A massive global network of infected gadgets, Aisuru DDoS Botnet‘s Android variant dubbed Kimwolf, has grown to over 2 million devices since last August, reveals the latest research from the anti-fraud intelligence company Synthient.
Reportedly, hackers are hunting for Android-powered smart TVs and cheap streaming boxes to build a botnet (a private army of infected devices) that they can control remotely and launch Distributed Denial-of-Service (DDoS) attacks. The combined power of these devices has been used to flood and crash major websites with traffic, reaching a record-breaking 29.7 Terabits per second, as per Cloudflare.
The Pre-Infected Trap
What makes this threat particularly tricky is how the devices get infected in the first place. Synthient’s investigation showed a disturbing trend that many of these gadgets are compromised before they even reach your front door.
And, their geographical footprint is even scarier. Research data shows a massive concentration of these zombie devices across the globe, with the highest number of victims found in Vietnam, Brazil, India, and Saudi Arabia. About 67% of these devices were found to be completely unprotected.
Once a user plugs them in and connects to the internet, the hackers can gain access to the home network within minutes. Even more concerning is that when researchers purchased several popular models, including those labelled HiDPTAndroid and generic TV BOX units, they found the malicious code was already running on the devices right out of the box.
Synthient’s investigation into the hackers’ backend monitoring tools, a Grafana instance, confirmed that the network’s growth has skyrocketed in just the last two months. Researchers identified roughly 12 million unique IP addresses associated with the network every single week, which means the system is cycling through a massive pool of home connections
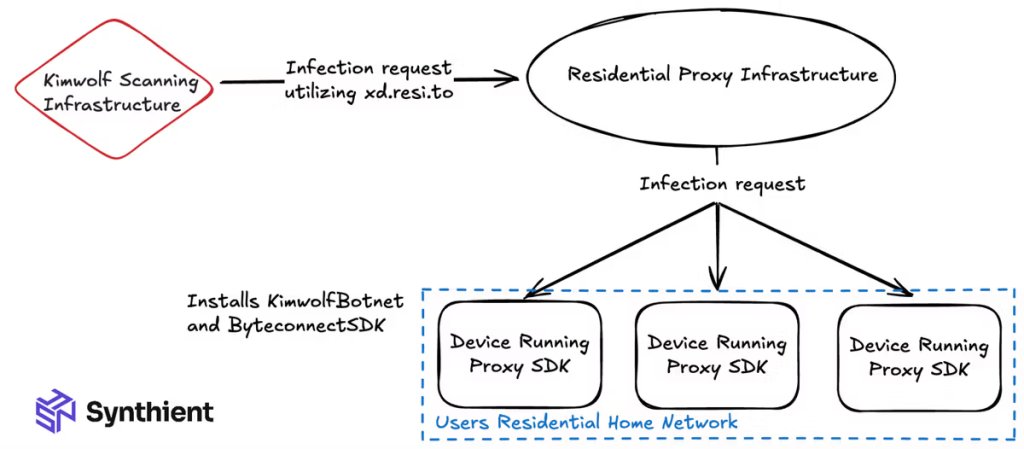

What’s the Objective?
The primary objective of Kimwolf actors is to make money by renting out their home internet’s bandwidth to others for as low as $0.20 per GB, researchers explained in the blog post.
In addition, they use a hidden tool called Byteconnect SDK to secretly install apps on your devices, earning a referral fee for each one without you ever knowing. That’s not all! They operate a DDoS-for-hire service, renting out the entire 2-million-device army to anyone looking to knock a major website offline.
While the provider IPIDEA successfully released a security fix on December 28, 2025, millions of devices still remain part of the network. If you own a “no-name” streaming box and it’s acting slow or strange, the safest bet is to stop using it or even destroy it. You can check if your own connection has been compromised by visiting synthient.com/check.
RELATED TOPICS
- Android TV Box Sold on Amazon Contains Malware
- New malware found targeting IoT devices, Android TV globally
- LG Smart TV Screen Bricked After Android Ransomware Infection
- Hundreds of Android Gaming Apps Tracked Your TV Viewing Habits
- Android TV Boxes Infected with Backdoors, Pwning Home Networks