CISA has ordered federal agencies to secure their systems within three weeks against a high-severity Linux kernel flaw actively exploited in attacks.
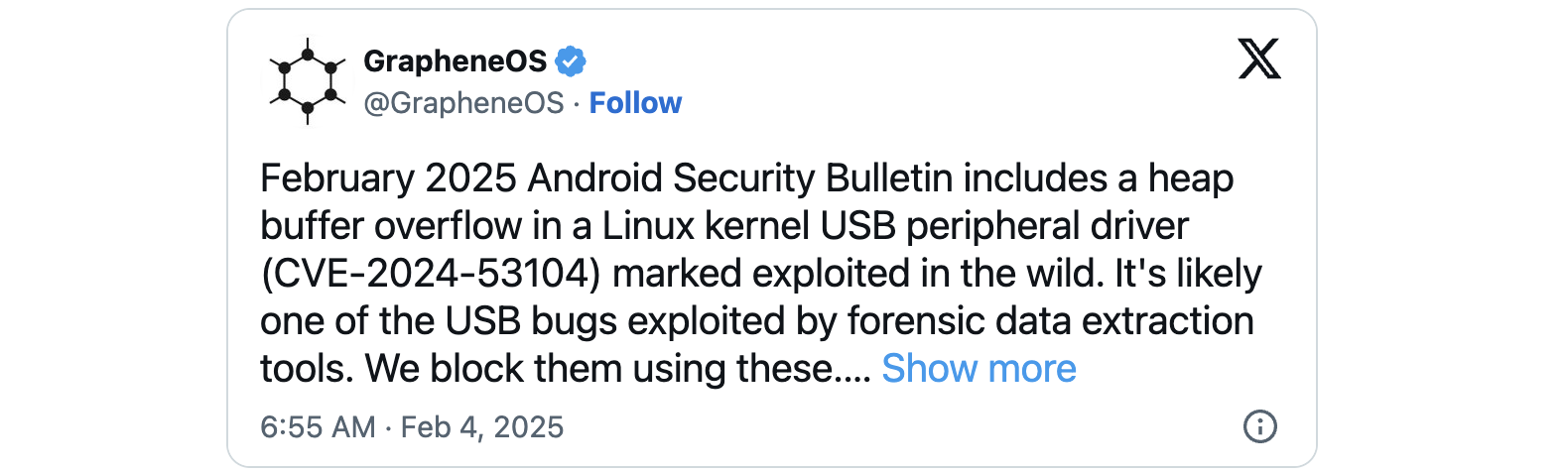
Tracked as CVE-2024-53104, the security bug was first introduced in kernel version 2.6.26 and was patched by Google for Android users on Monday.
“There are indications that CVE-2024-53104 may be under limited, targeted exploitation,” the Android February 2025 Android security updates warn.
According to Google’s security advisory, this vulnerability is caused by an out-of-bounds write weakness in the USB Video Class (UVC) driver, which allows “physical escalation of privilege with no additional execution privileges needed” on unpatched devices.
The driver’s inability to accurately parse UVC_VS_UNDEFINED frames within the uvc_parse_format function triggers the issue, leading to frame buffer size miscalculations and potential out-of-bounds writes.
While Google didn’t provide additional information on the zero-day attacks exploiting this vulnerability, the GrapheneOS development team says this USB peripheral driver vulnerability is “likely one of the USB bugs exploited by forensic data extraction tools.”
As mandated by the November 2021 Binding Operational Directive (BOD) 22-01, U.S. federal agencies must secure their networks against ongoing attacks targeting flaws added to CISA’s Known Exploited Vulnerabilities catalog.
The cybersecurity agency has given Federal Civilian Executive Branch (FCEB) agencies three weeks to patch their Linux and Android devices by February 26.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” CISA warned today.
On Tuesday, CISA also tagged high-severity and critical vulnerabilities in Microsoft .NET Framework and Apache OFBiz (Open For Business) software as actively exploited in the wild. However, it didn’t provide details on who was behind the attacks.
With Five Eyes cybersecurity agencies in the UK, Australia, Canada, New Zealand, and the U.S., it also shared security guidance for network edge devices, urging manufacturers to improve forensic visibility to help defenders detect attacks and investigate breaches.
