Category: TheHackerNews
Feb 09, 2024NewsroomMalware / Dark Web The operators of Raspberry Robin are now using two new one-day exploits to achieve…
Feb 09, 2024NewsroomMobile Security / Cyber Threat Threat hunters have identified a new variant of Android malware called MoqHao that…
Feb 09, 2024NewsroomEndpoint Security / Cryptocurrency Sixty-one banking institutions, all of them originating from Brazil, are the target of a…
Introduction The modern software supply chain represents an ever-evolving threat landscape, with each package added to the manifest introducing new…
Feb 09, 2024NewsroomCyber Espionage / Threat Intelligence An unnamed Islamic non-profit organization in Saudi Arabia has been targeted as part…
Feb 09, 2024The Hacker NewsCloud Security / Open Source XDR / SIEM Cloud computing has innovated how organizations operate and…
Feb 09, 2024NewsroomZero Day Vulnerability / Network Security Fortinet has disclosed a new critical security flaw in FortiOS SSL VPN…
Feb 09, 2024NewsroomVulnerability / Zero Day Ivanti has alerted customers of yet another high-severity security flaw in its Connect Secure,…
Feb 08, 2024NewsroomEndpoint Security / Cyber Threat The threat actors behind a loader malware called HijackLoader have added new techniques…
The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some…
Feb 08, 2024The Hacker NewsUnified Identity / Cyber Security If you’ve listened to software vendors in the identity space lately,…
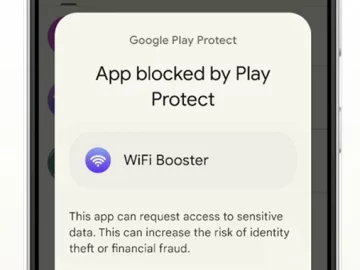
Feb 08, 2024NewsroomData Protection / Mobile Securit Google has unveiled a new pilot program in Singapore that aims to prevent…