A major data breach has compromised the personal records of nearly 14,000 individuals under court supervision, alongside contact information for thousands of criminal justice employees.
The breach targeted RemoteCOM, a company that provides computer, smartphone, and tablet monitoring services for pretrial, probation, and parole clients across 49 US states. The incident, first detailed by Straight Arrow News (SAN), has raised serious concerns about the security of highly sensitive surveillance data.
The SCOUT Software
The software at the centre of the controversy is SCOUT, a proprietary surveillance application advertised as the “premier” client management service. According to a leaked RemoteCOM training manual, SCOUT is used to track people involved in a wide range of offences, including everything from sex offences and narcotics to alleged terrorism, stalking, fraud, domestic violence, and hacking.
While its stated purpose is client management, SCOUT functions as aggressive spyware by secretly recording keystrokes, capturing screenshots, tracking location, and automatically sending alerts to probation officers if an individual types certain keywords.
An informational handout discovered in the leak revealed the financial burden placed on offenders: a $50 installation fee for every computer, a $30 fee for phone installations, and a recurring $35 monthly monitoring fee per device. The records also specifically label offenders believed to be “tech savvy.”
Critical Information Exposed
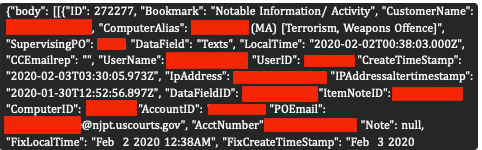
According to SAN’s report, the hacker, known as “wikkid,” claimed the breach against RemoteCOM was “easiest” one. The leaked information was divided into two key files:
‘Clients’ File (approx. 14,000 records): This file contained the names, home addresses, phone numbers, email addresses, and IP addresses of individuals currently or previously monitored by SCOUT, along with their specific charges.
The data was extremely personal; one record showed the SCOUT application had even been installed on a client’s (an officer’s) sister-in-law and fiancé’s phones. The file also contained over 380,000 activity alerts sent to officers, some flagging keywords like “Nazi” or “sex,” revealing the invasive nature of the surveillance.
‘Officers’ File (6,896 entries): This list exposed the names, job titles, phone numbers, work addresses, and email addresses for law enforcement personnel who use the service.

Dangers for Both Sides
The data leak poses substantial dangers for both the monitored individuals and the officers. For the people being monitored, the exposure of their personal details and offence categories makes them potential targets, even though not every client listed is a convicted offender (some may be suspects or awaiting trial).
On the other hand, for the officers and justice system staff, the leak of their contact and workplace information exposes them and their families to threats.
RemoteCOM released a short statement to SAN, confirming they are “assessing the situation currently.” This is a developing story. Hackread.com will update its readers as more information regarding the breach, its impact, and RemoteCOM’s further response becomes available.
