Blackpoint Cyber discovered a new Fake CAPTCHA campaign that tricks users into installing Amatera Stealer. By abusing legitimate Microsoft scripts and hiding malicious code in Google Calendar and PNG images, this attack bypasses standard security to harvest private passwords and browser data.
On Friday, January 23, 2026, the cyber threat monitoring firm Blackpoint Cyber revealed a clever new way that hackers are tricking people into infecting their own computers. This latest scheme uses a fake “I am not a robot” check to bypass security and install a data-stealing program called Amatera Stealer.
How the Trap Works
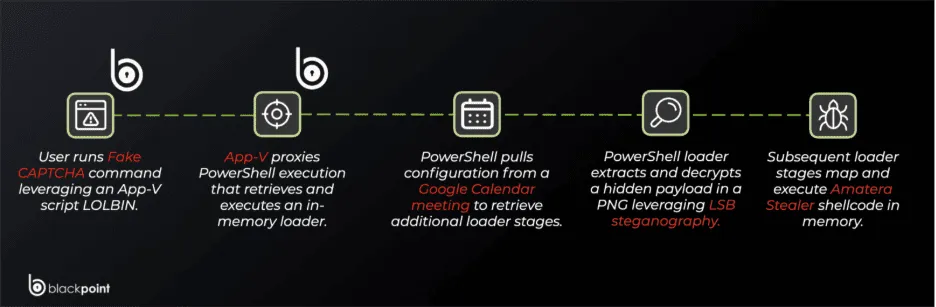
Most of us are used to clicking boxes or identifying traffic lights to prove we are human. However, this attack uses a Fake CAPTCHA, Blackpoint Cyber’s researchers explained in the blog post shared with Hackread.com. Instead of a simple click, the website asks the user to perform keyboard shortcuts like pressing the Windows Key + R, then pasting a code and hitting Enter.
Report authors Jack Patrick and Sam Decker note that this isn’t just a random set of steps. By doing this, the user is unknowingly running a command that starts the infection. The hackers use a built-in Windows tool called SyncAppvPublishingServer.vbs to hide their tracks.
This is known as a LOLBin (Living Off the Land Binary), which means it is a real Microsoft script used to manage virtual apps. Because this tool is a signed, trusted part of Windows, many antivirus programs don’t realize anything bad is happening.
Hiding in Plain Sight
The attack is oddly patient because if it detects it is being watched by security sandboxes (automated testing environments) or if the user didn’t follow the steps exactly, it simply stops. It even checks your clipboard for a specific marker to prove a human actually pasted the command. If the script doesn’t find this, it enters an infinite wait state, effectively playing dead to avoid being analysed.
Researchers also found that the system actually pulls its instructions from a public Google Calendar (.ics) file. By using a trusted site like Google, the hackers make their internet traffic look normal. They also hide the actual virus inside regular-looking pictures (PNG files) hosted on public sites like Imgur.
Using a trick called steganography, they hide the malicious code in the tiny bits of pixel data. To keep researchers confused, the script even uses a decryption key named AMSI_RESULT_NOT_DETECTED, a term usually used by security software to say a file is safe.
The Final Goal: Amatera Stealer
The chain ends with the delivery of Amatera Stealer, a virus designed to grab saved passwords, credit card info, and browser data. It even tries to hide its internet traffic by pretending to connect to common sites like microsoft.com or facebook.com.
It is also important to remember that this specific trick only works on modern Windows 10, 11, or Server editions that have App-V features enabled. If you have a basic Home version of Windows, the attack will likely fail.
Blackpoint Cyber researchers conclude that the real danger is how the hackers live off someone else’s infrastructure to avoid being caught. To stay safe, they suggest never copying and pasting commands from a website into your computer’s Run box.