
Not every security vulnerability is high risk on its own – but in the hands of an advanced attacker, even…
Government and telecommunications sectors in Southeast Asia have become the target of a “sophisticated” campaign undertaken by a new advanced…
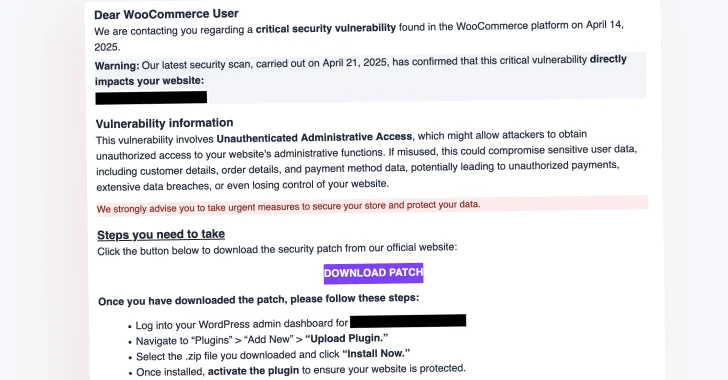
Apr 28, 2025Ravie LakshmananWebsite Security / Malware Cybersecurity researchers are warning about a large-scale phishing campaign targeting WooCommerce users with…
Apr 28, 2025Ravie LakshmananWeb Application Security / Vulnerability Threat actors have been observed exploiting two newly disclosed critical security flaws…