According to Check Point Research’s (CPR) latest report, cybercriminals spent the second quarter of 2025 impersonating the world’s most familiar brands to steal credentials and payment information. The data shows a mix of predictable targets and a few surprising returns, with Spotify reappearing as a key lure for the first time in years.
Microsoft once again topped the list, featuring in a quarter of all phishing attacks during Q2. Tech brands remained the primary focus, but cybercriminals also went after streaming services and travel platforms that people use daily without a second thought.
While the latest research shows Meta no longer at the top as it was in 2024, Microsoft taking the lead again doesn’t come as a surprise. As of 2025, over 1.6 billion people were using the Windows operating system. On top of that, Microsoft 365 had around 345 million paid subscribers and roughly 321 million active users each month.
That massive user base is exactly why Microsoft Office was the most targeted software in malware attacks back in 2022. It also explains why Microsoft was the most impersonated brand in phishing campaigns during Q2 2023, and why it has returned to the top spot now.
Spotify’s return to phishing charts for the first time since 2019 was linked to a spoofing campaign that mimicked the company’s login flow almost perfectly. The fake page, hosted on a malicious URL, asked victims to input credentials before redirecting them to a counterfeit payment form. Both the design and branding were polished enough to fool unsuspecting users, many of whom may have believed they were logging into their real account.

This renewed targeting of entertainment services shows attackers aren’t just looking at corporate systems anymore. Everyday platforms with large user bases are just as likely to be exploited, especially when those users are less suspicious of messages related to subscriptions or media.
Booking.com was also hit by a surge in impersonation. Researchers flagged over 700 newly registered domains with names resembling real booking confirmation URLs. Compared to previous quarters, that’s a spike by a factor of 100.
As Hackread.com reported on multiple occasions, most recently in June 2025, Booking.com was abused in a ClickFix email scam. Back in April 2025, another ClickFix scam exploited Booking.com to infect unsuspecting users with AsyncRAT.
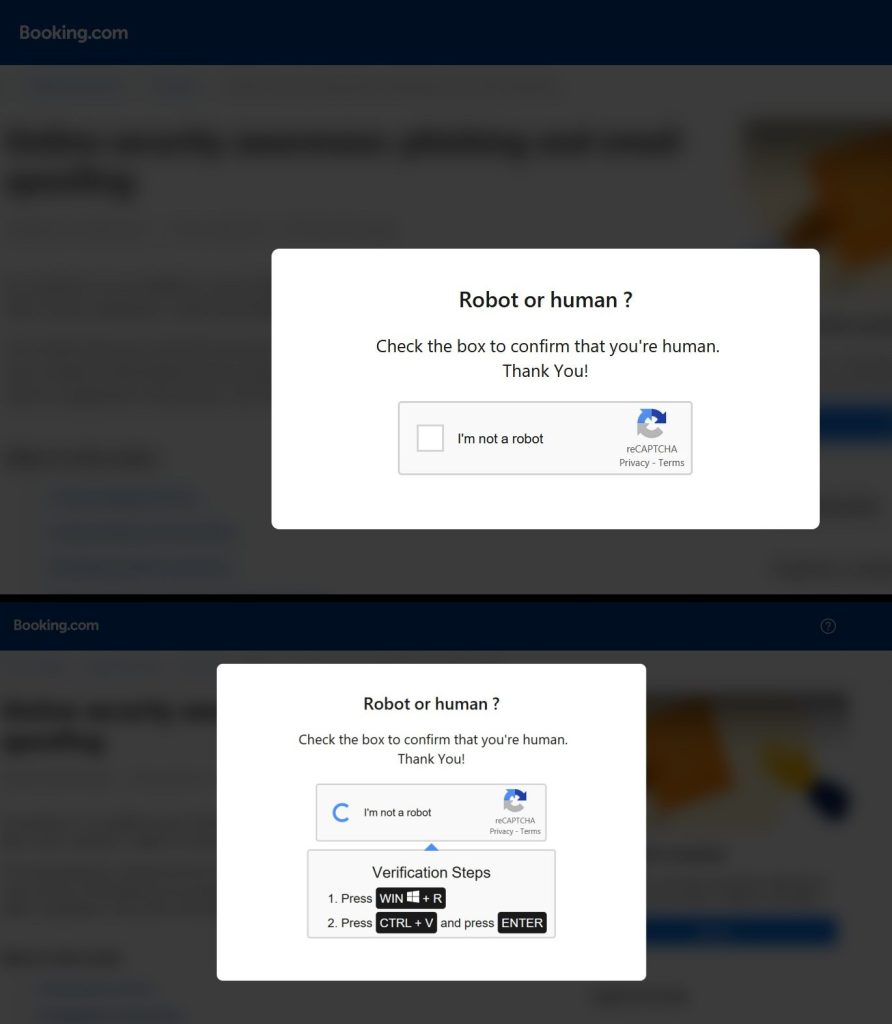
These scams used personal details like names and email addresses to create urgency. While the domains have since been taken down, the approach revealed how much more personalised phishing tactics have become.
Outside these two cases, as per CPR’s report, the overall trend remains predictable. The tech sector continues to be the most impersonated, with Microsoft, Google, and Apple taking the top three spots.
Social media platforms like LinkedIn, WhatsApp, and Facebook remain common targets, while retail and travel services like Amazon and Booking.com round out the top ten. It is worth noting that CPR’s report
If you use any of these services, keep in mind that phishing campaigns count on people clicking without thinking. A few simple steps can help protect your data. Start by using multi-factor authentication, double-check URLs, run suspicious links through VirusTotal before opening them, and don’t get caught up in the urgency scammers try to create.
For businesses, keep employees informed and alert on cybersecurity, since phishing is still one of the easiest ways attackers gain access to internal systems. And finally, for ongoing updates and insights on cybersecurity, make sure to follow Hackread.com.
