Watch out for the new CHAVECLOAK banking Trojan as it spreads its infection through SMS phishing (SMishing), phishing emails, and compromised websites.
Cybersecurity researchers at FortiGuard Labs have discovered a high-severity Trojan, dubbed CHAVECLOAK, targeting Brazilian banking users. The malware targets Windows devices and accesses online banking platforms, stealing their banking credentials and financial information.
The CHAVECLOAK infection method is under investigation, but researchers suspect potential distribution channels include phishing emails, SMS phishing, and compromised websites.
According to the company’s blog post, the campaign involves malicious emails disguised as legitimate bank communications that could trick users into downloading malware. It then targets unsuspecting users utilising Portuguese language settings, DLL sideloading, and deceptive pop-ups. It actively monitors victims’ interactions with financial portals.
It is worth motioning that DLL sideloading poses a huge security risk because it allows the malware to exploit legitimate processes without raising suspicion or getting detected.
The malware controls victims’ devices and collects sensitive financial information through a malicious PDF file, claiming to contain contract documents with Portuguese instructions. However, it has a malicious downloader link, which is processed via Goo.su and redirects to a ZIP file, resulting in the MSI file “NotafiscalGFGJKHKHGUURTURTF345.msi.”
When decompressed, the MSI installer revealed multiple TXT files, a legitimate execution file, and a malicious DLL named “Lightshot.dll.” The DLL file’s modified date is more recent than the other files. The installer executes the file “Lightshot.exe” and uses DLL sideloading techniques to execute the malicious DLL. This lets the legitimate executable run the malicious code discreetly, enabling unauthorized activities like data theft.
Additionally, the malware uses the “GetVolumeInformationW” process to gather file system and volume information, generates a log file, and executes the “Lightshot.exe” program upon user login. It sends HTTP requests, logs data, and monitors the foreground window using the APIs “GetForegroundWindow” and “GetWindowTextW.”
The malware then communicates with its C2 server, facilitating actions to steal a victim’s credentials, blocking their screen, logging keystrokes, and displaying deceptive pop-up windows.
Further, it actively monitors access to financial portals, including Mercado Bitcoin, the largest digital currency exchange in Brazil and Latin America, which combines conventional and cryptocurrency platforms and traditional banks.
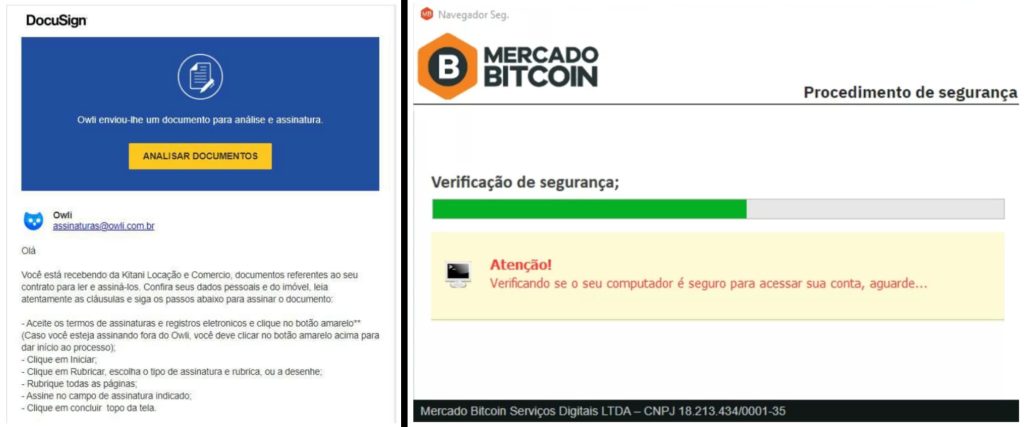
The stolen information is uploaded to different paths. The malware configures account information and sends a POST request. The malware actively monitors victims’ interactions with financial portals, highlighting the sophistication of contemporary banking trojans.
To protect yourself from CHAVECLOAK and similar banking trojans, be cautious with emails and SMS, verify website legitimacy, enable two-factor authentication (2FA), use strong passwords, and regularly update your operating system, web browser, and security software to address known vulnerabilities. Avoid clicking on suspicious links or attachments, and double-check website URLs for typos or minor variations.
RELATED TOPICS
- TA544 threat actors hit Italian firms with Ursnif banking trojan
- New MaliBot Android Malware Found Stealing Personal, Banking Data
- European Banking Authority victim in Microsoft Exchange Server hack
- Android Banking Malware FjordPhantom Steals Funds Via Virtualization
- SpyNote Spyware Returns with SMS Phishing Against Banking Customers
