A cyber-espionage group known as Ashen Lepus has been actively using a new set of malicious tools called AshTag to attack government and diplomatic offices across the Middle East, according to a recent report by the cybersecurity firm Palo Alto Networks’ Unit 42. This group, which has been linked to Hamas and is also tracked under the name WIRTE, has been, reportedly, conducting intelligence-gathering campaigns since 2018.
A Relentless Spying Campaign
Researchers noted that, unlike other similar groups whose activity slowed down during the Israel-Hamas conflict, Ashen Lepus “remained persistently active” and continued its operations even after the October 2025 Gaza ceasefire.
Initially, researchers observed the group focused on countries geographically close to the Palestinian Territories, such as the Palestinian Authority, Egypt, and Jordan. However, further investigation revealed a notable expansion in their targets, now including Oman and Morocco.
Regarding the attack method, the report reveals that the hackers rely on documents disguised as news or reports about Middle Eastern geopolitical affairs to trick their victims and distribute them via file-sharing services.
These themes, sometimes referencing the League of Arab States or the UN Security Council, are delivered via an initial “benign PDF file” that guides targets to a file-sharing service to download the actual malicious file. Lately, their bait has included more subjects related to Turkey and its relationship with the Palestinian administration.
AshTag Malware Analysis and Attack Chain
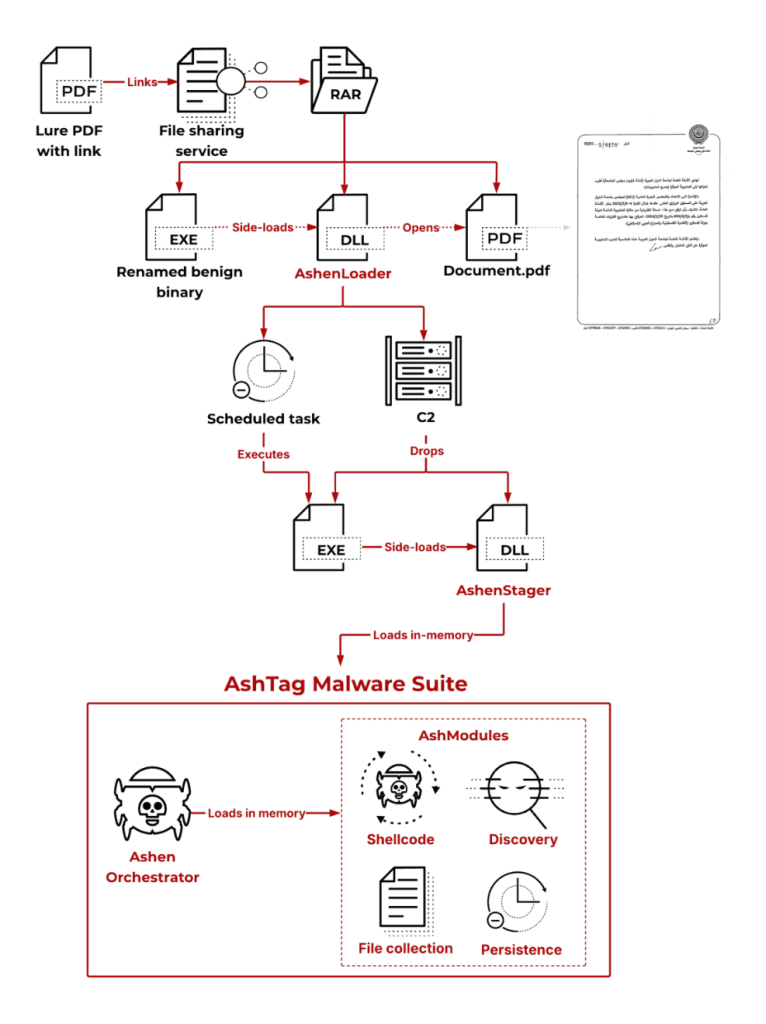
The new AshTag malware suite, the core element of this campaign, is designed to steal files and remotely run commands on a victim’s computer. The infection begins when the initial lure leads the target to download a compressed RAR archive, which contains three main components: a fake document, a malicious background program (a loader), and a separate, harmless PDF named Document.pdf.
When the victim opens the fake document, the malicious loader is quietly launched in the background, which then instantly displays Document.pdf. This clever move makes the target believe they successfully opened the file while the actual malware, which Unit 42 calls AshenOrchestrator, is loaded unseen.
It is worth noting that the group is becoming better at hiding its activity. They disguise the malware’s communication to look like normal internet traffic, for example, by using innocent-sounding website addresses like api.healthylifefeed.com.
Furthermore, the attackers are running their malicious software directly inside the computer’s memory (in-memory execution), which helps them avoid leaving behind evidence that security tools usually look for.
This effort to improve operational security helps them evade detection. Once the AshTag malware successfully infiltrates a system, the hackers engage in “hands-on data theft,” accessing specific diplomacy-related documents, often from the victim’s email accounts, before stealing them. Organisations in the Middle East, especially those in the governmental and diplomatic sectors, are urged to remain aware of this continuous and evolving threat.
