Microsoft on Thursday flagged a cross-platform botnet that’s primarily designed to launch distributed denial-of-service (DDoS) attacks against private Minecraft servers.
Called MCCrash, the botnet is characterized by a unique spreading mechanism that allows it to propagate to Linux-based devices despite originating from malicious software downloads on Windows hosts.
“The botnet spreads by enumerating default credentials on internet-exposed Secure Shell (SSH)-enabled devices,” the company said in a report. “Because IoT devices are commonly enabled for remote configuration with potentially insecure settings, these devices could be at risk to attacks like this botnet.”

This also means that the malware could persist on IoT devices even after removing it from the infected source PC. The tech giant’s cybersecurity division is tracking the activity cluster under its emerging moniker DEV-1028.
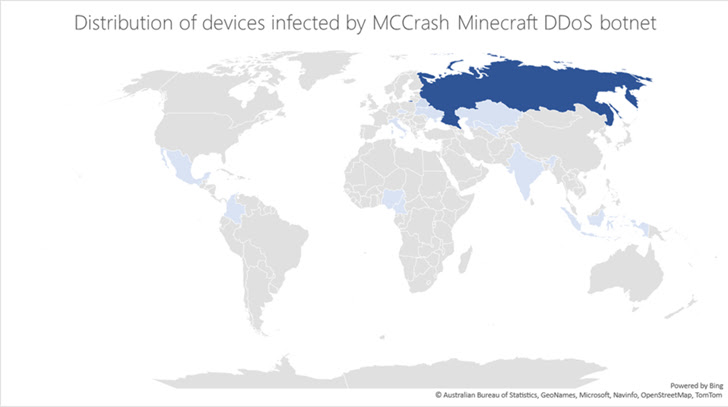
A majority of the infections have been reported in Russia, and to a lesser extent in Kazakhstan, Uzbekistan, Ukraine, Belarus, Czechia, Italy, India, Indonesia, Nigeria, Cameroon, Mexico, and Columbia. The company did not disclose the exact scale of the campaign.
The initial infection point for the botnet is a pool of machines that have been compromised through the installation of cracking tools that claim to provide illegal Windows licenses.
The software subsequently acts as a conduit to execute a Python payload that contains the core features of the botnet, including scanning for SSH-enabled Linux devices to launch a dictionary attack.
Upon breaching a Linux host using the propagation method, the same Python payload is deployed to run DDoS commands, one of which is specifically set up to crash Minecraft servers (“ATTACK_MCCRASH”).
Microsoft described the method as “highly efficient,” noting it’s likely offered as a service on underground forums.
“This type of threat stresses the importance of ensuring that organizations manage, keep up to date, and monitor not just traditional endpoints but also IoT devices that are often less secure,” researchers David Atch, Maayan Shaul, Mae Dotan, Yuval Gordon, and Ross Bevington said.
The findings come days after Fortinet FortiGuard Labs revealed details of a new botnet dubbed GoTrim, which has been observed brute-forcing self-hosted WordPress websites.