Category: TheHackerNews
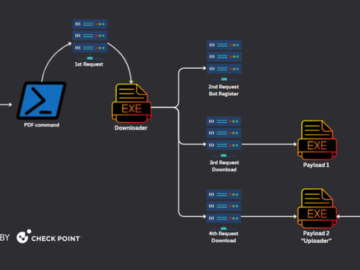
Multiple threat actors are weaponizing a design flaw in Foxit PDF Reader to deliver a variety of malware such as…
May 20, 2024NewsroomMalvertising / Cryptocurrency A “multi-faceted campaign” has been observed abusing legitimate services like GitHub and FileZilla to deliver…
May 20, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have observed a spike in email phishing campaigns starting early March 2024…
The U.S. Department of Justice (DoJ) has charged two arrested Chinese nationals for allegedly orchestrating a pig butchering scam that…
May 19, 2024NewsroomBanking Troja / Email Security The threat actors behind the Windows-based Grandoreiro banking trojan have returned in a…
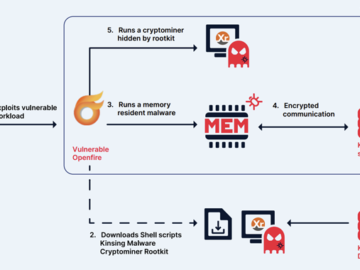
May 17, 2024NewsroomCryptojacking / Malware The cryptojacking group known as Kinsing has demonstrated its ability to continuously evolve and adapt,…
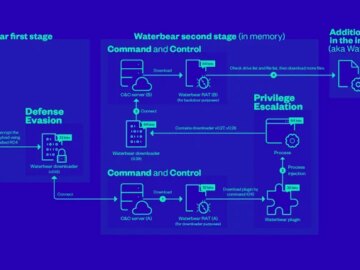
Cybersecurity researchers have shed more light on a remote access trojan (RAT) known as Deuterbear used by the China-linked BlackTech…
A new report from XM Cyber has found – among other insights – a dramatic gap between where most organizations…
May 17, 2024NewsroomLinux / Malware The Kimsuky (aka Springtail) advanced persistent threat (APT) group, which is linked to North Korea’s…
May 17, 2024NewsroomVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws…
May 16, 2024NewsroomVulnerability / Network Security Researchers have discovered a new security vulnerability stemming from a design flaw in the…
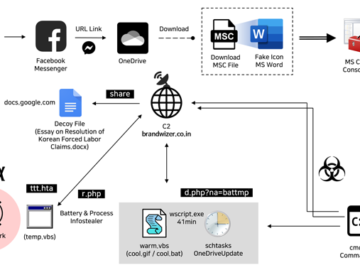
May 16, 2024NewsroomMalware / Cyber Espionage The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering…