Earlier today, the RANSOMEDVC ransomware group claimed to have breached Colonial Pipeline company and also leaked 5GB worth of data including internal files and photos.
The infamous RANSOMEDVC ransomware group has declared that they successfully infiltrated Colonial Pipeline, the American company operating a significant pipeline system that transports over 100 million gallons of various petroleum products, including gasoline, diesel fuel, and jet fuel, on a daily basis.
These latest claims from the RANSOMEDVC group surfaced through posts on their dark web blog. Furthermore, RANSOMEDVC shared their claims via their recently launched Telegram channel and their X (previously Twitter) account. It’s worth noting that RANSOMEDVC is the same group that claimed to have breached Sony Corporation in September 2024.
In correspondence with Hackread.com, the group disclosed that Colonial Pipeline had refused to pay any ransom. However, they did not disclose the size of the alleged stolen data or the ransom amount demanded from the company.
Additionally, RANSOMEDVC publicly shared a file containing 5GB of data, claiming it belongs to Colonial Pipeline. Hackread.com has examined and analyzed this data. While it’s premature to draw definitive conclusions, the files and folders appear to contain a wealth of information, including diagrams, internal documents, leak detection policies, ICS and SCADA-related presentations, as well as photos of employees handling electronic equipment, among other things.
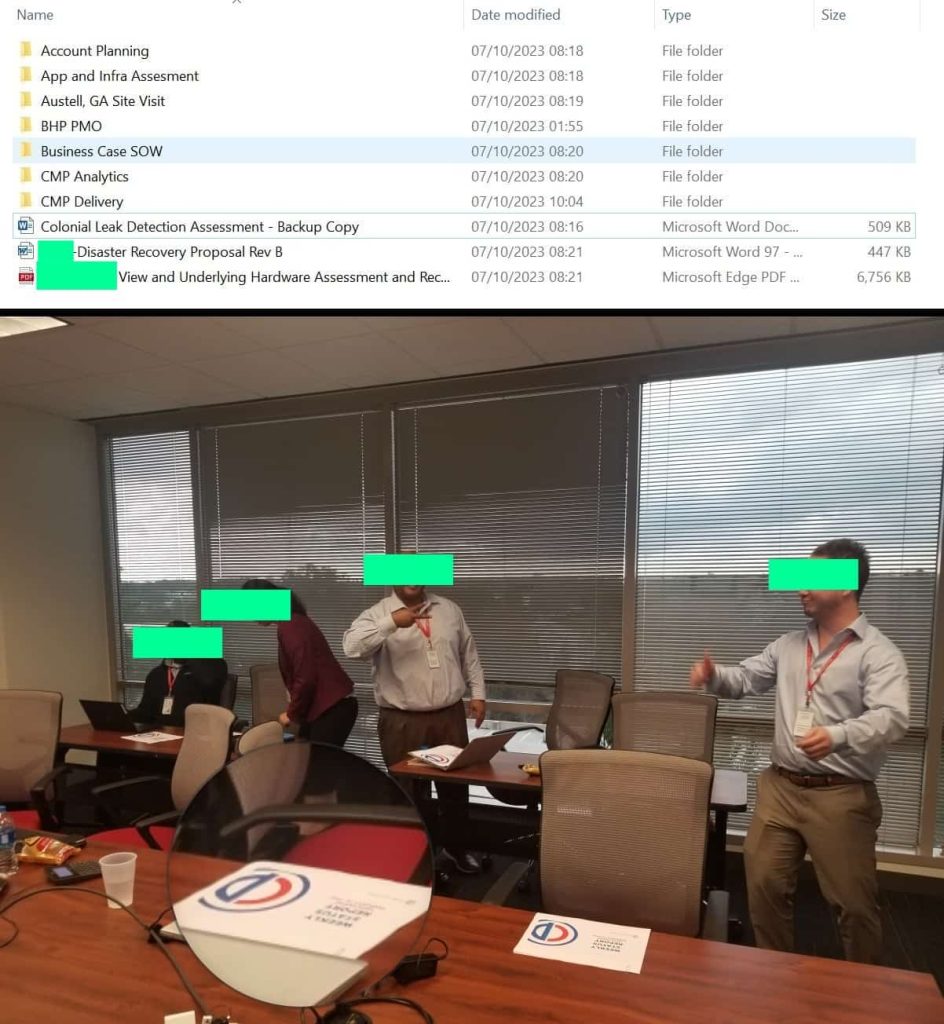
Notably, the photos of employees reveal that their desks feature a “Weekly Status Report” with the Colonial Pipeline logo. However, in an exclusive statement to Hackread.com, Colonial Pipeline has rejected the claims made by the RANSOMEDVC ransomware group and linked the leaked files to be part of “a third-party data breach unrelated to Colonial Pipeline.”
“Colonial Pipeline is aware of unsubstantiated claims posted to an online forum that its system has been compromised by an unknown party. After working with our security and technology teams, as well as our partners at CISA, we can confirm that there has been no disruption to pipeline operations and our system is secure at this time. Files that were posted online initially appear to be part of a third-party data breach unrelated to Colonial Pipeline.“
Colonial Pipeline
Colonial Pipeline’s Previous Encounter with Ransomware
This isn’t the first time that a ransomware group has asserted they breached Colonial Pipeline. In May 2021, a group called DarkSide successfully infiltrated the company’s systems, resulting in significant operational disruption.
Colonial Pipeline chose to pay a ransom of 75 Bitcoin to the DarkSide ransomware gang on May 7, 2021, amounting to approximately $4.4 million at that time. The ransom was paid to regain access to their systems and expedite the resumption of operations.
In June 2021, the U.S. Department of Justice (DoJ) disclosed that it had seized $2.3 million in Bitcoin, which Colonial Pipeline had paid to the DarkSide ransomware gang. The seizure was made possible by tracing the cryptocurrency trail and identifying the wallets used to store the ransom.
Furthermore, the FBI successfully dismantled DarkSide’s infrastructure, leading to the complete downfall of the ransomware group. As of November 2021, the U.S. government offered a $10 million reward for substantial information on the DarkSide ransomware gang.
The 2021 ransomware attack on Colonial Pipeline remains one of the most high-profile incidents in the history of ransomware attacks, underscoring the threats posed to critical infrastructure. This event also reignited debates about the wisdom of companies paying ransomware demands.
RELATED ARTICLES
- ALPHV ransomware gang claims it has hacked Amazon’s Ring
- GhostSec Claim Breaching Iranian Govt Surveillance Software Tool
- Acer Data Breach: Hacker Claims to Sell 160GB Trove of Stolen Data
- BlackCat (ALPHV) Gang Claims Ransomware Attack on NCR Data Center
- Hacker Claims to Have Data of 7 Million 23andMe Users from DNA Service
