Category: TheHackerNews
Oct 23, 2025Ravie LakshmananData Breach / Vulnerability E-commerce security company Sansec has warned that threat actors have begun to exploit…
Cybersecurity researchers have disclosed details of a coordinated spear-phishing campaign dubbed PhantomCaptcha targeting organizations associated with Ukraine’s war relief efforts…
Oct 22, 2025Ravie LakshmananMalware / Cyber Espionage The Iranian nation-state group known as MuddyWater has been attributed to a new…
Oct 22, 2025Ravie LakshmananCryptocurrency / Software Integrity Cybersecurity researchers have uncovered a new supply chain attack targeting the NuGet package…
Oct 22, 2025Ravie LakshmananCyber Espionage / Vulnerability Threat actors with ties to China exploited the ToolShell security vulnerability in Microsoft…
From Detection to Resolution: Why the Gap Persists A critical vulnerability is identified in an exposed cloud asset. Within hours,…
Oct 22, 2025The Hacker NewsData Breach / Enterprise Security The advice didn’t change for decades: use complex passwords with uppercase,…
Oct 22, 2025Ravie LakshmananCyber Espionage / Network Security Government, financial, and industrial organizations located in Asia, Africa, and Latin America…
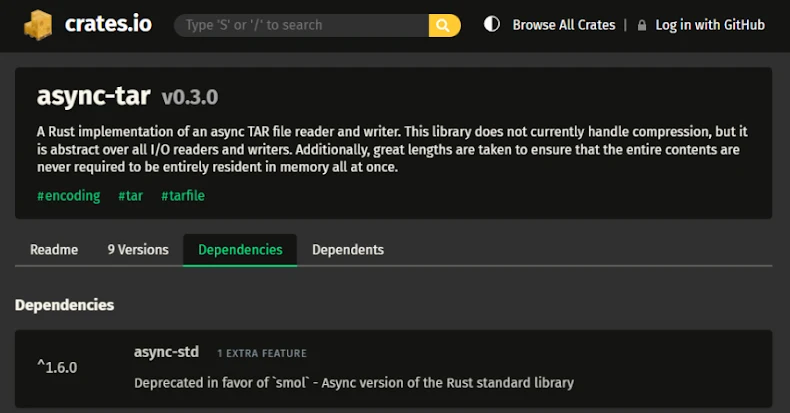
Oct 22, 2025Ravie LakshmananVulnerability / Data Protection Cybersecurity researchers have disclosed details of a high-severity flaw impacting the popular async-tar…
Oct 22, 2025Ravie LakshmananVulnerability / Network Security TP-Link has released security updates to address four security flaws impacting Omada gateway…
Oct 21, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have shed light on the inner workings of a botnet malware called…
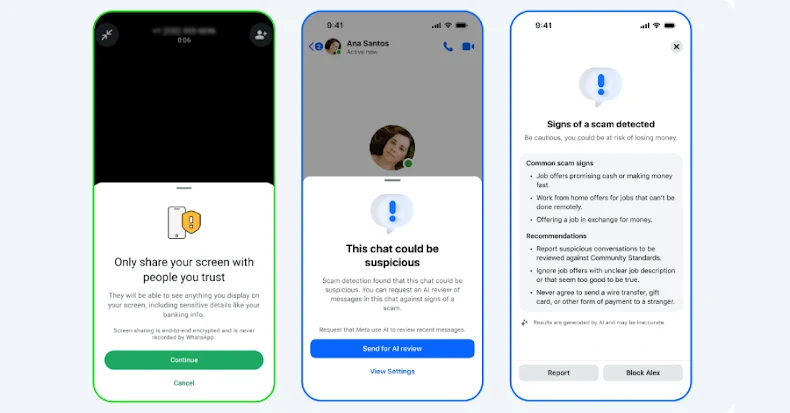
Oct 21, 2025Ravie LakshmananCryptocurrency / Encryption Meta on Tuesday said it’s launching new tools to protect Messenger and WhatsApp users…