A new variant of the notorious Adload malware has been discovered to bypass the latest updates to Apple’s built-in antivirus, XProtect.
Despite Apple’s efforts to fortify its defenses with a significant update to its malware signature list, Adload’s authors have swiftly adapted, rendering these new measures ineffective against the latest iterations of the malware.
Apple’s Massive Adload Signature Update
Apple’s security team recently implemented a substantial update to XProtect, adding 74 new rules in version 2192 and 10 additional rules in version 2193, released on April 30th.
This update aimed to combat the Adload adware, which has been a persistent threat to macOS devices.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
According to the recent report by SentinelOne, a new strain of Adload malware has been discovered that is capable of bypassing the built-in antivirus detection of macOS, posing a significant threat to the security of Mac systems.
Before this update, XProtect had 207 rules, of which a significant portion targeted historical versions of Adload.
The update marked a 24% increase in the rule count, showcasing Apple’s commitment to combating this pervasive adware.
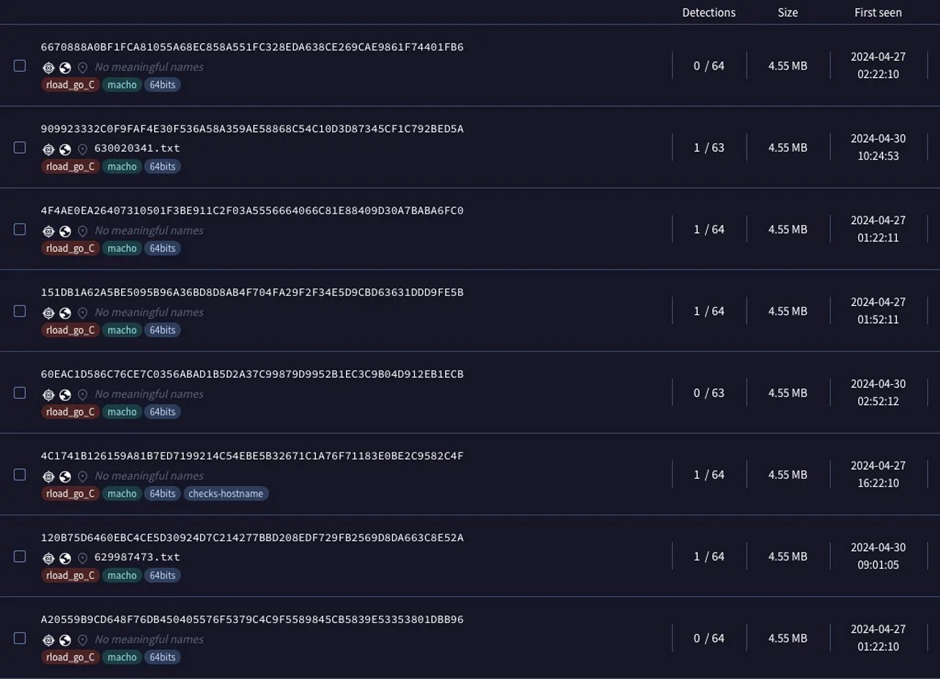
Despite these efforts, new versions of Adload have been identified, evading detection by both XProtect and other antivirus engines on VirusTotal.
This development underscores malware authors’ adaptability and the challenges faced by security teams in keeping up with evolving threats.
The latest Adload samples have shown an alarming ability to bypass detection mechanisms. Initially, various antivirus engines detected many of these samples.
However, as the week progressed, samples began to surface that eluded XProtect and other vendors’ detection on VirusTotal.
This evasion highlights the sophistication of the new Adload variants and the need for continuous vigilance and updates from security providers.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free.
New Adload Go Variant (Reload/Lador)
Among the new variants, one in particular, compiled solely for the Intel x86_64 architecture, has demonstrated a near-total detection evasion, with 0 or only 1 detection among VirusTotal engines.
This variant acts as an initial dropper for the next stage payload, with no clear parent executable, application, or disk image, suggesting a distribution through cracked or trojanized apps.
The samples observed embed a unique custom domain, following known Adload patterns, indicating a sophisticated and organized distribution method.
| SHA1 | Domain |
| 13312b3dad9633fa185351e28397c21415d95125 | api[.]deployquest[.]com |
| 21c447cac1c13a6804e52f216a4c41a20c963c01 | api[.]searchwebmesh[.]com |
| 5b1d60c6f461cd8ba91cbca5c7190f4b2752979d | api[.]generalmodules[.]com |
| 67a56aa269b9301981c0538ace75bec2cd381656 | api[.]validexplorer[.]com |
| 7aaff54d2d6e3f38e51a4f084e17b9aad79a9de0 | api[.]operativeeng[.]com |
| 912a2ab06d3afe89e8e2ad19d3300055f0e0a968 | api[.]buffermanager[.]com |
| a99d03fc3b32742de6688274a3ee3cdaef0172bf | api[.]lookwebresults[.]com |
| f166eb63162ce4a5ac169e01c160be98b0e27e13 | api[.]navigationbuffer[.]com |
| feb2c674f135410c3ced05c301f19ab461e37b20 | api[.]inetprogress[.]com |
Upon execution, these droppers perform system information discovery via the ioreg utility:
ioreg -rd1 -c IOPlatformExpertDevice
The malware then seeks to resolve a hardcoded domain name, sym._main.dwnldUrl, and sends an http request to retrieve a remote gzip.
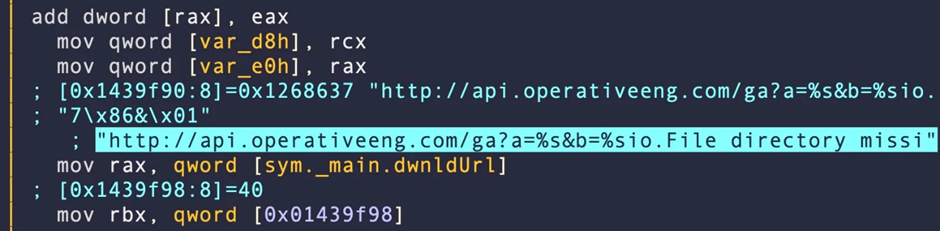
Minor Tweak Evades XProtect Signature Rule
A closer examination of the binaries reveals that despite Apple’s targeted efforts, the malware authors have managed to evade detection by making minor adjustments, such as replacing the string main.DownloadURL with main.dwnldUrl.
rule macos_smolgolf_adload_dropper
{
meta:
description = "MACOS.ADLOAD"
strings:
$varName = "main.DownloadURL"
$libraryName = "github.com/denisbrodbeck/machineid.ID"
$execCommand = "os/exec.Command"
condition:
Macho and all of them
}This subtle change has allowed the latest Adload samples to slip past XProtect’s defenses, underscoring the ongoing cat-and-mouse game between malware authors and security teams.
As the battle against malware like Adload continues, it is clear that reliance on built-in antivirus solutions alone may not suffice.
Enterprises and individual users are encouraged to consider third-party security solutions to ensure comprehensive protection against these and other sophisticated threats.
For those concerned about the security of their macOS devices, exploring additional security measures and staying informed about the latest threats and detection strategies is more crucial than ever.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide