An X (Twitter) account, operated by hackers using the handle @MonkeyInject, alleges that the breach was facilitated by a former employee of Plume.
The smart Wi-Fi service provider, Plume, has apparently fallen victim to a data breach. The perpetrators, claiming responsibility for the incident, made their announcement on the notorious Breach Forums.
This is the same forum where, in the past few days, we observed the data leak of a scraped LinkedIn user database comprising 35 million entries and two scraped databases from Chess.com.
The Palo Alto, California-based Plume is a SaaS (software-as-a-company) platform offering users AI security, smart Wi-Fi, and cloud management services, and has footprints in over 45 countries, covering 55 million homes and small businesses.
The attackers are currently claiming to have stolen over 20GB of the company’s Wi-Fi database with over 15 million lines of information. Plume, however, has not confirmed the news, stating that it is aware of the attackers’ claims and has launched an investigation to verify these claims.
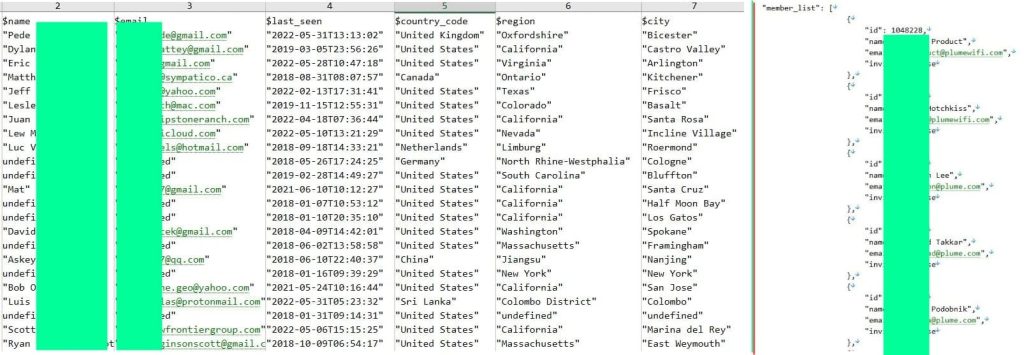
At the same time, dissatisfied with Plume’s response, the hackers have released two CSV files, each containing purported data of the company’s customers and employees. As reported by Hackread.com, the first file includes email addresses, full names, countries, device details, and other information related to the alleged 26,000 customers of the company.
The second file comprises 3,086 email addresses and full names, which the hackers claim belong to Plume’s employees. A majority of the leaked email addresses are associated with the @plume.com and @plumewifi.com domains.
Darren James – Senior Product Manager, Specops Software – An Outpost24 Company commented on the alleged breach adding, “Any data breach that involves the loss of personal information is always a huge concern, not just for the affected organisation, but specifically for people whose data has been stolen.”
“Although we don’t have many details on this particular breach right now, even the loss of a username or email address can open an attack vector on any site where you have also used those same details,” James emphasised.
“My advice for anyone affected by such breaches, it is imperative that they change their passwords across all platforms that use the same username as soon as possible, ideally using a password that hasn’t already been breached,” he said.
Hackers on X (Twitter)
The hackers have also created an X (Twitter) profile to disclose details of the attack and stolen data on their handle @MonkeyInject, which is an interesting step as hackers usually hide their identities and operate covertly. Addressing the X community, the hackers wrote that:
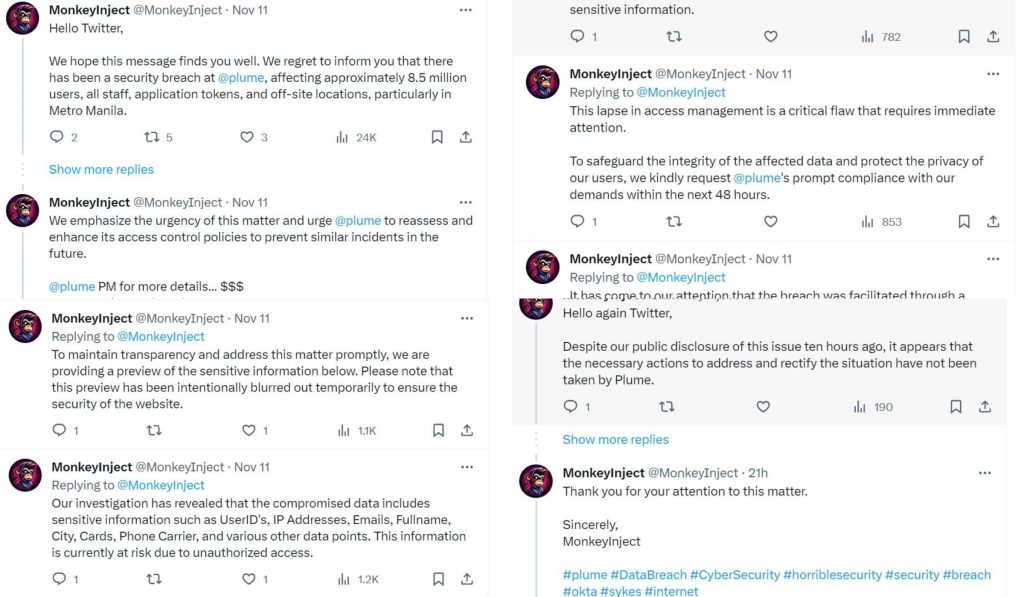
“We hope this message finds you well. We regret to inform you that there has been a security breach at @plume, affecting approximately 8.5 million users, all staff, application tokens, and off-site locations, particularly in Metro Manila.”
In subsequent tweets, they noted that the leak includes email addresses, first and last names, device details, IP addresses, user IDs, city, cards, carriers, and other data. The hacker provided a preview of the information on their Twitter page to legitimize their claims.
MonkeyInject also revealed that the breach was facilitated by a former employee of Plume, who left the company in 2023 but still possessed access rights, indicating Plume’s lackluster approach toward implementing robust security protocols.
The hackers gave the company 48 hours to comply with their demands otherwise, they would disclose more data. They also encouraged Plume to improve its access control policies to prevent similar incidents.
“This lapse in access management is a critical flaw that requires immediate attention. To safeguard the integrity of the affected data and protect the privacy of our users, we kindly request @plume’s prompt compliance with our demands within the next 48 hours. Failure to do so may result in the disclosure and sharing of additional sensitive information,” the hackers tweeted.
Stay Tuned for Updates!
Nevertheless, Hackread.com is closely monitoring the situation, and this article will be updated accordingly, taking into account any responses from Plume and in the event that the hackers decide to leak the entire trove of data.
RELATED ARTICLES
- IBM Notifies Janssen CarePath Customers of Data Breach
- Human Error: Casio ClassPad Data Breach Impacting 148 Countries
- Sony Data Breach via MOVEit Vulnerability Affects Thousands in US
