Cybersecurity researchers have discovered a new, highly dangerous Android banking malware called Sturnus, named after the common starling or ‘songbird’ because of its complex and ‘chaotic’ communication style.
The Dutch cybersecurity firm ThreatFabric identified this privately-operated threat, which has features that are simply far more advanced and dangerous than what we’ve seen before.
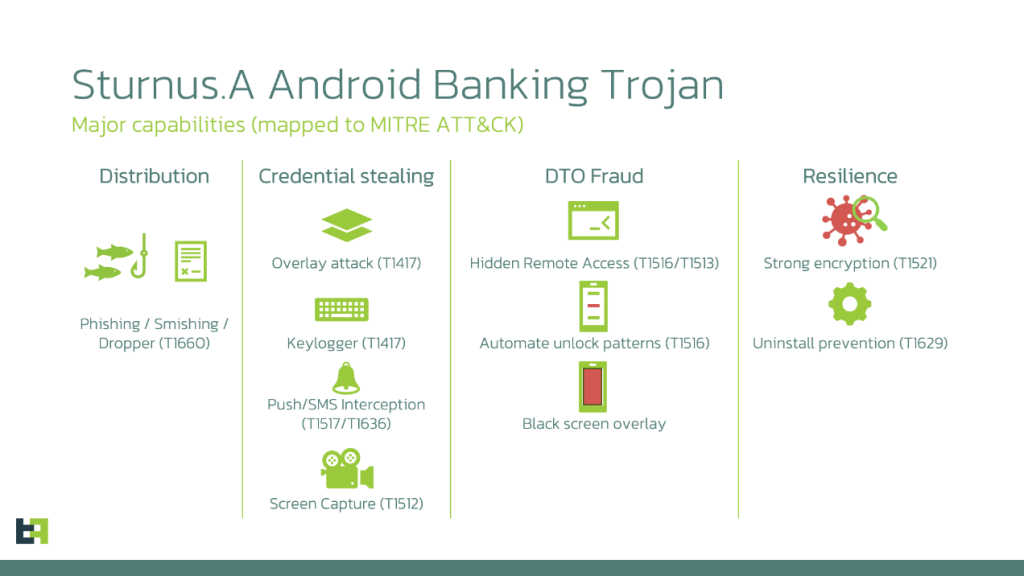
According to ThreatFabric’s blog post, published on November 20, 2025, Sturnus is far more advanced than previous malware, capable of stealing your bank details, able to view chat content on apps like WhatsApp, Telegram, and Signal by abusing Android’s Accessibility Service
How it Decodes Your ‘Encrypted’ Chats
Even though these apps use end-to-end encryption, which means only you and the person you’re chatting with can read the messages, Sturnus completely gets around this protection. It works by relying on the Android Accessibility Service to read the message content directly from the screen after the legitimate app has decrypted it. This means the attackers can see full conversations, contacts, and all incoming and outgoing messages in real time.
A Fully Featured Threat
The malware is distributed through social engineering campaigns, including Phishing (email), Smishing (SMS text messages), or via a malicious Dropper application, which tricks users into installing the final malware as an unofficial APK file
Once Sturnus infects a phone, it uses two integrated methods to steal sensitive data: deploying fake login screens, known as HTML overlays, that perfectly mimic banking apps; and simultaneously employing a comprehensive keylogging pipeline via the Accessibility Service to record every keystroke and screen tap.
Further probing revealed that the malware gives the attackers extensive remote control. They can type, monitor all activity, and, most disturbingly, display a black screen overlay to hide their actions while it silently executes fraudulent transactions in the background. The malware even uses its keylogging ability to steal PINs and Passwords, making it easy to unlock the device itself.
The Attack Status and Targets
It is worth noting that Sturnus is highly persistent. It gains special privileges on the phone, called Device Administrator rights, and actively protects them. If a user tries to disable these rights or uninstall the malware in settings, Sturnus detects the attempt and automatically stops the action. This defence makes it very difficult to get rid of it once installed.
Researchers assess that although this malware is not yet widespread and is currently in an early testing phase, it is already fully functional. Its configurations show an immediate focus on targeting financial institutions across Southern and Central Europe. This concentration on high-value apps and specific regions suggests the criminals are simply getting ready for a much larger, more coordinated global attack.
Expert Commentary
In commentary shared exclusively with Hackread.com, Aditya Sood, VP of Security Engineering and AI Strategy at Aryaka, provided insight into the malware’s technical edge and broader risks.
“Sturnus poses a different kind of threat compared to other Android malware due to its ability to use a mix of plaintext, RSA, and AES-encrypted communication with the C2 server it responds to,” Sood said.
“The combination of these three allows Sturnus to blend more easily into normal network patterns, while also hiding commands and stolen data from defence systems. This advanced level of evasion and resilience from the malware disrupts signature-based detection and can impede reverse-engineering efforts, making it harder to inspect Sturnus’ network traffic or recover the contents that it steals.”
Sood also highlighted the risk to organisations: “As a banking trojan, Sturnus is primarily targeting financial organisations. However, the ability to steal messages from end-to-end encrypted platforms like Signal could spell serious problems for organisations, as those applications are used across several industries to secure sensitive or confidential information.”
He advises, “Individuals who are at-risk, or who are in control of sensitive information, must avoid downloading APK files from outside Google Play, and should continuously monitor for malicious activity if infection is suspected.”
