Category: TheHackerNews
Dec 03, 2024Ravie LakshmananVulnerability / Network Security Cisco on Monday updated an advisory to warn customers of active exploitation of…
Dec 03, 2024Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers have disclosed a set of flaws impacting Palo Alto Networks and…
Dec 03, 2024Ravie LakshmananThreat Intelligence / Email Security The North Korea-aligned threat actor known as Kimsuky has been linked to…
Dec 02, 2024Ravie LakshmananMalware / Cryptocurrency Taiwanese entities in manufacturing, healthcare, and information technology sectors have become the target of…
Dec 03, 2024Ravie LakshmananMalware / Phishing Attack A newly discovered malware campaign has been found to target private users, retailers,…
Dec 02, 2024The Hacker NewsAI Security / Data Protection Artificial Intelligence (AI) is no longer a far-off dream—it’s here, changing…
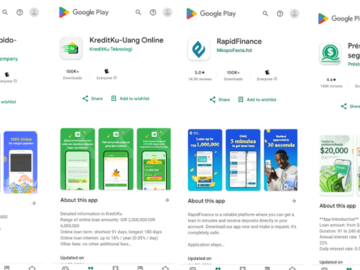
Dec 02, 2024Ravie LakshmananMobile Security / Financial Fraud Over a dozen malicious Android apps identified on the Google Play Store…
Dec 02, 2024Ravie LakshmananFinancial Fraud / Cryptocurrency A global law enforcement operation has led to the arrest of more than…
Nov 30, 2024Mohit KumarRansomware / Cybercrime A Russian cybercriminal wanted in the U.S. in connection with LockBit and Hive ransomware…
Nov 29, 2024Ravie LakshmananDisinformation / Artificial Intelligence A Moscow-based company sanctioned by the U.S. earlier this year has been linked…
Nov 29, 2024Ravie LakshmananAI Security / Cloud Security Microsoft has addressed four security flaws impacting its artificial intelligence (AI), cloud,…
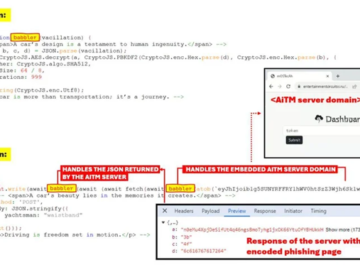
Nov 29, 2024Ravie LakshmananCybercrime / Cloud Security Cybersecurity researchers are warning about malicious email campaigns leveraging a phishing-as-a-service (PhaaS) toolkit…