Cybersecurity researcher finds 4.6M Illinois voter records exposed in unsecured databases. Sensitive data including names, addresses, and SSNs were publicly accessible. Incident highlights vulnerabilities in election data security and potential for misuse. Learn more about the discovery and its implications.
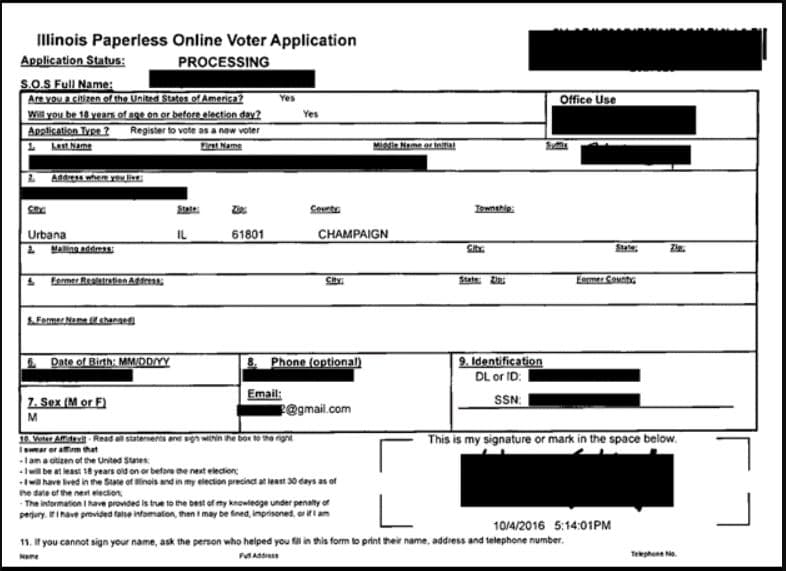
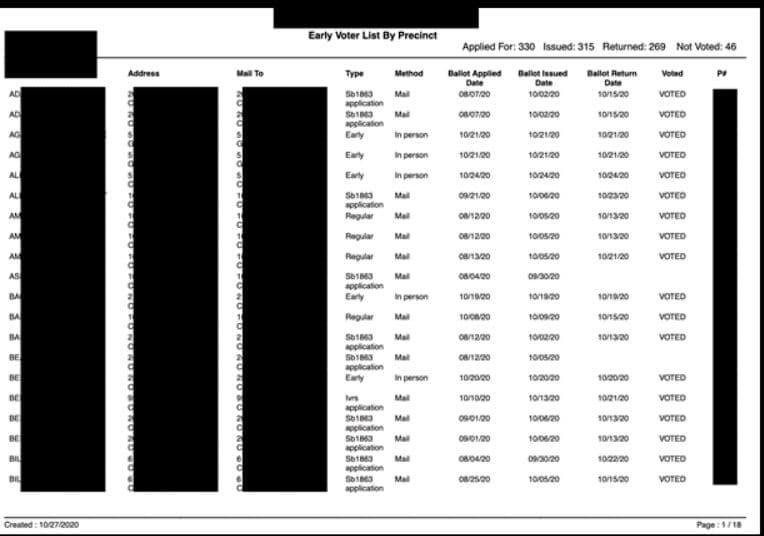
In a recent discovery, cybersecurity researcher Jeremiah Fowler uncovered 13 misconfigured databases containing a staggering 4.6 million documents, including voter records, ballots, and various election-related lists. The exposed data appeared to originate from a single county in Illinois, United States, and was publicly accessible without any password or security authentication.
The US voter data has been leaked online multiple times, often due to server misconfigurations. For example, 191 million voter records were leaked in December 2015, and millions of voter records were circulating on the dark web in January 2016.
Fowler’s investigation began when he identified a database with a collection of sensitive documents, including voter registrations, ballot templates, and voting records. Suspecting that other counties might be inadvertently exposing similar data, Fowler replaced the county name in the database format and discovered a total of 13 publicly accessible databases, along with an additional 15 that were not publicly accessible.
According to Fowler’s findings shared with Hackread.com ahead of publishing on Friday, August 2, 2024, the counties mentioned in the exposed databases have contracts with Platinum Technology Resource, a company offering ballot printing, election management, and voter registration software. Fowler also discovered that Magenium, an Illinois-based technology company, is responsible for the technical support of Platinum Elections Services.
After sending responsible disclosure notices to both Platinum Technology Resource and Magenium, the databases were finally restricted. However, it remains unknown how long the documents were exposed or if any unauthorized access occurred.
The exposed databases contained a wide range of sensitive information, including full names, physical addresses, email addresses, dates of birth, Social Security Numbers (full and partial), driver’s license numbers, and historical voting records. Additionally, the databases held copies of voter registration applications, death certificates, and records of changes in address, jurisdiction, or state.
Fowler emphasizes the importance of maintaining public trust in the electoral process, especially in the wake of the 2020 election, when the integrity of the process was questioned. He believes that any assertions of unfair elections could potentially harm civic engagement and trust in the democratic process.
While Fowler found no evidence of wrongdoing or suspicious activity in the limited sample of documents he reviewed, he stresses the importance of protecting election data from cyber attacks, which could include tampering with documents or using exposed voter information for fraud or misinformation.
The potential risks associated with exposed personally identifiable information (PII) and sensitive data extend beyond the political sphere. Criminals could exploit this information for identity theft, financial fraud, and targeted social engineering attacks.
“The potential risk of a coordinated disinformation campaign using voter lists and voter registrations is a serious concern,” Fowler noted. “Having PII of voters would potentially allow malicious actors to send them misleading information based on their party affiliation.”
To mitigate such risks, Fowler advises organizations managing sensitive documents in multiple databases to use unique formats and names that are not easily guessable. He also recommends implementing access controls, encryption, and time-limited access tokens to ensure that only authorized users can access or view the documents.
“The best way to protect these documents from being publicly exposed by the URL is to use an access token to generate a unique, time-limited access token for authenticated users when they or the system requests the document,” Fowler suggested.
Fowler emphasizes that his findings are for educational purposes and to promote cybersecurity and data protection best practices. He does not imply any wrongdoing by the companies involved and acknowledges that determining detailed access information would require an internal forensic audit.
RELATED TOPICS
- UK Electoral Commission Admits Major Data Breach
- Mexico’s entire voter database (93.4 million) leaked online
- Hackers hold 19 Million California voter records for ransom
- Sensitive Data of 123 Million American Households Exposed
- Ticketmaster Data Breach: Hackers Selling 560M Users Data