A recent investigation by researchers at Check Point Harmony Email Security uncovered a clever new phishing scam targeting businesses worldwide. Over the last 14 days, it was found that cybercriminals have been abusing Google’s own automated systems to send out thousands of malicious emails that look 100% official.
How the Attack works
According to Check Point’s report, this newly discovered campaign uses a tool called Google Cloud Application Integration. This service is normally used by companies to set up workflow automation, like sending automatic alerts. However, scammers have found a way to use this feature to send emails directly from a legitimate Google address: [email protected].
Because the emails come from a real Google domain, they easily bypass traditional security filters. Probing further, researchers found that the messages usually look like standard office notifications, claiming you have a new voicemail or need to view a “Q4” file. As we know it, such content makes the emails look like “routine enterprise notifications,” which is why so many people trust them.
A Three-Step Trap
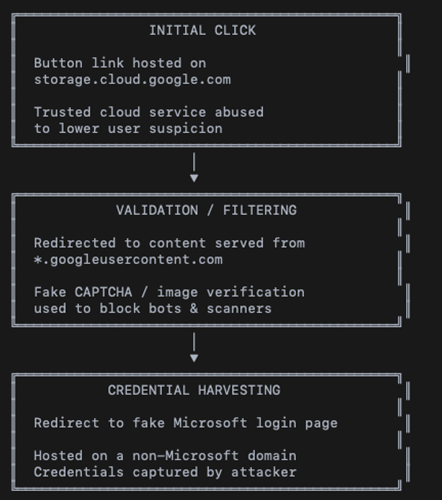
The scammers use a multi-stage process to steal information. It begins when a user clicks a link or button pointing to a real Google Cloud page (storage.cloud.google.com). From there, they are sent to a second page (googleusercontent.com) showing a fake CAPTCHA test.
Researchers noted this is done to block security tools while letting real people through. Finally, the user is sent to a fake Microsoft login page for credential harvesting, which is a simple way of saying the scammers record your password the moment you type it.
Who is Being Targeted?
Researchers observed that the campaign is truly global. While 48.6% of the targets were in the United States, there was significant activity in Asia-Pacific (20.7%) and Europe (19.8%). In Latin America, Brazil (41%) and Mexico (26%) saw the most hits within that region. It is worth noting that the manufacturing and technology sectors were the biggest targets, at 19.6% and 18.9% respectively, followed by finance and banking at 14.8%.
In total, 9,394 phishing emails were sent to approximately 3,200 customers in just two weeks. Google has since stated that this “activity stemmed from the abuse of a workflow automation tool, not a compromise of Google’s infrastructure.”
While the company has confirmed these specific campaigns are now blocked, this incident reminds us all to remain cautious of any unexpected links, even when they appear to come from a trusted source.
