Cybercriminals exploit fake YouTube links to redirect users to phishing pages, stealing login credentials via URI manipulation and layered obfuscation techniques.
According to a recent discovery by cybersecurity analysts at ANY.RUN, cybercriminals have been leveraging fake YouTube links to redirect unsuspecting users to phishing pages, stealing login credentials in the process. This attack employs Uniform Resource Identifier (URI) manipulation to obscure malicious intent while maintaining the appearance of authenticity.
Let’s take a closer look at the details of this attack and how understanding these techniques can allow your company to strengthen its protection against similar threats.
How Fake YouTube Links Work in This Attack
Cybercriminals behind this campaign have implemented a clever manipulation of the Uniform Resource Identifier (URI) to deceive users. At first glance, the malicious URLs appear trustworthy, often starting with legitimate-looking strings such as http://youtube. This approach relies on the human tendency to trust familiar domains while hiding the true destination of the link.
To see how this works, let’s look at an analysis session using ANY.RUN’s interactive sandbox. By safely running a sample of the malicious YouTube URL in a secure environment, the full picture of the attack is revealed.
Unlike traditional methods that might require juggling multiple tools to analyze different stages of an attack, this sandbox makes it easy to uncover every step of the chain in one place.
View analysis session
In the following analysis session, the malicious link is distributed via email. The victim receives an email prompting them to “View Completed Document,” which seems like a legitimate action. However, the link embedded in the email has been cleverly replaced with recognizable domain names to appear trustworthy.
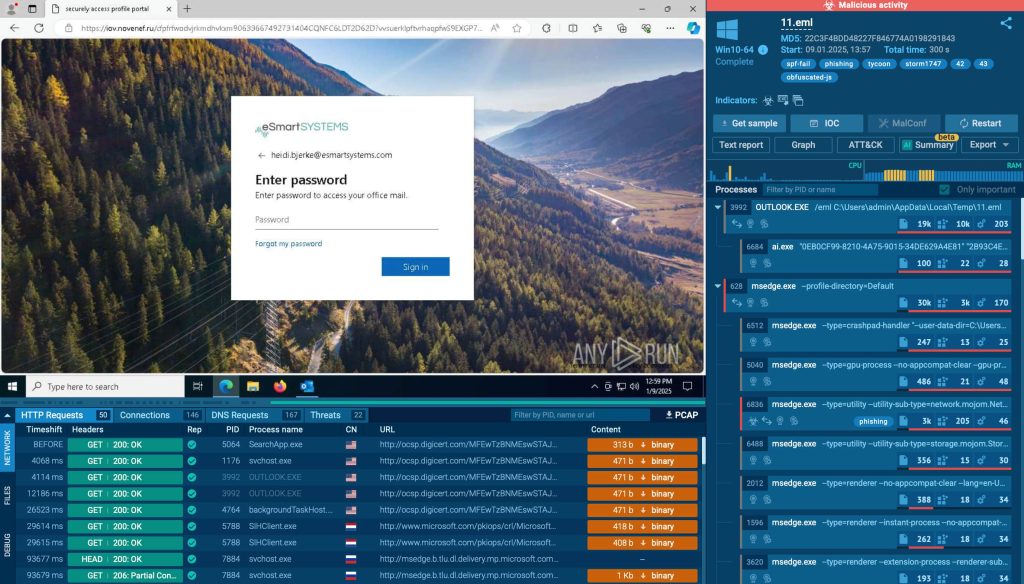
While the URL looks authentic at first glance, clicking on it redirects the victim to a phishing page designed to harvest their login credentials. This subtle manipulation is highly effective, exploiting the natural tendency of users to trust familiar-looking links, making it even more dangerous.
Save time and effort by identifying malicious content before it can harm your company. ANY.RUN provides a 14-day free trial for security teams to try advanced malware analysis.
Layered Obfuscation Techniques
In addition to URI manipulation, attackers deploy layered redirections to evade detection by automated tools and users alike.
These redirections often involve multiple intermediate domains, further concealing the final phishing page. By the time a user reaches the actual site, their guard is often lowered, and the phishing page looks nearly indistinguishable from the legitimate one.
For instance, the attack mentioned above attack cleverly incorporates a fake Cloudflare verification page to enhance its credibility. Once the victim clicks the link, they are greeted with what appears to be a routine Cloudflare check, complete with loading animations and prompts that mimic legitimate browser security processes.
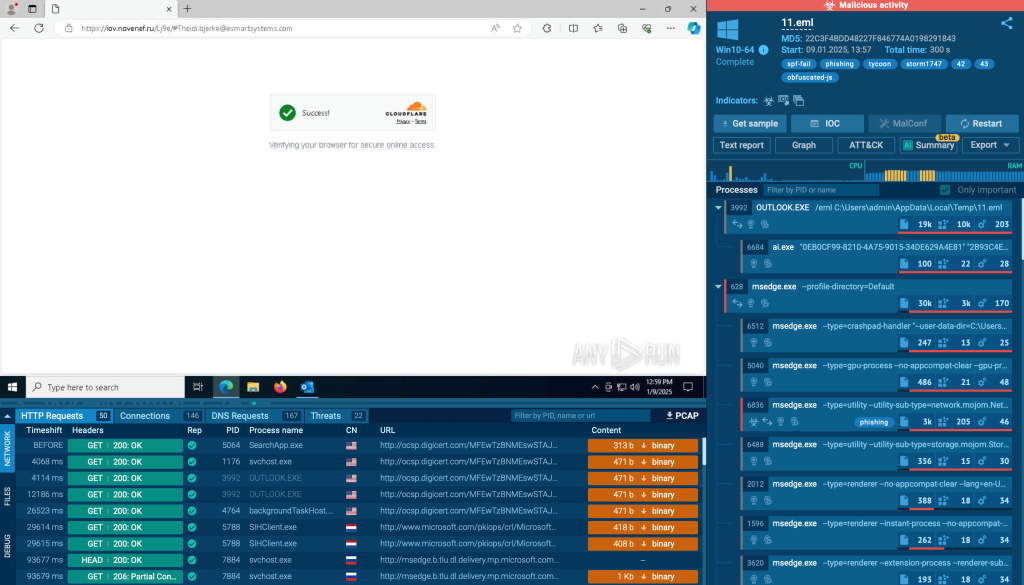
This added layer of deception is designed to disarm suspicion, making the victim believe they are navigating through a secure and trusted environment. By the time the user reaches the phishing page, they are more likely to enter their login credentials without questioning its authenticity.
Phishing Kits and Infrastructure
This campaign is connected to the Storm1747 group, which relies on a well-organized domain infrastructure to carry out its attacks. Their setup includes checkers, redirectors, and main phishing pages, all built using standardized templates from the Tycoon 2FA phishing kit.
These ready-to-use components make it easier for attackers to deploy large-scale phishing campaigns quickly and efficiently.
One of their key tricks is replacing the user info field in URLs, a clever tactic that makes malicious links look legitimate. This technique isn’t exclusive to Storm1747; it’s also used in other phishing kits like Mamba 2FA and EvilProxy, which are designed to create convincing fake login pages.
Collecting IOCs Related to the Attack
In tools like ANY.RUN’s sandbox and indicators of Compromise (IOCs) such as malicious URLs, file hashes, and IP addresses are neatly organized in the upper-right corner of the interface. This arrangement makes it easier to analyze and understand key details about the attack.
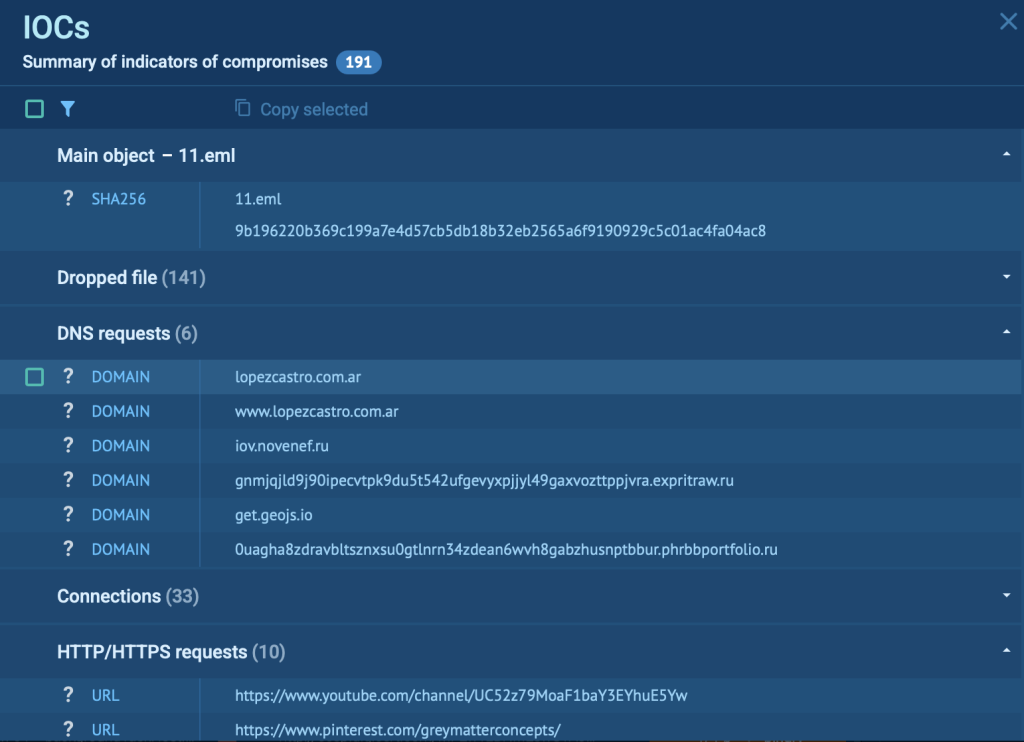
You can gather and review everything in one place, helping businesses piece together how the attack works and how to better prepare for similar threats in the future.
Get the Fastest Detection of Malware with ANY.RUN Sandbox
Attacks like this one demonstrate the need for advanced tools that go beyond basic detection to uncover every layer of an attack. With ANY.RUN’s interactive sandbox, you don’t waste time juggling multiple tools or building complex setups. Instead, you get a powerful, cloud-based platform that allows you to detect and analyze threats directly from your browser.
Everything is designed with convenience in mind; no infrastructure maintenance, no extra software. Just real-time insights into files, links, and full attack chains, available whenever you need them.
RELATED TOPICS
- A Step-by-Step Guide to How Threat Hunting Works
- How Attackers Use Corrupted Files to Slip Past Security
- Malware in Fake Business Proposals Hits YouTube Creators
- Rockstar 2FA Phishing-as-a-Service Kit Targets MS365 Accounts
- YouTube Channels Hacked to Spread Lumma via Cracked Software
