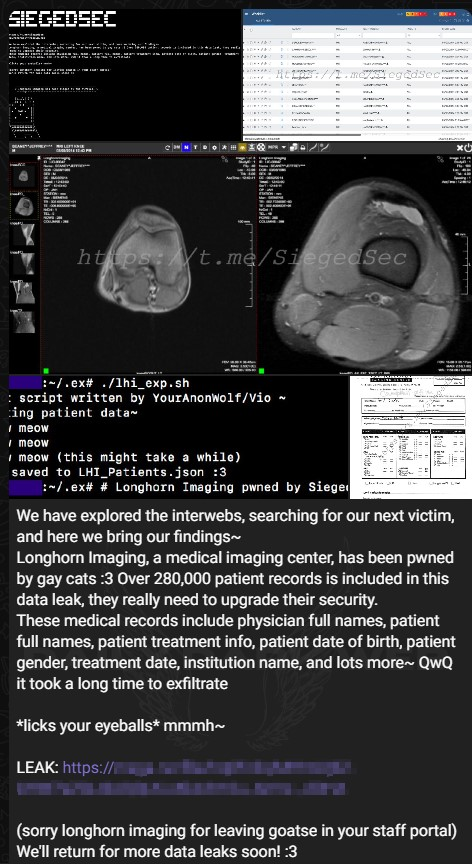
Longhorn Imaging, a prominent medical imaging service, has allegedly fallen victim to a cyber attack by the notorious hacker group SiegedSec.
The group has claimed the Longhorn cyber attack and asserts that they have successfully infiltrated the company’s systems, compromising an extensive database containing more than 280,000 patient records.
Daily Dark Web, a threat intelligence service that monitors illicit activities on the internet, shared the details of the Longhorn cyber attack.
In a Twitter post, Daily Dark Web shared a screenshot of the statement made by the threat actor responsible for the Longhorn data breach.
The Cyber Express reached out to the US-based medical imaging center to confirm the Longhorn cyber attack claims. However, at the time of writing, we did not receive an official response from the company.
The Longhorn data breach has added more weight to the ongoing concerns about the US medical attacks and the overall security of patient data in the US healthcare sector.
Longhorn data breach and the threat actor’s post
The statement posted by the threat actor appeared on a dark web forum, typically used by cybercriminals to share stolen data and boast about their exploits. The post included a link to a data leak, suggesting that the compromised patient records from the Longhorn data breach have been stored and made available for unauthorized access.
The leaked data reportedly includes a vast range of sensitive information such as full names of physicians and patients, patient treatment details, dates of birth, genders, treatment dates, institution names, and various other details pertaining to patient healthcare.
The threat actor behind the Longhorn cyber attack on a US-based medical imaging service expressed satisfaction at the exfiltration of this information, hinting at the extensive efforts and time it took to carry out the Longhorn data breach.
The implications of this alleged breach are grave, as the compromised data could potentially be exploited for various nefarious purposes.
Patient records contain highly personal and confidential information, making them a prime target for cybercriminals seeking to engage in identity theft, financial fraud, or even extortion.
Moreover, such breaches can erode patients’ trust in medical service providers, jeopardizing the reputation of Longhorn Imaging and the overall confidence in the healthcare industry’s ability to protect sensitive data.
Cyber attack on Longhorn and US medical center breaches: What’s the next step?
Apart from the latest Longhorn data breach in this case, to combat the ongoing battle against hacker groups targeting medical facilities, UpGuard has shared its “Ultimate Cybersecurity Guide for Healthcare in 2023” guide.
The report highlights the prevalence of data breaches in healthcare organizations and emphasizes the importance of basic cybersecurity practices in preventing such incidents.
The guide focuses on mitigating cybersecurity risks and enhancing data breach resilience through a tailored cybersecurity program.
It suggests performing a risk assessment to identify areas for improvement and define a risk appetite that sets the maximum level of security risks an organization is willing to tolerate.
It also provides security responses and recommended controls for each stage of a ransomware attack, including phishing prevention, multi-factor authentication, endpoint detection and response, and network segmentation.
The guide explains the difference between regulations and cybersecurity frameworks and highlights the importance of compliance with the Health Insurance Portability and Accountability Act (HIPAA) in the healthcare industry.
The report also provides an overview of HIPAA’s privacy and security rules and outlines administrative, physical, and technical safeguards necessary for compliance.
UpGuard’s report concludes by emphasizing the need for healthcare organizations to adopt cybersecurity frameworks such as the NIST Cybersecurity Framework and HITRUST to enhance their security posture and meet regulatory requirements like HIPAA.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
