Croatia’s biggest hospital, Zagreb Univ. Hospital Centre, was crippled by ransomware attack. LockBit 3.0 forced shutdown and data breach. Patients diverted, medical reports handwritten. Investigation underway.
A cyberattack crippled the University Hospital Centre Zagreb (KBC Zagreb), Croatia’s largest and most advance hospital, on June 27th, 2024. The attack was a ransomware incident perpetrated by the LockBit 3.0 group, which forced the hospital to shut down its entire IT infrastructure to prevent further damage.
The attack severely disrupted the hospital’s digital systems, incapacitating its networks and forcing emergency patients to be diverted to other Zagreb hospitals.
“They shut down all the servers, so that the virus would not spread. They informed all the external companies that do protection and started an investigation to see what happened,” said Milivoj Novak, KBC Zagreb’s assistant director of health care quality and supervision.
The publicly funded teaching hospital was back online just 24 hours later, and over 100 experts were tasked with restoring IT systems to full functionality. However, the incident caused significant setbacks and delays, taking the facility back “50 years – to paper and pencil,” as per Croatian Radio.
Hospital staff had to hand-write medical reports instead of printing them, causing some patients to be redirected to other hospitals. An initial investigation confirmed patients’ medical records were not compromised.
The Russian ransomware group, LockBit, compromised the hospital using LockBit 3.0 virus and demanded a yet undisclosed ransom amount by July 18.
The group claims to have stolen a large cache of files including “medical records, patient exams, research papers, surgery data, organ and donor data; organ and tissue banks; employee data, addresses phone numbers etc.; employee legal documents; data on donations and relationships with private companies; donation book; medication reserve data; personal data breach reports and much more.”
The group uploaded an alleged sample of its stolen wares, consisting of 12 documents, as proof of exfiltration. The hospital has not confirmed the data involved but has notified authorities and initiated a criminal investigation to determine its impact.
The LockBit cybercriminal gang, active since 2019, operates a Ransomware-as-a-Service model. Despite a setback in Operation Cronos, led by the FBI and Interpol, LockBit continues to remain relevant, with Evolve Bank and Trust being its recent victim.
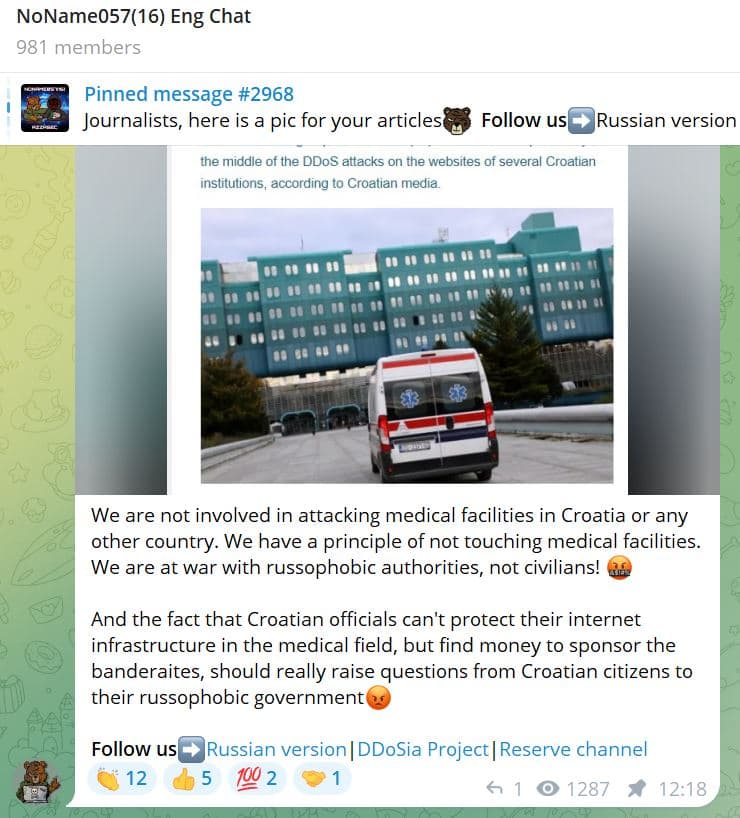
NoName057(16), another Russian hacktivist group responsible for around one-third of all hacktivist attacks in 2023 including attacks on Croatian government’s finance and Central Bank’s websites a day before, was initially suspected of causing the hospital outage. However, the group denied involvement in attacking medical facilities in Croatia or any other country.
“We have a principle of not touching medical facilities. We are at war with russophobic authorities, not civilians!” NoName wrote in its Telegram post on June 28th.
RELATED TOPICS
- Ransomware attack on hospital causes patient’s death
- CISA warns of disruptive ransomware attacks on US hospitals
- Ransomware Attack Disrupts Services in 18 Romanian Hospitals
- London NHS Crippled by Ransomware, Several Hospitals Targeted
- Hacker group busted while planning to hit hospitals with ransomware
