Cl0p is claiming responsibility for a new data breach affecting the National Health Service (NHS UK). On November 11, 2026, the ransomware group posted on its dark web leak site, accusing the healthcare provider of neglecting its security, stating, “The company doesn’t care about its customers; it ignored their security.”
Although the group has not revealed the volume of stolen data, the announcement aligns with ongoing attacks and reports pointing out CL0p of exploiting vulnerabilities in Oracle’s E-Business Suite (EBS).
NHS officials have not confirmed a breach, but their cybersecurity division did issue alerts in October about critical flaws in Oracle EBS. That alert warned healthcare and public sector systems relying on Oracle’s enterprise software to apply immediate patches and restrict internet exposure. The timing of the Cl0p post now suggests the group may have exploited the same vulnerabilities NHS had already flagged a month earlier.
The Washington Post
While the NHS claim is still being investigated, Cl0p’s campaign has already proven its reach. Just days earlier, on November 7, the group announced it had breached The Washington Post by exploiting the same Oracle EBS flaws.
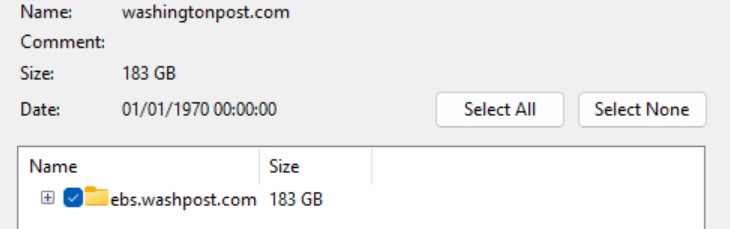
As seen by Hackread.com, the hackers published what they claim is 183GB of data under a folder labeled ebs.washpost.com. The Washington Post later confirmed it was impacted, saying it was among the victims of a “breach of the Oracle E-Business Suite platform.”
What Experts Think
Security experts say the Washington Post attack fits Cl0p’s pattern of large-scale, data-theft operations targeting enterprise software used across multiple sectors. Lidia Lopez, Senior Threat Intelligence Analyst at Outpost24, noted that the incident highlights Cl0p’s focus on exploiting high-value business systems rather than random targets.
She explained that the group has moved away from traditional ransomware encryption toward coordinated data-exfiltration campaigns that leverage zero-day flaws in critical software such as MOVEit, GoAnywhere, and Oracle EBS.
Unlike affiliate-based ransomware operations, Cl0p’s structure is centralised and technical. Lopez said this setup allows the group to conduct synchronised attacks against hundreds of organisations before vendors release patches.
Their tactics often involve scanning for vulnerable systems, gaining remote access, maintaining persistence, and quietly siphoning data for months before making demands or publishing leaks.

Faik Emre Derin, Technical Content Manager at SOCRadar, added that the Oracle EBS campaign revolves around CVE-2025-61882, a severe remote code execution flaw with a CVSS score of 9.8.
His team’s analysis shows the exploitation began around August 2025, months before Oracle issued an emergency patch on October 4. The affected versions range from 12.2.3 to 12.2.14, with attackers focusing on the BI Publisher Integration module that allows unauthenticated access to vulnerable systems.
Derin said the exploit’s spread accelerated when a separate group called Scattered Lapsus$ Hunters leaked proof-of-concept code on October 3. This leak allowed additional threat actors, including Cl0p and FIN11, to expand attacks on a global scale.
He recommended that organisations running Oracle EBS install the October 2025 patch immediately, conduct forensic reviews dating back to August, and monitor for connections to suspicious IPs such as 200.107.207.26 and 185.181.60.11.
The ongoing campaign has also affected other high-profile organisations, including Harvard University and American Airlines’ subsidiary Envoy. Investigations by Mandiant and Google’s Threat Intelligence Group suggest the activity started in late September 2025, targeting companies that rely heavily on Oracle EBS for finance, HR, and supply-chain management.
Oracle has since released patches addressing the vulnerabilities and urged customers to update without delay. Despite those efforts, many systems remain exposed, providing Cl0p and affiliated groups with continued opportunities for exploitation.
The inclusion of NHS UK and The Washington Post in the victim list places the Cl0p campaign among the most significant enterprise-software breaches in recent years. With stolen data already circulating online and more victims expected to surface, experts warn that the threat from unpatched Oracle systems is far from over.
