The rise of Artificial Intelligence (AI) has undeniably transformed various sectors, with tools like ChatGPT, DeepSeek and Gemini becoming household names. However, this advancement has also created an environment where scammers can thrive.
McAfee Labs has uncovered a concerning trend where malicious actors are exploiting the popularity of AI tools, to distribute malware. This tactic, often referred to as SEO poisoning, exploits trending search terms to lure unsuspecting users to malicious websites.
The recent surge in interest surrounding DeepSeek-R1, a cost-effective AI model released under an open-source license an AI model and its subsequent chatbot launch, provided a solid platform for such exploitation.
This increasing interest, coupled with occasional website unavailability due to high traffic, created an ideal scenario for scammers. They take advantage of the “excitement, anxiety, and impatience” of users by distributing malware disguised as DeepSeek installers, McAfee researchers noted in the blog post shared with Hackread.com.
The attack starts with a user’s search, after which they are directed to websites offering DeepSeek applications for Windows, Mac, and Android. These websites, however, are malicious, leading to the download of malware, fake installers that bundle unwanted third-party software, and fraudulent captcha pages.
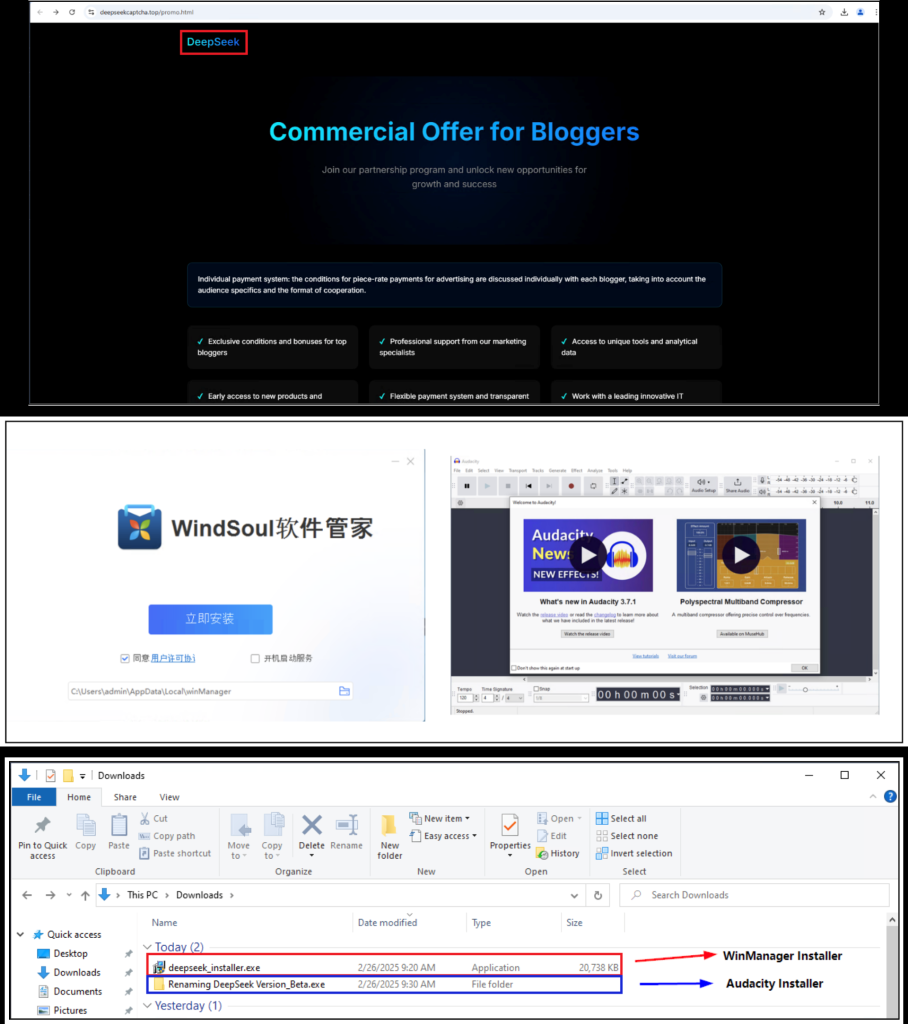
Fake DeekSeek Installers, Websites and Apps
McAfee Labs identified several malware campaigns associated with DeepSeek, including fake installers, impersonator websites, and fake mobile apps. These campaigns distributed various types of malware, such as keyloggers, crypto miners, and password stealers. One notable example involved fake installers that bundled legitimate software with unwanted third-party applications, generating revenue through pay-per-install programs.
Another tactic observed was the use of fake captcha pages, designed to trick users into downloading and executing malicious software. These pages employed “brand impersonation,” mimicking DeepSeek’s branding to appear legitimate. Upon registering for a fake partnership program, users were redirected to these captcha pages, which then prompted them to execute commands that installed malware capable of stealing sensitive information.
Monero Miner Behind Fake DeepSeek Installer
A technical analysis of a crypto miner disguised as DeepSeek software revealed that after installation the malware communicated with a command-and-control server to download and execute a PowerShell script. This script employed process injection techniques to evade detection and establish persistence in the victim’s system. The payload, identified as XMRig mining software, then initiated a Monero mining operation, utilizing a portion of the system’s CPU resources.
Scammers chose Monero probably due to its emphasis on anonymity, making it difficult to trace the flow of funds. This highlights the attackers’ focus on covert operations and maximizing their gains while minimizing the risk of detection.
McAfee Labs emphasizes the importance of staying alert and informed, especially during hype cycles surrounding emerging technologies. Another step toward safety is scanning suspicious links and files on VirusTotal before opening or executing them.
