FortiGuard Labs discovers Winos 4.0 malware targeting Taiwan via phishing. Learn how this advanced threat steals data and how to protect your Windows system.
Fortinet’s FortiGuard Labs has disclosed details of a new malware campaign targeting Taiwanese businesses. Reaching out to Hackread.com on this discovery, prior to its publishing on Thursday, researchers revealed that this campaign was discovered in January 2025 and deployed a highly advanced malware framework, known as Winos 4.0. This attack exhibited a high severity level, and utilized a multi-stage infection process, ultimately aiming to steal sensitive information for future malicious activities.
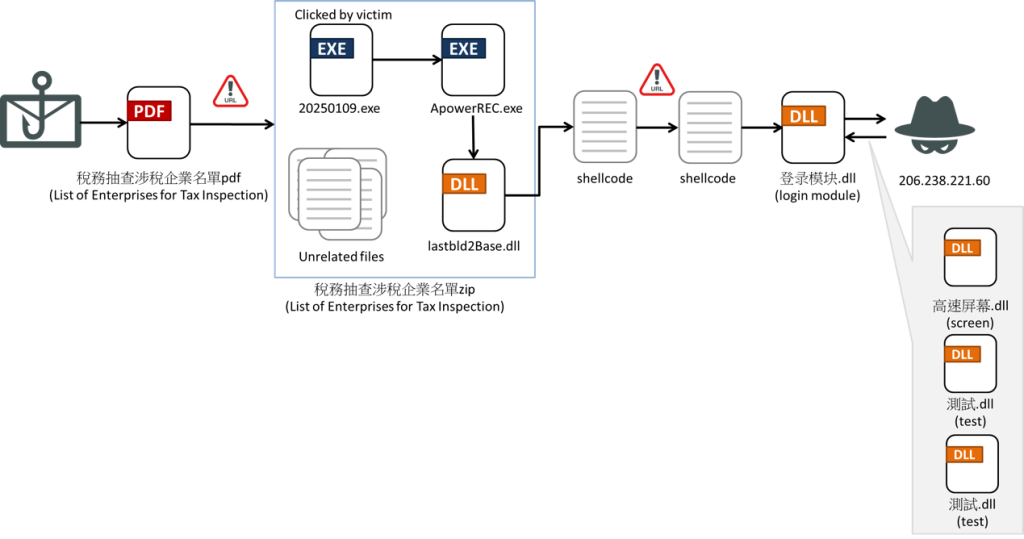
Further probing revealed that this malware specifically targeted Microsoft Windows platforms. A phishing email, carefully crafted to impersonate Taiwan’s National Taxation Bureau, served as the initial attack vector. This deceptive email claimed to contain a list of companies scheduled for tax inspections, urging recipients to forward the information to their financial departments. The attached file, disguised as an official document from the Ministry of Finance, contained a malicious DLL for the next attack stage.
The attack unfolded through a series of executable and dynamic link library (DLL) files. The ZIP file contained files that executed in a sequence: 20250109.exe, ApowerREC.exe, and lastbld2Base.dll.
“20250109.exe is a launcher originally used to execute the actual APowerREC.exe in ./app/ProgramFiles. The attacker created the same folder structure in the ZIP file and used a loader to replace ApowerREC.exe. The fake ApowerREC.exe does nothing but call a function imported from lastbld2Base.dll,” researchers explained in the blog post.
This DLL decrypts and executes shellcode, which contains configuration data including the command-and-control (C2) server address. The shellcode further implements optional features, such as permission escalation, anti-sandbox techniques (e.g. taking multiple screenshots to detect user activity, delaying execution if no user interaction was detected), and process window hiding. The malware downloads encrypted shellcode and the core Winos 4.0 module from the C2 server. This data was stored within the system’s registry for later decryption and execution.
The module initiates several malicious tasks, such as establishing persistence, bypassing UAC (User Account Control), collecting system information (including computer name, operating system version, and installing antivirus software), and disabling screen savers and power-saving features on the infected system.
In addition, the malware actively monitors and manipulates user activity. This includes capturing screenshots, logging keystrokes and clipboard contents (even connected USB devices with their insertion and removal logs), and modifying clipboard data based on predefined rules. It can also disable network connections for security software. Alternative attack chains were also observed, involving Python scripts and further shellcode injection techniques. These variations demonstrate the flexibility and adaptability of the Winos 4.0 framework.
Protecting yourself from sophisticated malware like Winos 4.0 requires being highly suspicious of unsolicited emails, especially those with attachments or links, avoiding opening compressed files (ZIP, RAR) attached to emails, as they are often used to deliver malware, and enabling real-time scanning to detect and block threats before they can infect your system.
Experts Comments
“This attack follows a classic phishing pattern but with a fun twist around the trusted authority to invoke a reaction,” explains J. Stephen Kowski, Field CTO at SlashNext. “The threat actors cleverly exploit human psychology by creating urgency and curiosity, making recipients more likely to download malicious content.”
Beyond email security, Kowski highlights the importance of a multi-layered approach to defence. “Most organizations are now using managed file transfer systems that require registration and internal approval while simultaneously blocking zip attachments altogether. Combining user education with advanced threat detection technologies is key to stopping sophisticated social engineering attempts before they reach inboxes.”
