Cybercriminals exploit Trump’s assassination attempt to lure victims into a crypto doubling scam using deepfake Elon Musk videos on hijacked YouTube channels. Bitdefender Labs uncovers malicious domains and advises caution.
Cybercriminals and crypto scammers have seized upon the recent assassination attempt against former US President Donald Trump to lure unsuspecting victims into a new cryptocurrency doubling scheme.
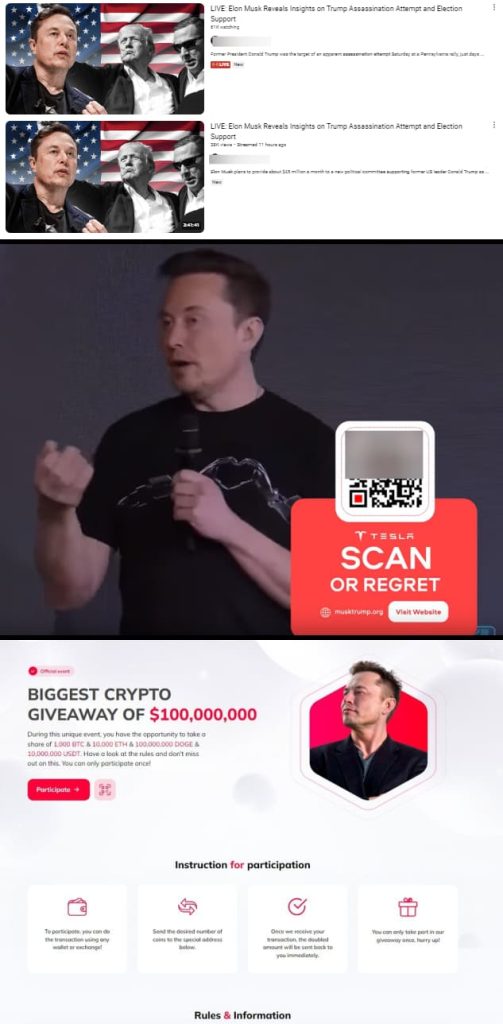
The scam, which researchers at Bitdefender Labs have detected, involves hijacking YouTube channels to broadcast deepfake videos of Tesla CEO Elon Musk, promising to reveal insights into the attack on Trump.
The hijacked channels, some of which boast subscriber counts in the millions, have been stripped of their original content and renamed to include references to Tesla and Donald Trump Jr.
The videos feature a looped deepfake of Musk encouraging viewers to participate in a cryptocurrency giveaway by scanning a QR code embedded in the video. These codes direct users to fraudulent websites that resemble legitimate Tesla domains or those associating Musk with Trump.
The descriptions of the hijacked channels further promote the scam, claiming that Musk plans to provide substantial financial support to Trump’s presidential campaign. One description reads, “Elon Musk plans to provide about $45 million a month to a new political committee supporting former US leader Donald Trump as part of the presidential campaign.”
According to Bitdefender’s report shared with Hackread.com ahead of publishing on Wednesday, researchers have identified five malicious domains associated with this ongoing campaign, all of which are detected and blocked by their anti-phishing and anti-fraud filtering systems.
To protect against falling victim to such scams, users are advised to exercise caution when encountering videos with click-bait titles related to Tesla or the attack on Trump, double-check messages promising double returns on crypto investments, and avoid scanning QR codes in YouTube videos promoting crypto giveaways.
Additionally, users should inspect YouTube channels promoting crypto giveaways for suspicious activity, such as missing or deleted videos and closed comment sections, and report any suspicious activity to the platform or relevant authorities. Employing a comprehensive security solution that can block phishing attempts and fraudulent links is also highly recommended.
As cybercriminals continue to adapt and exploit current events to deceive unsuspecting individuals, users must remain alert and adhere to best practices in cybersecurity to safeguard their digital assets and personal information.
RELATED TOPICS
- Fake YouTube Android Apps Used to Distribute CapraRAT
- New YouTube phishing scam using authentic email address
- YouTube Channels Hacked, Spread Lumma Stealer Malware
- British Military’s YouTube Account Hacked to Scam Crypto Users
- Google details cookie stealer malware campaign targeting YouTubers
