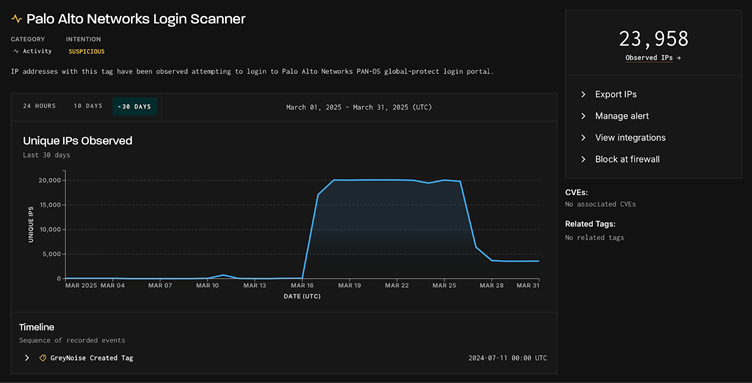
A wave of malicious activity targeting Palo Alto Networks PAN-OS GlobalProtect portals has been observed, with nearly 24,000 unique IPs attempting unauthorized access over the past 30 days.
This coordinated effort, flagged by cybersecurity firm GreyNoise, highlights the growing sophistication of attackers probing network defenses as a precursor to potential exploitation.
GreyNoise detected the surge starting on March 17, 2025, peaking at nearly 20,000 unique IP addresses per day.
While the activity tapered off by March 26, it revealed consistent patterns, with the majority of IP addresses classified as suspicious (23,800) and a smaller subset deemed outright malicious (154).
Bob Rudis, VP of Data Science at GreyNoise, noted this trend aligns with historical patterns linked to the emergence of new vulnerabilities:
“Over the past 18 to 24 months, we’ve observed deliberate targeting of older vulnerabilities, often followed by the discovery of new exploits within weeks.”
Organizations relying on Palo Alto Networks products are urged to secure their login portals immediately, as attackers may be preparing for exploitation.
Key Observations
GreyNoise identified several significant elements in the breach attempt:
Source and Destination Analysis
- Source Countries: The majority of traffic originated from the United States (16,249) and Canada (5,823), with additional activity from Finland, the Netherlands, and Russia.
- Destination Countries: Overwhelmingly targeted systems in the United States (23,768), followed by smaller volumes aimed at the UK, Ireland, Russia, and Singapore.
This global activity underscores a coordinated operation spanning multiple regions.
Top Contributors & Toolkit Indicators
A notable portion of traffic was traced back to 3xK Tech GmbH, responsible for 20,010 IPs under ASN200373.
Other contributors included PureVoltage Hosting Inc., Fast Servers Pty Ltd., and Oy Crea Nova Hosting Solution Ltd.
Three JA4h hashes associated with the login scanner tool were identified:
- po11nn11enus_967778c7bec7_000000000000
- po11nn09enus_fb8b2e7e6287_000000000000
- po11nn060000_c4f66731b00d_000000000000
These hashes indicate a planned and systematic approach to breaching the portals using specialized connection tools.
The incident draws parallels to the 2024 espionage campaign targeting perimeter devices, as reported by Cisco Talos.
Although the methods differ, both events emphasize the critical need for organizations to monitor and defend edge devices.
Recommendations for Organizations
Experts have urged businesses to act swiftly:
- Audit March Logs: Review activity for unusual access attempts.
- Perform Threat Hunts: Analyze systems for potential compromises or suspicious processes.
- Block Malicious IPs: Use actionable intelligence to minimize exposure.
In light of the probing behavior, ensuring robust defenses around exposed Palo Alto Networks portals is essential to thwart future exploitation attempts.
The rise in coordinated attacks against critical network systems serves as a stark reminder of the importance of proactive cybersecurity measures in a constantly evolving threat landscape.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!
