IN THIS ARTICLE:
- Hackers’ Claims: IntelBroker released a second batch of extracted Cisco data, amounting to 4.84 GB, from the October 2024 breach, claiming it is part of a 4.5 TB trove.
- Leaked Data Contents: The data includes sensitive files such as software artifacts, network configurations, testing logs, cloud server images, and cryptographic signatures, exposing intellectual property and operational insights.
- Misconfigured Resource Exploitation: The data originated from a misconfigured, public-facing DevHub resource left exposed without password protection, allowing hackers to download it.
- Cisco’s Response: Cisco acknowledged the incident, stated public access was disabled, and confirmed no servers were breached or sensitive data compromised, though hackers contest this claim.
- IntelBroker’s Track Record: The hacker, known for breaching Apple, AMD, Europol, and others, highlights ongoing exploitation of misconfigured systems, a persistent issue in cybersecurity.
Hackers have released what they claim to be the second batch of data stolen in the alleged Cisco data incident from October 2024. According to IntelBroker, the hacker behind the breach, the latest leak, published on Christmas Eve on Breach Forums, contains 4.84 GB of data, part of an allegedly stolen 4.5 TB.
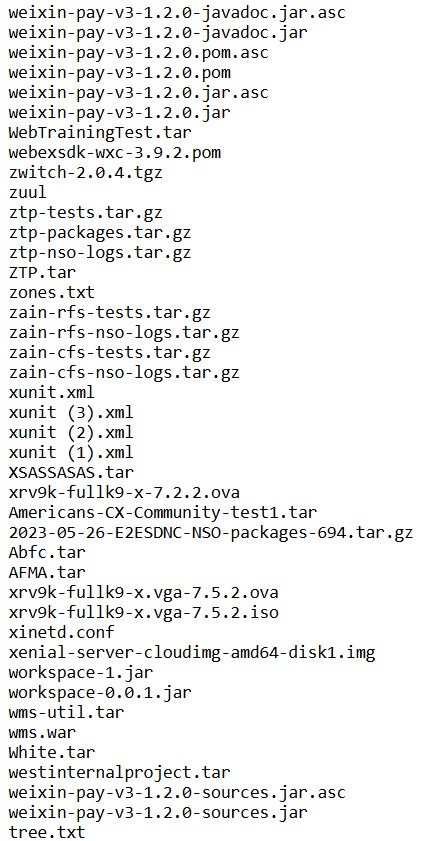
As seen by Hackread.com, the leaked data includes a trove of sensitive files, such as proprietary software development artifacts like Java binaries, source code, and application archives; network-related files including Cisco XRv9K virtual router images and configurations; testing logs and scripts; operational data such as Zero Touch Provisioning (ZTP) logs and packages; cloud server disk images; and cryptographic signatures for payment SDKs like Weixin Pay.
Additionally, the leak contains configuration files, internal project archives, and other miscellaneous documents, potentially exposing intellectual property, network configurations, and operational insights.
Background
Notably, the leaked data originates from a misconfigured, public-facing DevHub resource that Cisco reportedly left exposed without password protection or security authentication, enabling the hackers to download the entire dataset in October 2024.
IntelBroker who accessed the misconfigured server claims they managed to extract 4.5TB of information. The first part of the data leak, which included 2.9 GB of files, was published on December 17, 2024.
Cisco’s Response
Cisco acknowledged (PDF) the October 2024 incident and stated that public access was disabled. The company also confirmed that none of its servers were breached and no sensitive data was compromised. However, the hackers claim otherwise, particularly regarding the extracted data.
Regarding the latest leak, Cisco noted on its incident response page that it is aware of the claims made by IntelBroker, asserting that the data published this time also stems from the October 14, 2024, incident.
“On Wednesday, December 25, 2024, at 17:07 EST, the threat actor IntelBroker posted on X about releasing more data. At 17:40 EST, IntelBroker released 4.45 GB of data for free on BreachForums. We have analyzed the post data, and it aligns with the known data set from October 14, 2024.”
Cisco
Intel Broker and Previous Breaches
Intel Broker is known for high-profile data breaches. In June 2024, the hacker claimed to have breached Apple Inc., stealing source code for internal tools. The same hacker boasted about breaching AMD (Advanced Micro Devices, Inc.), and stealing employee and product information.
In May 2024, Intel Broker hacked Europol, a breach that the agency later confirmed. Some of the hacker’s previous data breaches are listed below:
Nevertheless, the partial leak goes on to show ongoing exploitation of misconfigured systems and exposed data. The scale of exploitation is evident, as even high-profile hackers like ShinyHunters and Nemesis have targeted misconfigured servers and S3 buckets.
RELATED TOPICS
- IntelBroker Claim Access to Nokia Internal Data, Selling for $20K
- Europol Hacked: IntelBroker Claims Major Law Enforcement Breach
- IntelBroker Space-Eyes Breach, Targeting US National Security Data
- IntelBroker Claims Breach of Top Cybersecurity Firm, Selling Access
- AMD Data Breach: IntelBroker Claims Theft of Employee, Product Info
