A hacker using the alias 888 is claiming responsibility for a major data breach affecting the European Space Agency (ESA), alleging theft of more than 200 GB of internal data. The claim surfaced on DarkForums, where the actor states the attack occurred on 18 December 2025 and resulted in the full exfiltration of private development and documentation assets.
The material advertised for sale is described as a one-time package, with payment requested exclusively in Monero (XMR). According to the post, the data includes private Bitbucket repositories, internal documentation, infrastructure definitions, and sensitive credentials.
Sample Screenshots Analysed
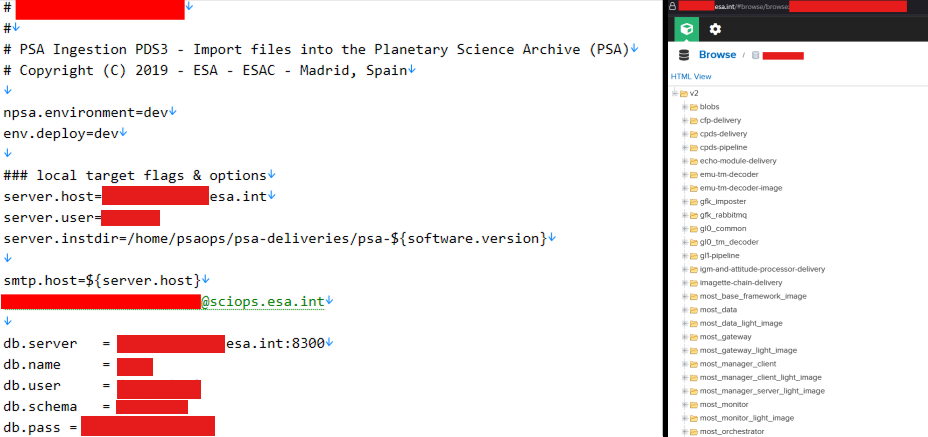
Screenshots shared by the hacker show what appears to be internal ESA-related environments. One image shows a build.properties.dev configuration file referencing PSA ingestion workflows, internal hosts ending in esa.int, SMTP settings, and database connection details.
Several fields are redacted in the screenshots, though directory paths and variable naming conventions are visible. The presence of hardcoded server references and environment-specific parameters suggests material taken directly from development or integration systems.
Another screenshot displays internal technical documentation marked as proprietary and confidential, including documents carrying Thales Alenia Space internal notices and Airbus Defence and Space branding.
These files include spacecraft reference frames, subsystem descriptions, and detailed engineering diagrams typically restricted to partners and internal teams. The documents appear formatted as official deliverables with reference numbers, issue dates, and page counts.
Additional images show what looks like an internal project management and development tooling. A Jira instance lists structured subsystem requirements for the Security Operations Centre (SOC) and Operations Control and Command System (OCCS) components, covering data reception, validation, orchestration, job execution, and non-functional requirements. The hierarchy and naming conventions indicate active operational or development programs rather than archival material.
A separate screenshot shows a Bitbucket project view containing numerous repositories tied to deployment pipelines, Docker images, orchestration services, monitoring components, and data processing chains.
Repository names reference CI/CD pipelines, packaging systems, gateway services, and core framework images. This aligns with the actor’s claim of access to source code, automation workflows, and infrastructure logic.
Big If True
If authentic, the exposure described would carry serious implications. Source code, CI/CD pipelines, API tokens, access credentials, Terraform definitions, and SQL files together represent a complete attack surface map. Such material could enable follow-on breaches, supply chain abuse, or long-term espionage targeting ESA programs and partner organisations.
At the time of writing, the European Space Agency has not issued a public statement confirming or denying the breach. The authenticity of the dataset has not been independently verified, though the screenshots show a level of internal detail that would be difficult to fabricate without real access. Hackread.com has reached out to the ESA, and this story will be updated accordingly.
888 and Previous Breaches
The alias 888 has surfaced in multiple high-profile incidents prior to the alleged ESA breach. One such case involved Samsung Medison, where the attacker claimed access to sensitive data through a compromised third-party service.
The breach exposed internal and customer related information rather than Samsung Medison’s core infrastructure, pointing to an attack path that relied on weaker external dependencies. The entire stolen data was later leaked online.
In a separate breach attributed to the same alias, data belonging to Microsoft and Nokia employees was leaked online. The exposed material included internal contact details and corporate information.



