Anti-Phishing, DMARC
,
Cybercrime
,
Fraud Management & Cybercrime
Database Will Provide Intelligence of Use to Online Criminals, Expert Warns

See Also: OnDemand | Understanding Human Behavior: Tackling Retail’s ATO & Fraud Prevention Challenge
“The database … will unfortunately lead to a lot of hacking, targeted phishing and doxxing” by criminals and governments alike, says Alon Gal, CTO at Israeli cybercrime intelligence firm Hudson Rock, in a post to LinkedIn. “This is one of the most significant leaks I’ve seen.”
The leak includes 211,524,284 records, comprising names, usernames, email addresses and follower counts, according to the free data breach notification service Have I Been Pwned.
The information had been publicly offered for sale last month to Twitter CEO Elon Musk as a database of 400 million records, which was first spotted by Gal.
On Wednesday, the owner released a pared down version – likely to eliminate duplicates – for free via a popular cybercrime forum. The identity of the individual who controls or amassed the information remains unknown.
While the Twitter data leak doesn’t include passwords, many other data breaches have included such information, which experts say could be easily gathered and merged with many of these records.
Gal says the records provide useful intelligence to criminals, such as knowing which Twitter accountholders are interested in – and perhaps owners of – cryptocurrency, based on accounts having .eth in their name or other crypto-themed text. The list can also be used to target high-profile accounts based on follower counts, identify “OG” accounts that have desirable usernames, target “political accounts” as well as unmask “‘anonymous’ accounts” that didn’t use a unique email for Twitter, but rather an address that can be cross-indexed with other data leaks to identify the owner, he says.
Criminals Abused Twitter API
The email addresses do not appear to have been stolen from Twitter. Rather, “the data was obtained sometime in 2021 by abusing an API that enabled email addresses to be resolved to Twitter profiles,” according to HIBP. Accordingly, the information was compiled well before Musk bought Twitter for $44 billion in October 2022.
This isn’t the only set of data to have been compiled by individuals who used the API flaw. Last November, an attacker dumped a database containing 5.4 million users’ usernames, display names, bios, locations, email addresses and phone numbers.
Twitter confirmed last August that data had been stolen from a “let others find you by your phone” feature, which it added in June 2021, then locked down in January 2022, after receiving a bug report about the risk posed by such functionality. Until it got fixed, Twitter said that “if someone submitted an email address or phone number to Twitter’s systems, Twitter’s systems would tell the person what Twitter account the submitted email addresses or phone number was associated with, if any.”
Lifecycle of Breached Data
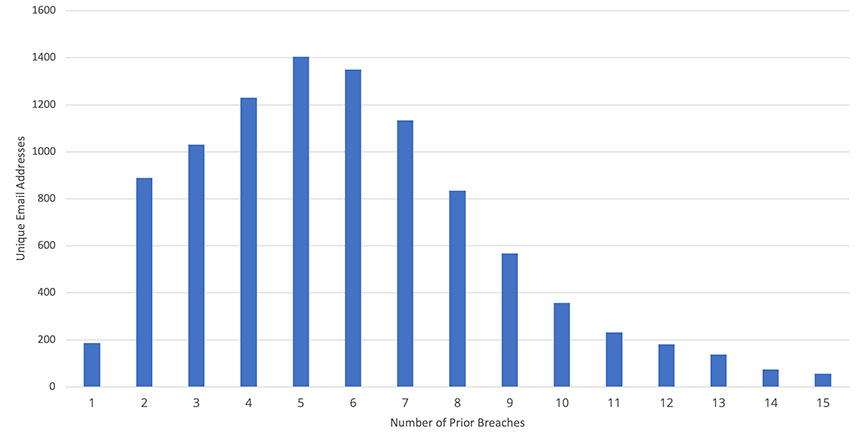
Based on sampling the first 10,000 records contained in the Twitter data dumped Wednesday, nearly every email address has appeared in previous data breaches, reports data breach expert Troy Hunt, who created and runs Have I Been Pwned.
The free breach notification service emails anyone who registers an email address, whenever that email appears in a public data breach or data dump. To date it has tracked 12.4 billion pwned accounts, with some email addresses having appeared in multiple breaches.
For the recent leak of over 200 million Twitter records, “the 98% ‘pwned before’ rate clearly indicates the email addresses were taken from other data breaches then used to query the vulnerable API,” Hunt says via Twitter. Those queries allowed whoever compiled the data set to add the user’s name, Twitter username and follower counts associated with each of the email addresses they’d tested, which were tied to a Twitter account.
Many emails contained in the sample of leaked Twitter records appear in three of the top 10 biggest breaches or collections of leaked data to date, as tracked by HIBP:
- 62% appear in the Collection1 data set (773 million records total);
- 58% appear in the ExploitIn data set (593 million records total);
- 26% appear in the AntiPublic data set (458 million records total).
“No revelations here IMHO, just confirmation that once data is out there it gets re-circulated and re-abused over and over again,” Hunt says. “These addresses are only in the scraped Twitter data because they’d already been compromised elsewhere, and so the cycle continues.”
How Many Newly Leaked Twitter User Emails Appeared in Prior Breaches?