IntelBroker hacker leaks data linked to US contractor Acuity Inc., exposing potentially sensitive intelligence agencies-related data – US government previously denied Acuity Inc. breach, but experts warn of national security risks.
The notorious IntelBroker hacker and their affiliates have leaked a trove of sensitive records, which they claim jeopardize the United States national security. The data, leaked on Breach Forums, is linked to US Federal contractor Acuity Inc., in a data breach allegedly carried out in March 2024. The data was previously being sold for just $3,000 in Monero (XMR) cryptocurrency.
As seen by Hackread.com, IntelBroker has classified the breach as a “National Security Documents Leak,” involving documents from the “Five Eyes Intelligence Group.” The leaked records now accessible to the public include highly sensitive information such as full names, email addresses, office numbers, personal cell numbers, email addresses (government, military, and Pentagon), classified information, and communications between the Five Eyes, 14 Eyes, and the US’s allies.
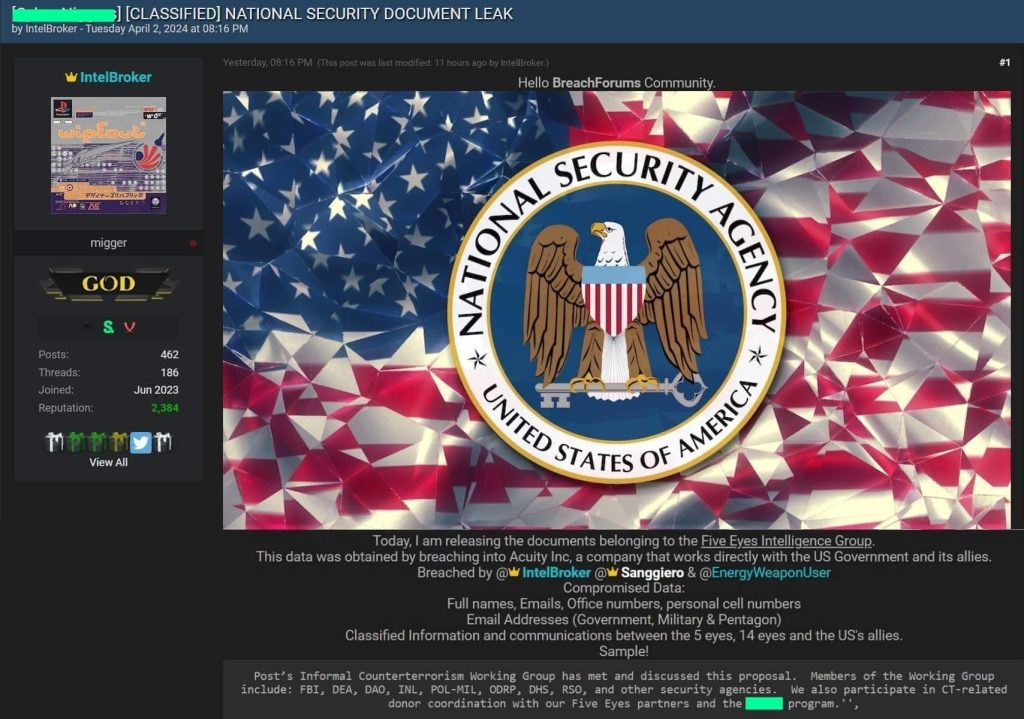
For your information, The Five Eyes Intelligence Group is an intelligence alliance including five English-speaking countries: the United States, the United Kingdom, Canada, Australia, and New Zealand. The alliance aims to share intelligence and collaborate on signals intelligence (SIGINT) gathering, surveillance, and cybersecurity activities.
Background of the alleged Acuity Inc. data breach
On March 4, 2024, Hackread.com published an exclusive report on a data breach allegedly involving Acuity Inc., a federal contractor based in Reston, Virginia. The breach was claimed by IntelBroker.
The hacker claimed the use of a zero-day security vulnerability in GitHub to access Acuity Inc.’s tokens and facilitate their malicious activities, including the theft of data belonging to U.S. Citizenship and Immigration Services (USCIS) and U.S. Immigration and Customs Enforcement (ICE).
Hackread.com reported the breach to GitHub, Acuity Inc., ICE, and USCIS. However, none of the organizations responded to the report. In contrast, Homeland Security, responding to a third-party media site that had not reported on the incident or analyzed the data, denied IntelBroker’s claims and labelled the breach as false, categorizing the leaked information as “test demos for vendors” with fake names and contact information used solely to provide examples of received data.
Now What?
Despite the US Government’s version that the data leak is fake, Hackread.com’s analysis suggests that the publicly leaked information remains highly consequential. Even if the data is fabricated, it exposes the modus operandi of US intelligence agencies and their allies, potentially risking their operational security and strategies.
I will say again: data like this can’t be faked unless it’s copy paste from different and previous leaks which is highly unlikely based on IntelBroker’s previous attacks.
Also, their availability on twitter should be good for OSINT researchers, no? https://t.co/6CkYBp07Ua
— Waqas (@WAK4S) April 3, 2024
IntelBroker
The hacker’s origins and affiliates are unknown; however, according to the United States government, IntelBroker is alleged to be the perpetrator behind one of the T-Mobile data breaches.
Additionally, IntelBroker is known for targeting high-profile targets in the United States. Some of their previous data breaches include Las Angeles Intl. Airport, US DoD Documents, Staffing Giant Robert Half, Facebook Marketplace Database, DARPA-related accesses in General Electric breach, Weee! Grocery and several others.
RELATED TOPICS
- US Govt’s secret terrorist watchlist with 2M records exposed online
- Chinese Group Storm-0558 Hacked European Govt Emails, Microsoft
- Adobe ColdFusion Flaw Used by Hackers to Access US Govt Servers
- Traffic sign near ICE headquarters hacked with “Abolish ICE” message
- Norweigian researcher exposes how a US firm collected his location data




