Category: TheHackerNews
Jan 31, 2024NewsroomSoftware Security / Linux Multiple security vulnerabilities have been disclosed in the runC command line tool that could…
Jan 31, 2024NewsroomVulnerability / Zero Day Ivanti is alerting of two new high-severity flaws in its Connect Secure and Policy…
The SEC isn’t giving SaaS a free pass. Applicable public companies, known as “registrants,” are now subject to cyber incident…
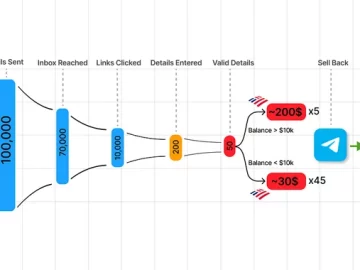
Jan 31, 2024NewsroomCyber Crime / Hacking News Cybersecurity researchers are calling attention to the “democratization” of the phishing ecosystem owing…
Jan 31, 2024NewsroomCryptocurrency / Cybersecurity A financially motivated threat actor known as UNC4990 is leveraging weaponized USB devices as an…
Jan 31, 2024NewsroomCyber Attack / Network Security A pair of recently disclosed zero-day flaws in Ivanti Connect Secure (ICS) virtual…
Jan 31, 2024NewsroomVulnerability / Endpoint Security Malicious local attackers can obtain full root access on Linux machines by taking advantage…
Jan 30, 2024NewsroomCyber Crime / Malware A Brazilian law enforcement operation has led to the arrest of several Brazilian operators…
Jan 30, 2024NewsroomDevSecOps / Vulnerability GitLab once again released fixes to address a critical security flaw in its Community Edition…
Jan 30, 2024NewsroomMalware / Cyber Espionage The China-based threat actor known as Mustang Panda is suspected to have targeted Myanmar’s…
Jan 30, 2024NewsroomGenerative AI / Data Privacy Italy’s data protection authority (DPA) has notified ChatGPT-maker OpenAI of supposedly violating privacy…
Each New Year introduces a new set of challenges and opportunities for strengthening our cybersecurity posture. It’s the nature of…