A new malware threat called Zhong Stealer has surfaced from China, and it’s already slipping into businesses through an unexpected entry point – customer support chats. This info-stealing malware is currently infiltrating fintech companies by exploiting support agents, but the bigger concern is its adaptability.
Zhong Stealer can easily be repurposed to target any industry that relies on customer support teams – hospitality, healthcare, retail, and beyond. If your business has a customer-facing team, it could easily be the next target.
Let’s take a closer look at how this malware operates and what businesses can do to stop future attacks before they escalate.
How Zhong Stealer Works
Cybercriminals behind Zhong Stealer don’t rely on complex exploits or high-tech hacking tools to break into businesses. Instead, they use a low-effort but highly effective scam that plays on human nature: urgency, confusion, and frustration.
As noted by ANY.RUN researchers, the attack unfolds in a calculated, repetitive pattern designed to wear down customer support agents:
- A new support ticket appears but the sender’s account is brand new and completely empty. There’s no history, no past interactions, just a vague request for help.
- The attacker types in broken language, usually Chinese, making the conversation difficult to follow. This adds an element of confusion and makes the request seem more urgent.
- A ZIP file is attached, supposedly containing screenshots or other necessary details for the request. The attacker insists the support agent must open it to understand the issue.
- If the agent hesitates, the attacker becomes increasingly frustrated, pressuring them to act.
Running Zhong Stealer in a secure and isolated environment, such as the ANY.RUN sandbox revealed its behaviour almost immediately. View the sandbox analysis here: Sandbox session with Zhong Stealer
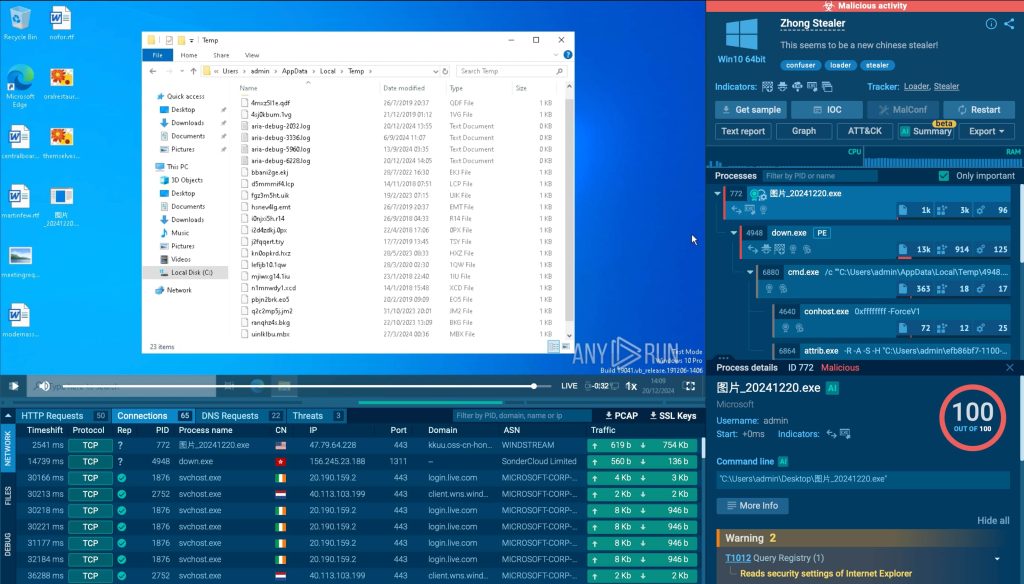
After running the analysis, we can see in the upper-right corner of the screen that the ANY.RUN sandbox immediately flagged the file and its activities as malicious, highlighting it in red.
This allows security teams to instantly recognize threats without needing deep technical expertise – the fastest and simplest way to determine if a suspicious file or link contains malware.
| Give your team the power to identify and stop cyber threats before they spread. Sign up for a 14-day free trial with ANY.RUN today! Start Your Free Trial |
During the analysis session, we can also see how Zhong Stealer downloads additional components to continue the attack:
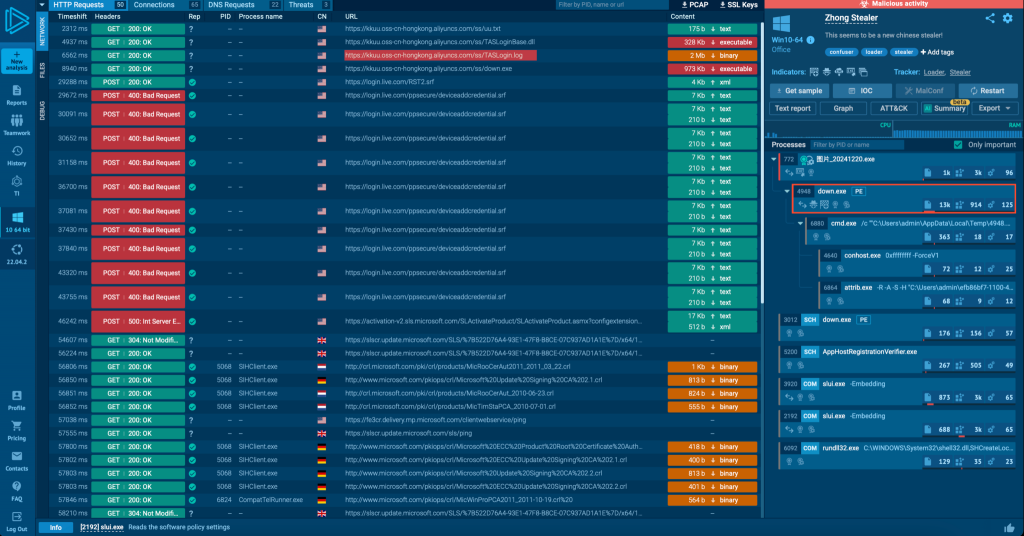
After all the preparations, Zhong Stealer starts with credentials theft and data exfiltration. By clicking on the malicious behaviour inside ANY.RUN’s sandbox we can see all the main techniques and tactics used by Zhong Stealer.
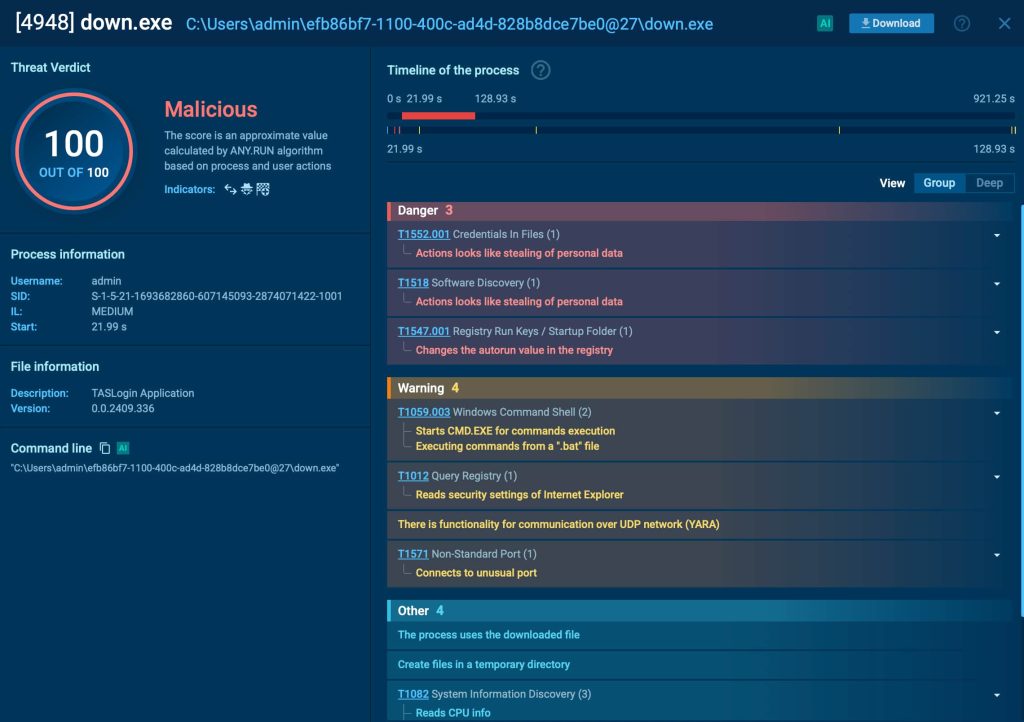
From this analysis, we can see how Zhong Stealer maintains persistence on an infected system. Its primary method is adding a registry key to make sure that the malware automatically runs every time the system starts.
If the registry entry is removed, Zhong has a backup plan: it uses a scheduled task to relaunch itself, making it harder to fully eliminate.
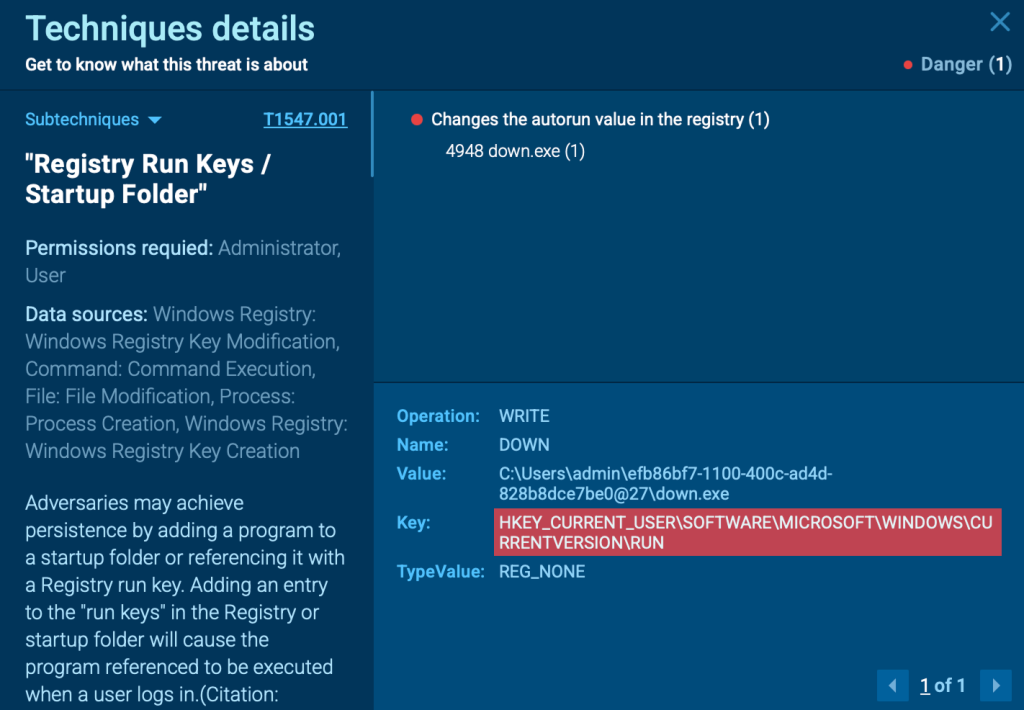
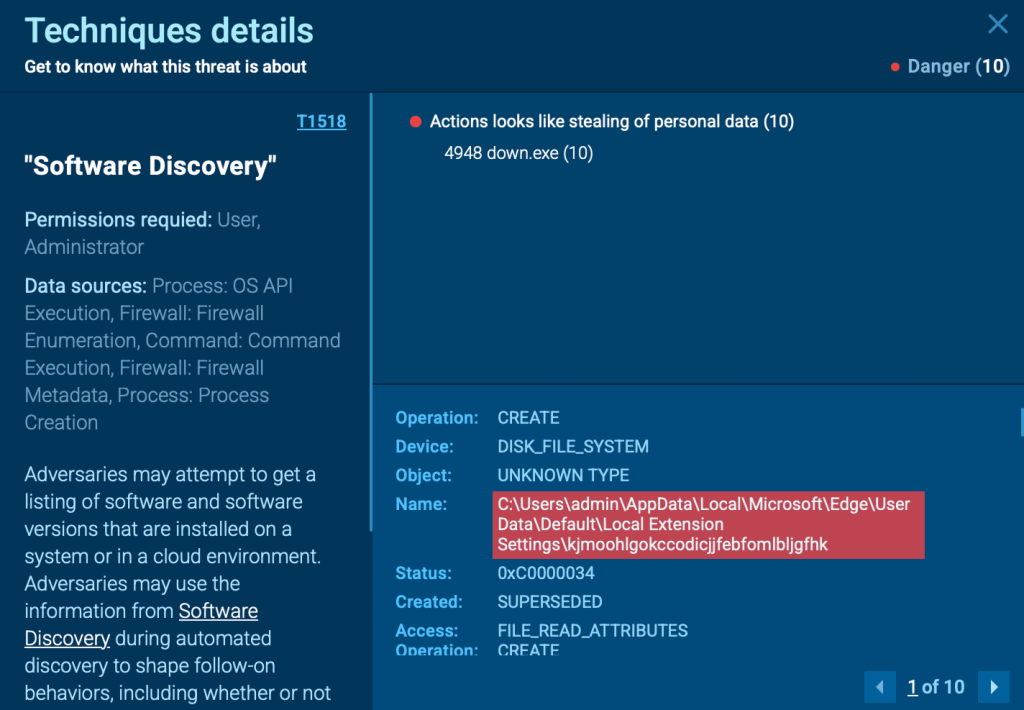
Once persistence is secured, Zhong shifts its focus to the real goal: harvesting credentials and browser extension data.
By targeting stored login information, it can steal sensitive business and personal data before the victim even realizes they’ve been compromised.
Finally, after stealing sensitive data, Zhong connects to its command-and-control (C2) server in Hong Kong to send the stolen information back to the attackers.
How to Protect Your Business from Zhong Stealer
Zhong Stealer proves that malware can slip into businesses through unexpected channels, like customer support chats.
The easiest way to check whether a file is malicious is to analyze it with tools like ANY.RUN sandbox. Thanks to its user-friendly interface, anyone can use it, even without technical expertise, making it a great solution for all team members.
Simply upload the file into the secure sandbox environment, run the analysis, and see the verdict. If malicious activity is detected, the file should be reported immediately.
You can also download a well-structured report containing all the attack details, making it easier to share findings with security teams, IT staff, or decision-makers.
With ANY.RUN, businesses can:
- Quickly analyze suspicious files and links in a safe, controlled environment without risk to internal systems.
- See real-time malware behavior, including persistence techniques, data theft attempts, and communication with external servers.
- Identify threats instantly, with flagged malicious activity highlighted for easy recognition.
- Prevent infections before they happen by proactively checking files before employees open them.



